Protect your SSH Keys before it becomes a security liability.
Poor SSH key tracking causes key sprawl, lost keys, and security gaps that increase the risk of unauthorized access. QCecuring’s SSH Key Management helps you organize and secure all SSH keys, reducing exposure and strengthening system protection.
SSH Key Management
Centralized SSH key inventory with comprehensive scanning, reporting, and access control capabilities to prevent key sprawl and unauthorized access.
The Problem
SSH Key sprawl happens when keys are not tracked properly when number of remote machines increases. One leaked key enables attacker to open backdoor and to SSH into across various remote machines through encrypted channel without being detected.
- Key Sprawl Risk: Untracked SSH keys across multiple machines create security vulnerabilities and access risks.
- Unauthorized Access: Leaked keys enable attackers to gain encrypted access to multiple systems undetected.
The Solution
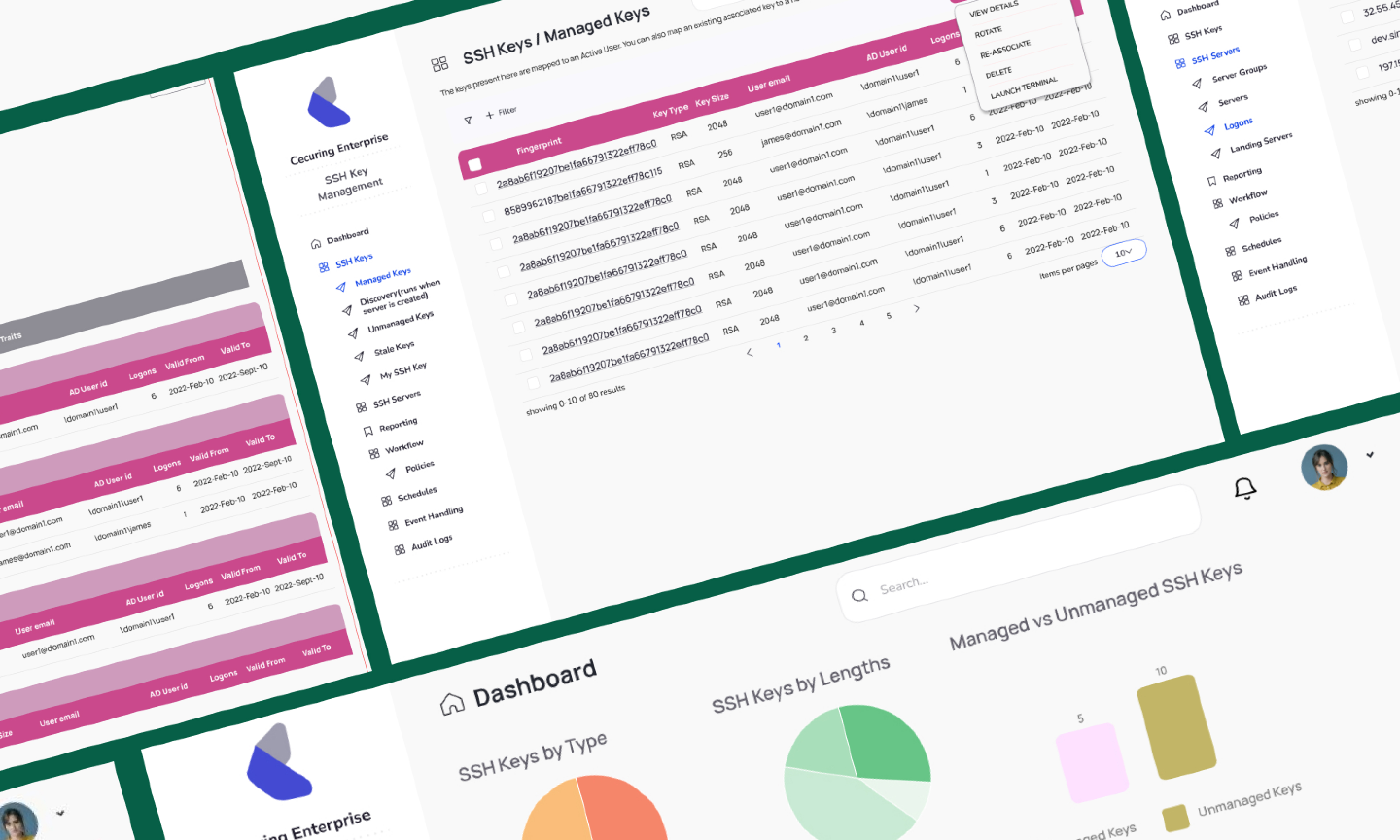
QCecuring's SSH Key Management component helps an enterprise to prevent Key sprawl and track every SSH Key effectively inside a centralized place. It scans your remote SSH Server machine, brings every public key inside all user accounts to a centralized inventory, where you associate them to a new user. You can generate various reports, view dashboard charts.
- Centralized Inventory: Single place to view, manage, and track all SSH keys across your organization.
- Automated Scanning: Automatically scan remote machines to discover and inventory SSH keys for centralized management.
