Build Trust with Zero-Trust Architecture
Empower your enterprise with cryptographic automation and identity protection.
Foundation of Security Excellence
Comprehensive cryptographic solutions built for modern enterprises
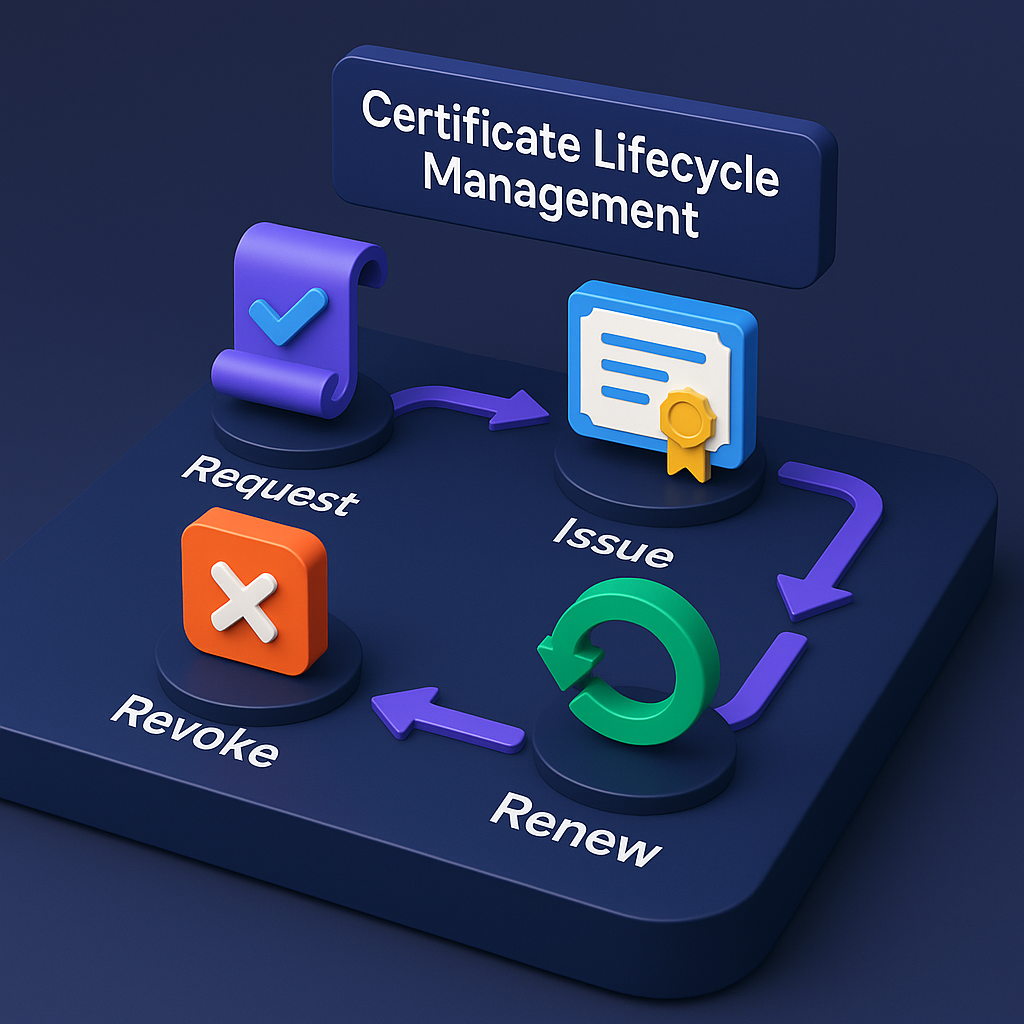
SSL Certificate Lifecycle Management
Automate certificate provisioning, renewal, and revocation across your entire infrastructure.
Prevent Key Theft
Advanced cryptographic protection to safeguard your private keys from unauthorized access.
Remediate Certificate Outages
Proactive monitoring and instant alerts to prevent certificate-related downtime.
SSH Key Management
Centralized control and visibility over SSH keys across all your systems and users.
Anywhere PKI
Deploy and manage PKI infrastructure anywhere—cloud, on-premise, or hybrid environments.
