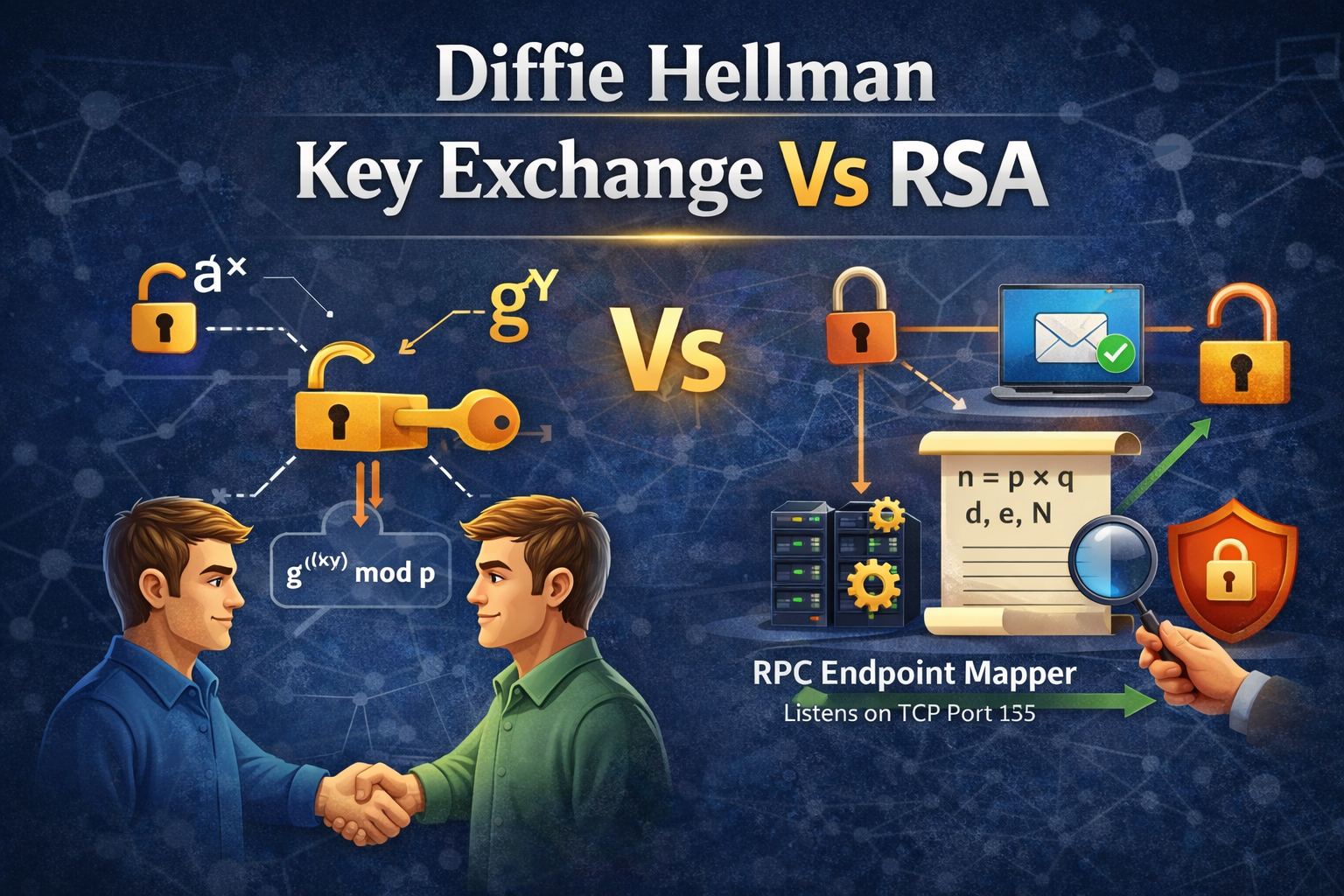
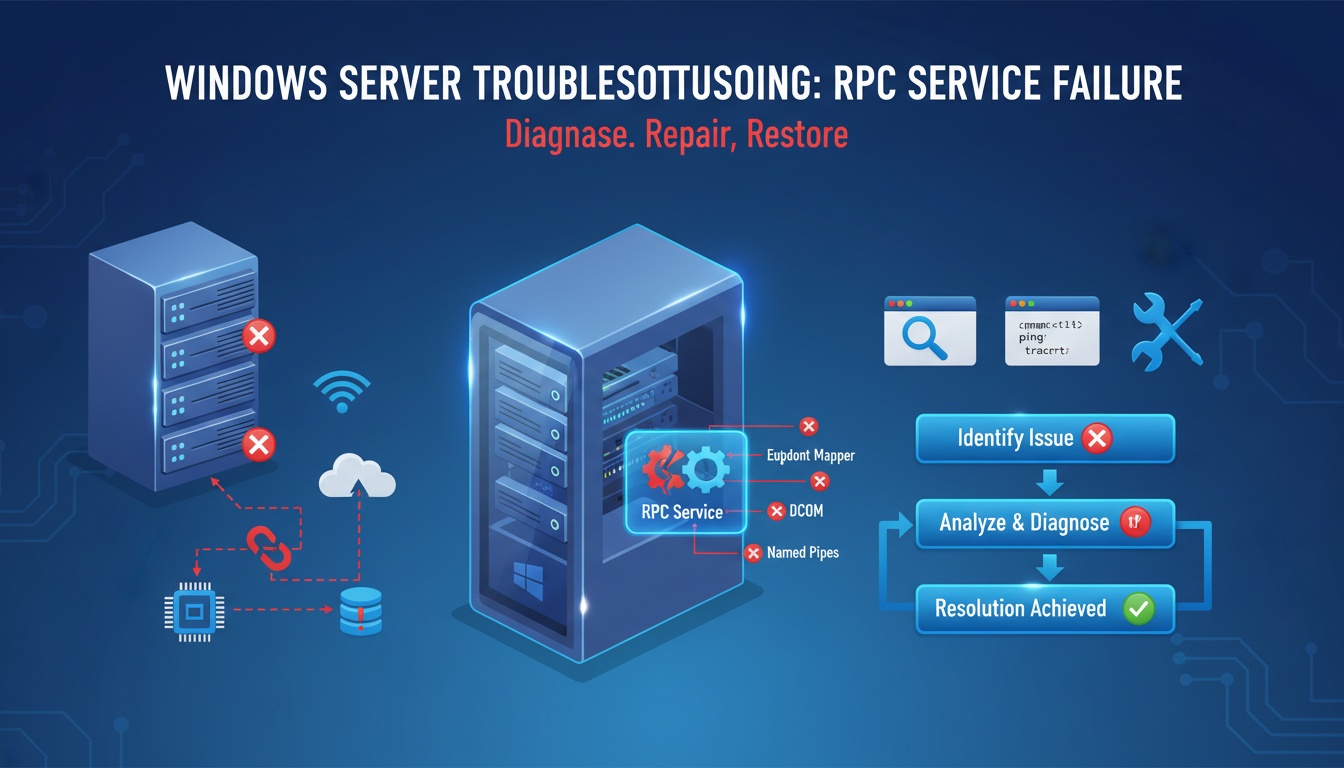
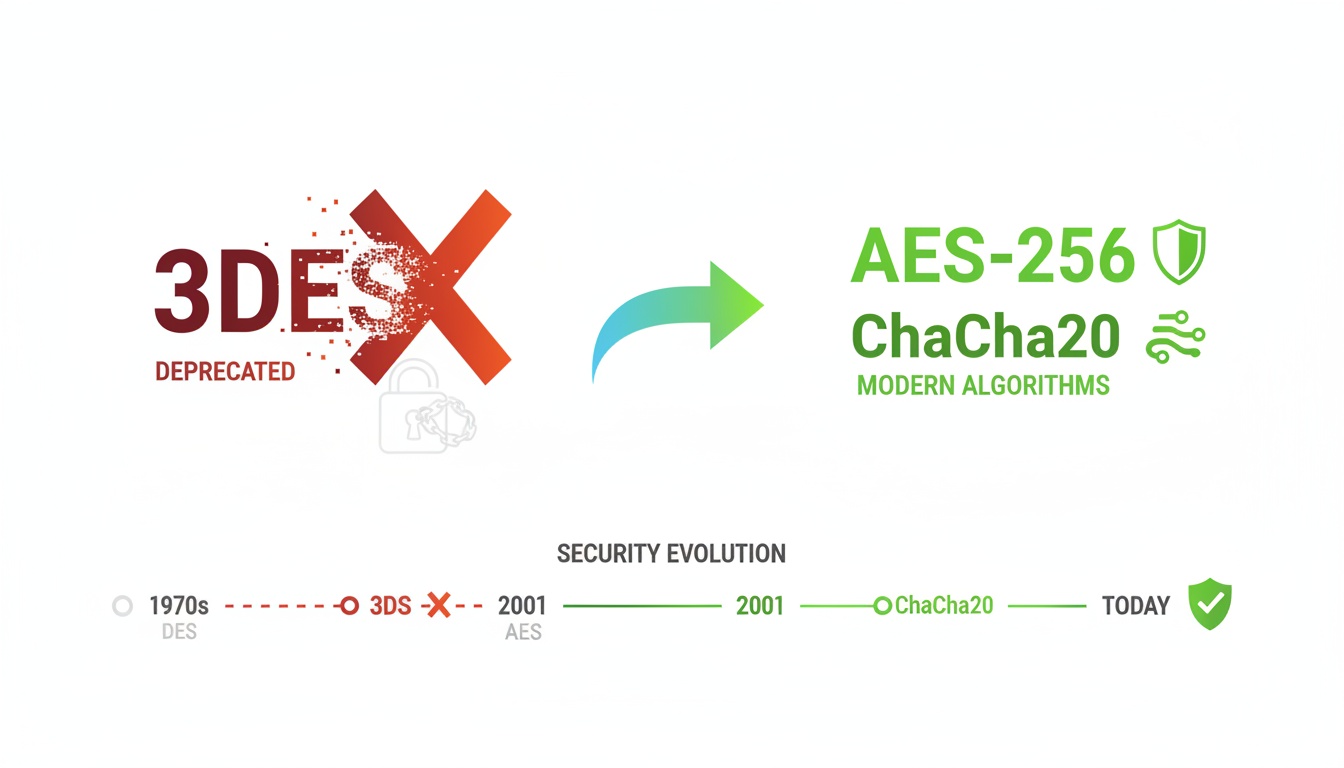