Core Features
Comprehensive SSH key management with centralized inventory, automated scanning, and advanced reporting
Chart Based Statistics
View Charts and list SSH keys based on chart selection.
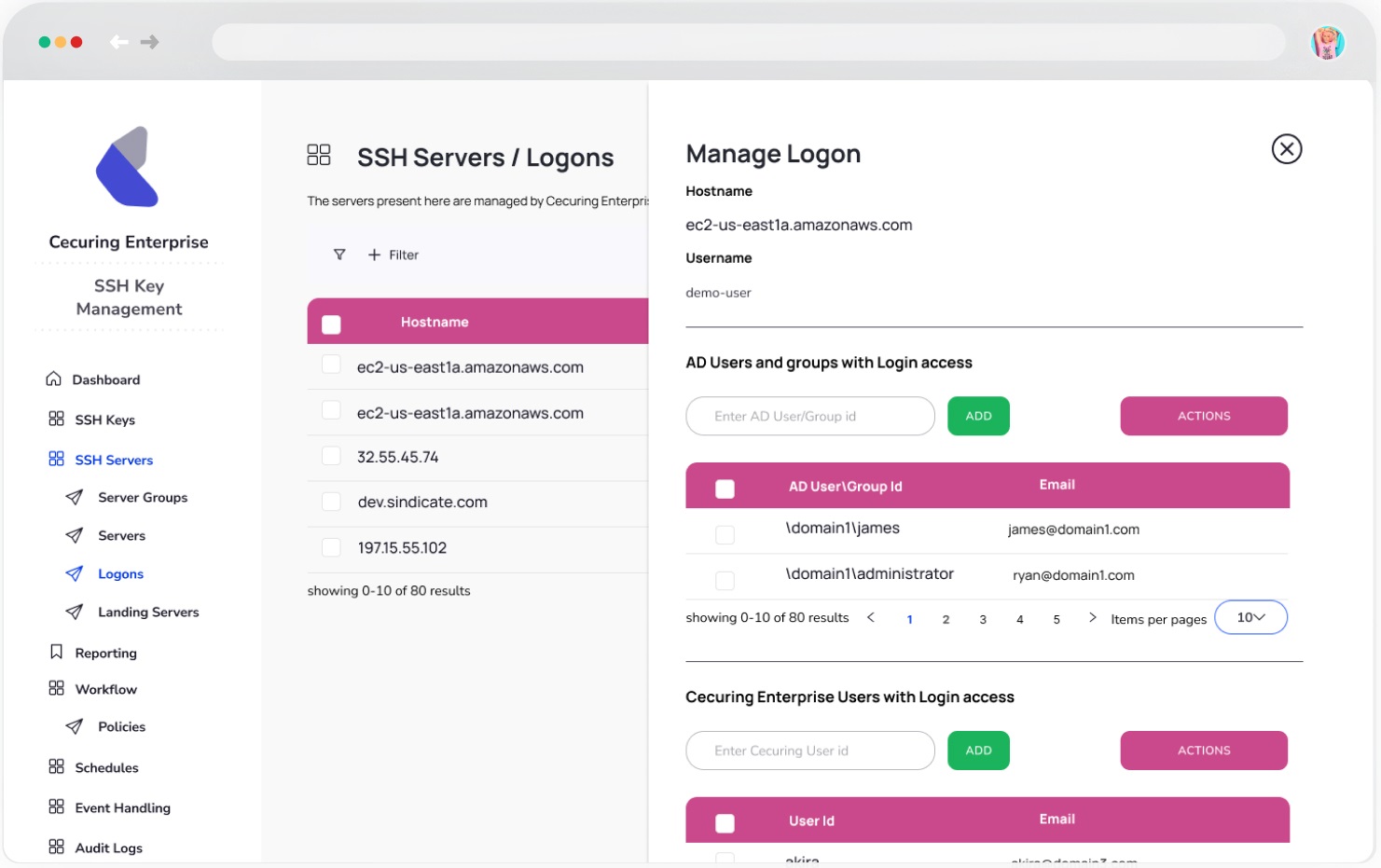
Centralized SSH Key Inventory
A Single place to view all of your SSH Key, view complete details, reassociate them to new users delete them altogether from the system.
SSH Server Scanning
You can configure a Remote machine, our component will scan its user accounts to find the public keys present and gather them inside a centralized place for further processing.
Reporting Capabilities
With access to 11+ Reports, you can gather various metrices and see their corresponding SSH Keys very easily. Not only this Every report provides you the ability to export it as PDF and as Excel document. If you want automation over this too, then Scheduling capability allows you to create schedule to deliver these reports on timely basis.
AD Integration
The application Integrates with Active Directory (AD) seemlessly, adding a user in Logons via AD user addition will automatically provide that user access to concerned remote machine.
Event Handlers
Application is designed to register customized handlers for predefined events like Key Expired event (means rotation is needed for the key).
Auditing Capabilities
Every operation performed inside the application is logged at the atomic level, thereby giving complete transparancy of who did what.
Ready to Secure Your Enterprise?
Experience how our cryptographic solutions simplify, centralize, and automate identity management for your entire organization.