Enterprise Security Solutions
Comprehensive cryptographic infrastructure for modern enterprises
SSL Certificate Lifecycle Management
- Automate certificate issuance and renewal
- Centralized certificate inventory and tracking
- Prevent certificate-related outages
- Support for all certificate types and CAs
Code Signing
- Secure software supply chain integrity
- Enterprise-grade signing workflows
- Multi-platform code signing support
- Audit trails and compliance reporting

SSH Key Management
- Centralized SSH key lifecycle management
- Automated key rotation and revocation
- Role-based access control
- Comprehensive audit logging

HSM as a Service
- Cloud-based Hardware Security Modules
- FIPS 140-2 Level 3 compliance
- Secure key generation and storage
- Enterprise-grade cryptographic operations

PKI as a Service
- Cloud-native Public Key Infrastructure
- Automated certificate lifecycle management
- Seamless cloud platform integration
- Enterprise security and compliance

Cloud Native Machine Identity
- Kubernetes and cloud-native support
- Cert-manager integration
- Advanced monitoring and reporting
- Enterprise-scale deployments

Ports Required for Active Directory and PKI: A Complete Guide
Essential network ports and protocols for AD and PKI infrastructure. Join us to learn how to configure your firewalls correctly.
Date
March 7, 2026
Why Choose QCecuring Technologies