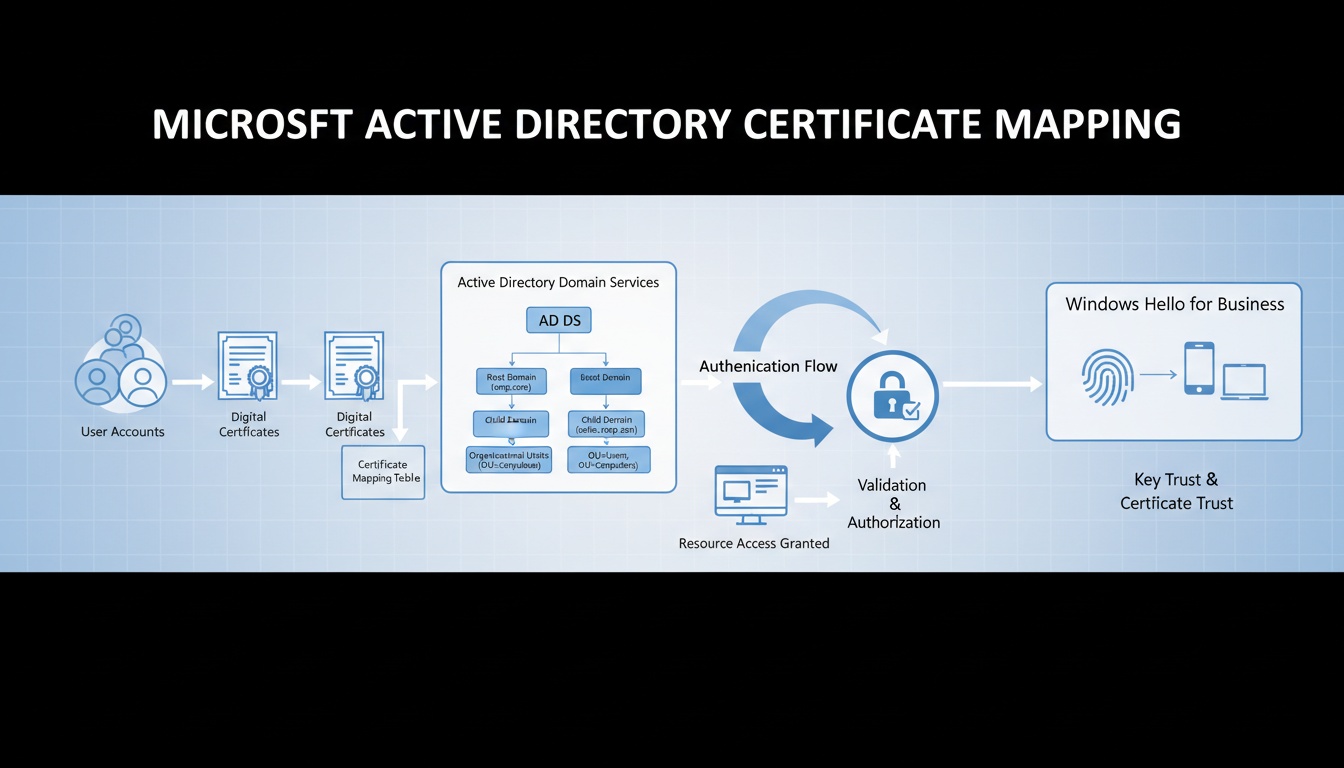
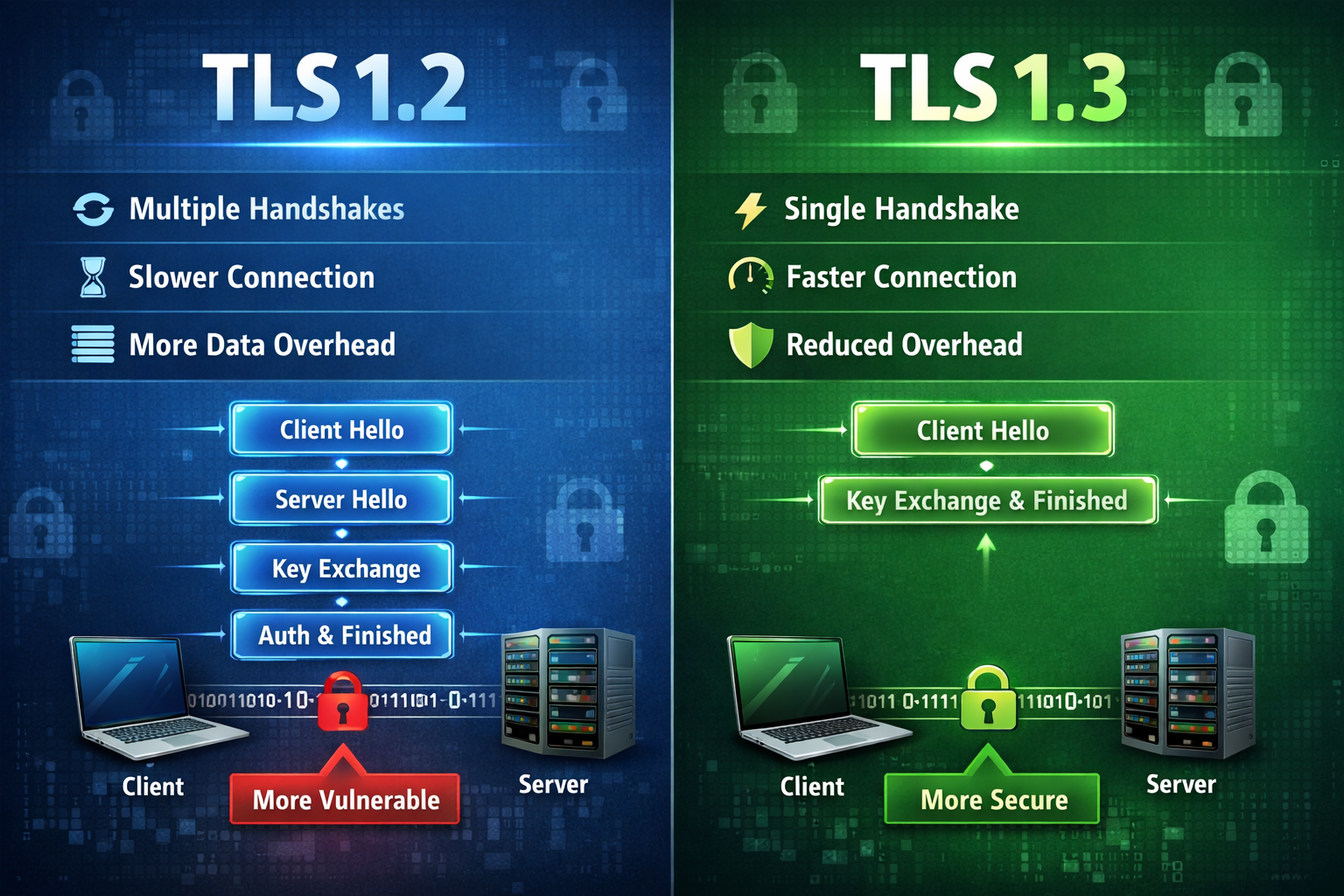
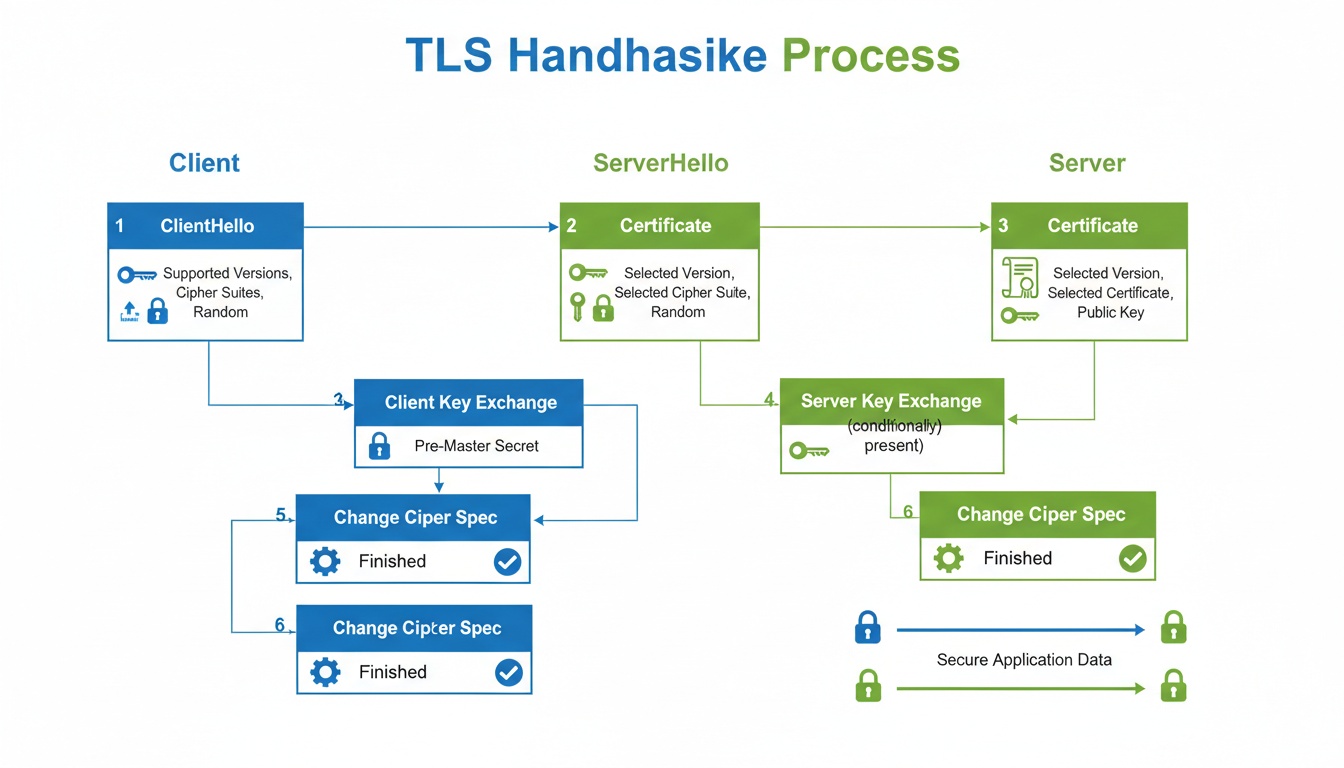
Insight and advice from our expert team
Stay updated with the latest trends, best practices, and insights in cybersecurity and enterprise security.
Featured Posts
Recent Posts
Ready to Secure Your Enterprise?
Experience how our cryptographic solutions simplify, centralize, and automate identity management for your entire organization.