Enterprise-grade security solutions trusted by leading organizations
Automated Lifecycle Management
Manage thousands of certificates effortlessly with intelligent automation that eliminates manual processes and human error.
Enterprise-Grade Security
Built for scalability and compliance with industry standards including FIPS, Common Criteria, and SOC 2 Type II.
Zero-Trust Integration
Align your IT infrastructure with next-generation security frameworks and implement zero-trust architecture seamlessly.
Global Support
Trusted by enterprises worldwide with 24/7 support, comprehensive documentation, and dedicated success teams.
Recent Insights
Stay updated with the latest trends and best practices in cybersecurity
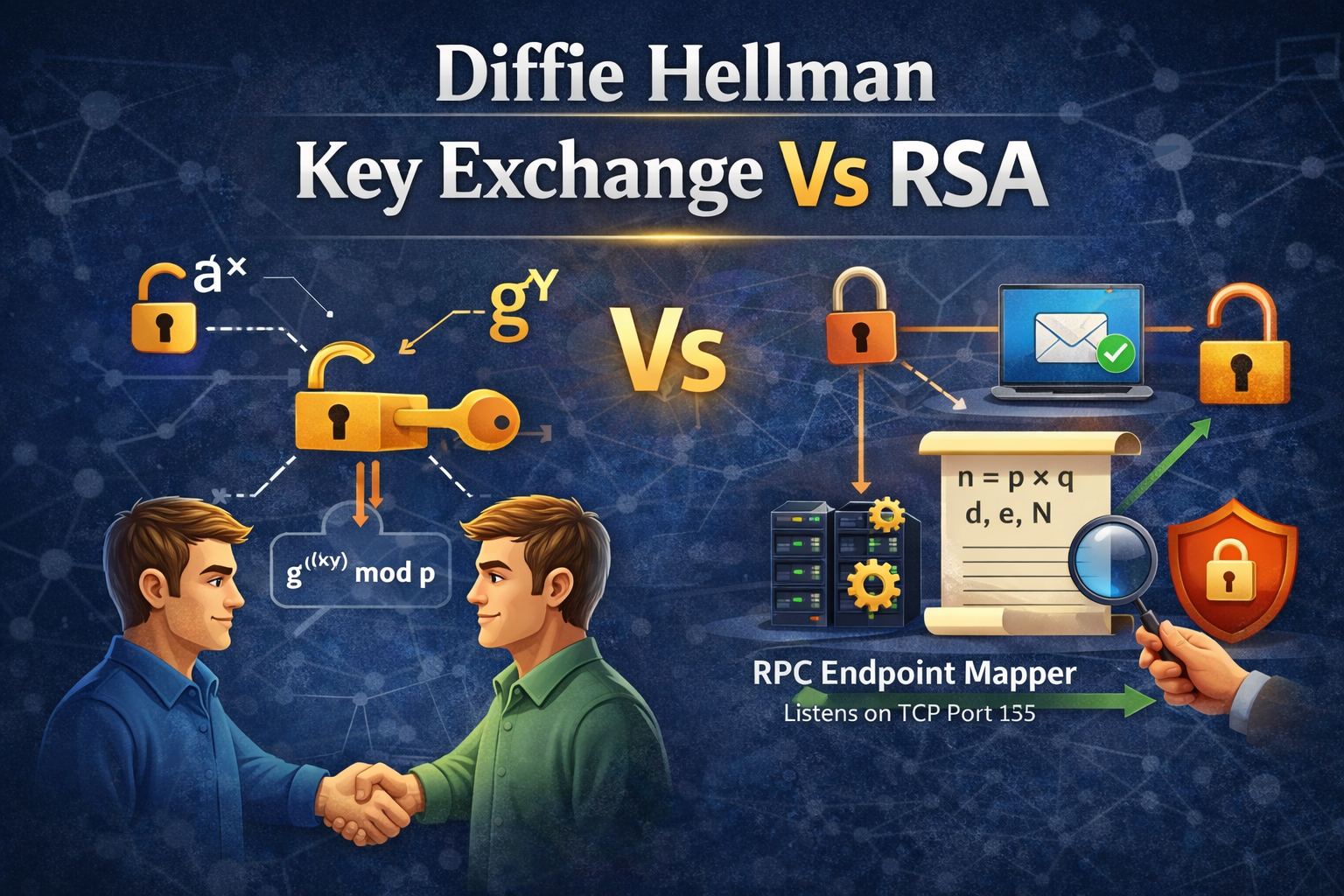
Diffie-Hellman Key Exchange vs RSA: A Modern Cryptographic Comparison
A point-by-point, enterprise-focused comparison of Diffie-Hellman Key Exchange and RSA, covering security, performance, and real-world use cases.
Read More
How To Fix The RPC Server Is Unavailable Error
Step-by-step guide to troubleshoot and fix the RPC Server Is Unavailable error in Windows systems.
Read More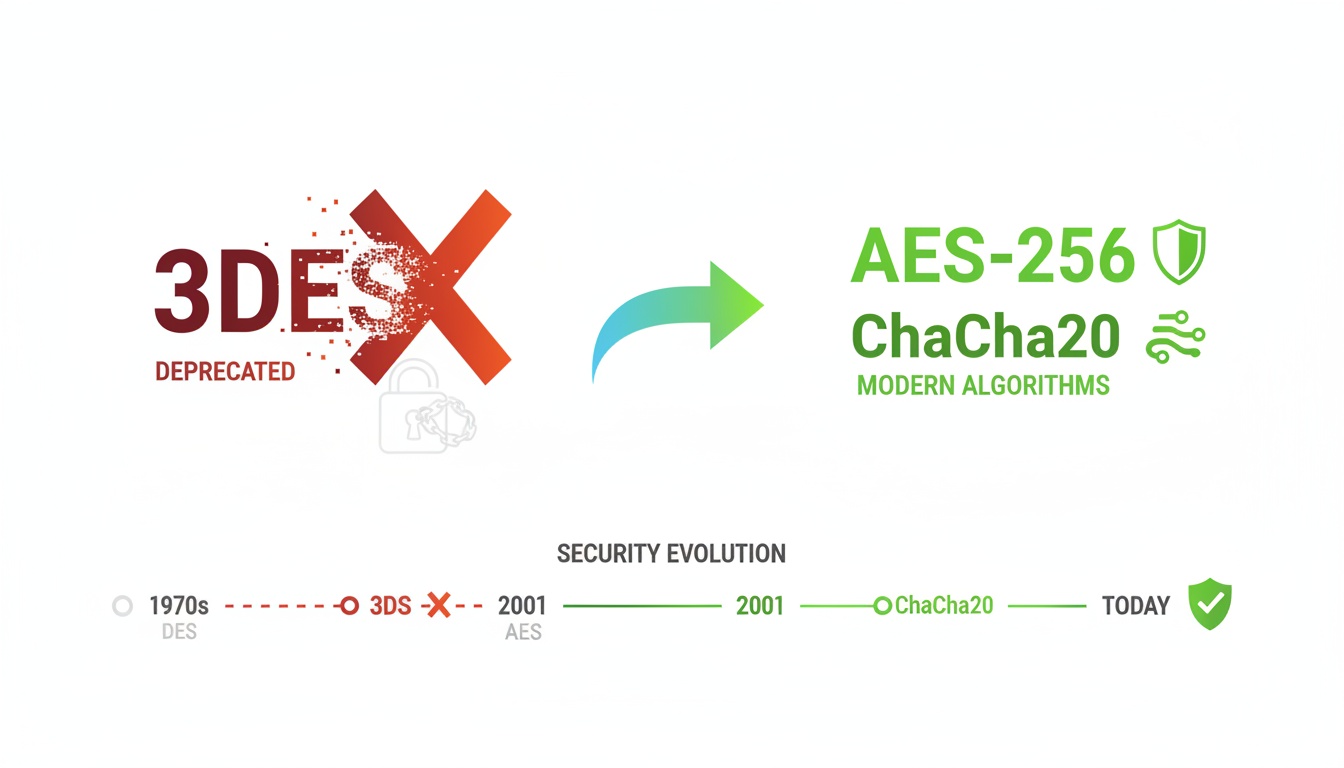
Why 3DES or Triple DES Is Officially Being Retired
Learn why 3DES (Triple DES) is being deprecated, the security weaknesses behind its retirement, and why AES is now the recommended encryption standard.
Read More
NIST SP 1800-16 Guidelines: The Enterprise Blueprint for TLS Certificate Management
A comprehensive guide to NIST SP 1800-16 guidelines for securing web transactions through automated TLS server certificate management.
Read More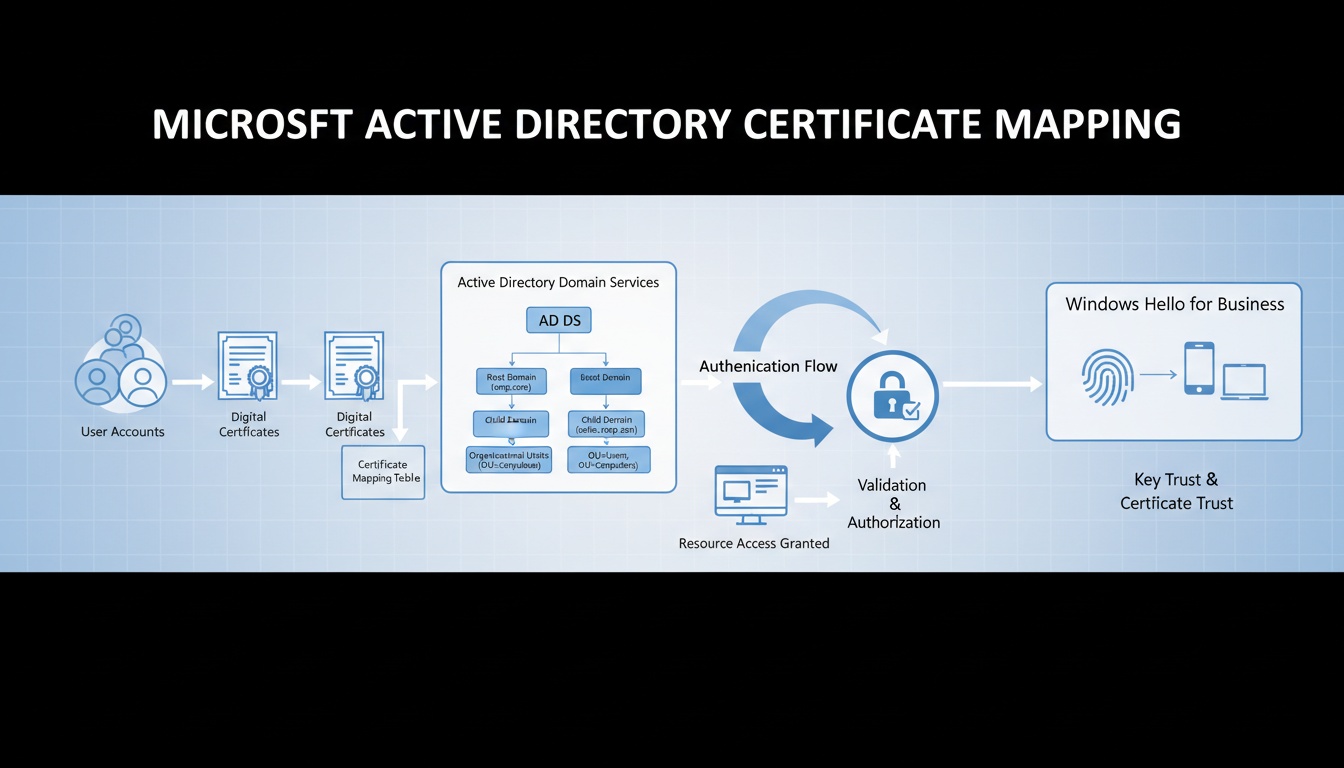
Microsoft Strong Certificate Mapping: Security, Enforcement & Enterprise Migration Guide
In-depth guide to Microsoft's Strong Certificate Mapping enforcement, SID-based mappings, registry controls, Event ID 39, PKI requirements, and enterprise migration strategies.
Read More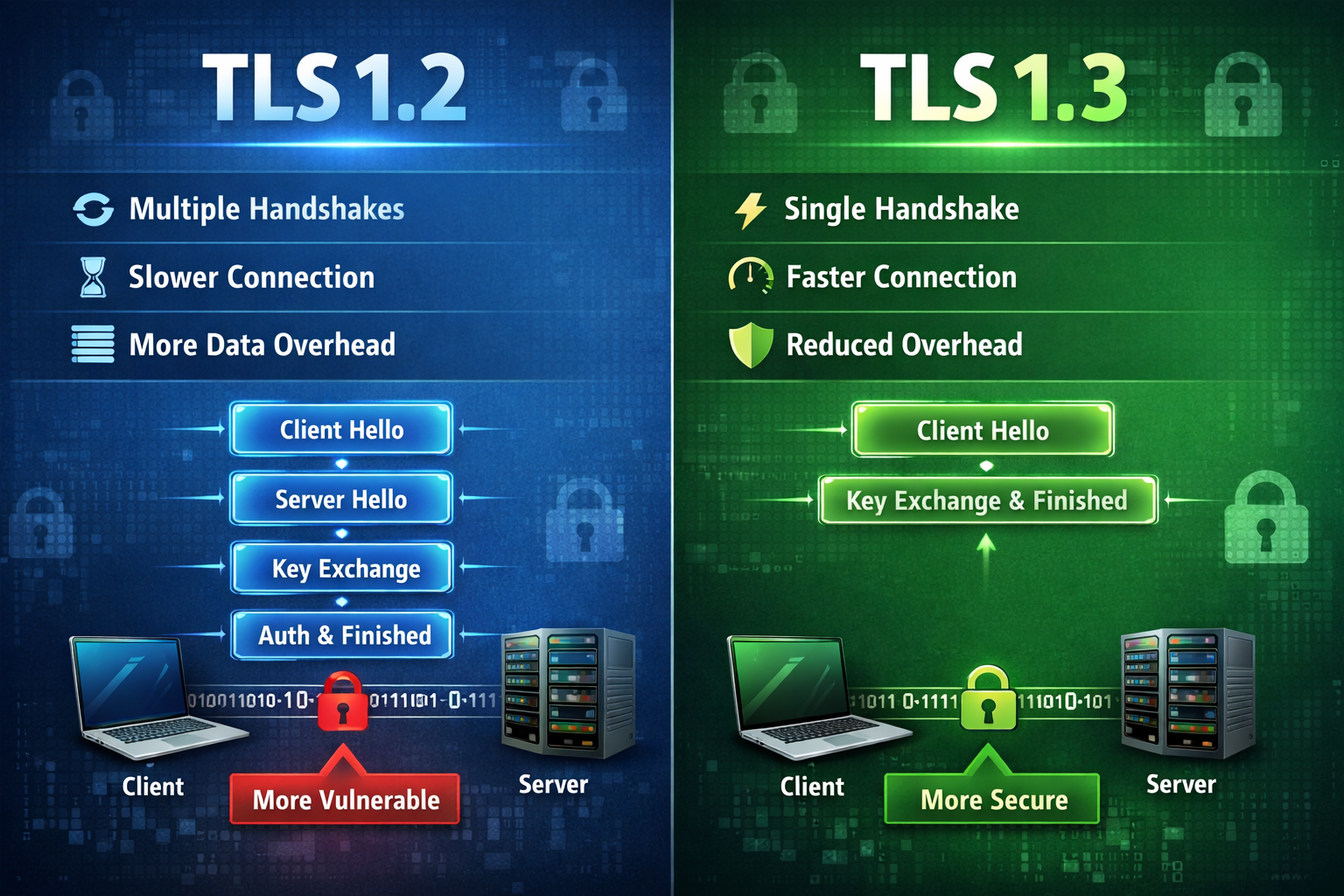
TLS 1.2 vs TLS 1.3: Security, Speed & Migration Guide
Comprehensive guide to TLS 1.3 improvements, performance gains, security enhancements, and enterprise migration strategies.
Read More← Scroll to explore more articles →
Ready to Secure Your Enterprise?
Experience how our cryptographic solutions simplify, centralize, and automate identity management for your entire organization.

