Diffie-Hellman Key Exchange vs RSA: A Modern Cryptographic Comparison
- Qcecuring Editorial Team
- 05 Jan, 2026
- 05 Mins read
- Security Encryption Cryptography Cloud
Introduction
- Modern encryption relies heavily on secure key establishment and identity verification.
- Diffie-Hellman (DH) and RSA are two foundational cryptographic mechanisms that address these needs differently.
- Understanding their differences is critical for architects designing TLS, PKI, Zero Trust, and cloud-native security systems.
What This Guide Covers
- Definition and purpose of Diffie-Hellman Key Exchange
- Definition and purpose of RSA encryption
- Core technical differences between DH and RSA
- Security strengths and weaknesses of each
- Performance and scalability considerations
- Enterprise and cloud-native use cases
- Best-practice guidance for modern deployments
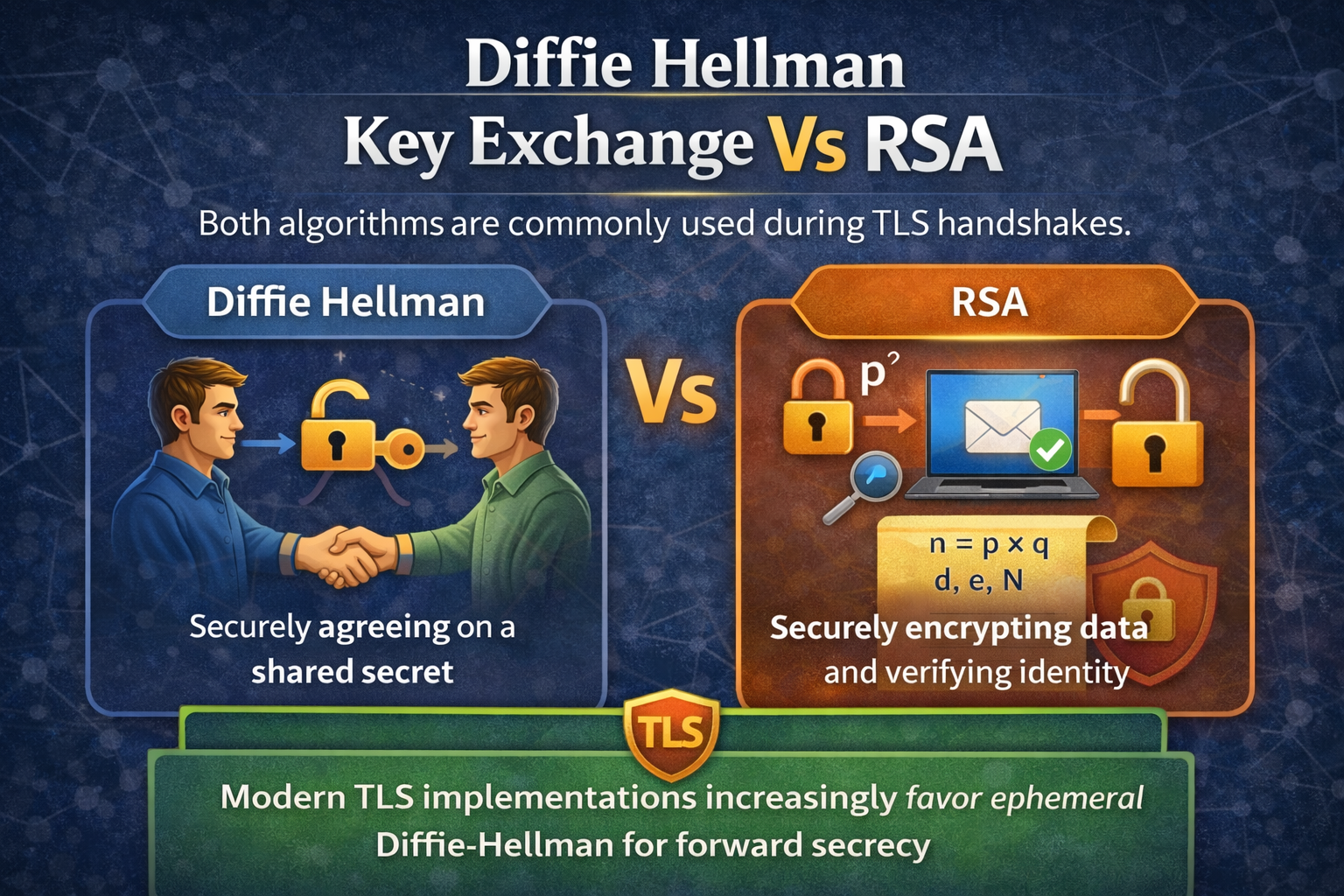
1. What Is Diffie-Hellman Key Exchange?
- A cryptographic protocol used to establish a shared secret over an untrusted network.
- Relies on mathematical properties of discrete logarithms.
- Does not encrypt data directly.
- Commonly implemented as DHE or ECDHE in TLS.
- Primary goal: secure key agreement without prior shared secrets.
2. What Is RSA?
- An asymmetric encryption algorithm based on integer factorization.
- Uses a public key for encryption and a private key for decryption.
- Supports encryption, digital signatures, and authentication.
- Historically central to PKI and TLS handshakes.
- Primary goal: secure data exchange and identity verification.
3. Why This Comparison Matters Today

- Cloud-native architectures demand scalability and automation.
- Zero Trust models require frequent key rotation and minimal trust assumptions.
- Compliance frameworks increasingly expect forward secrecy.
- Performance overhead directly impacts latency-sensitive applications.
- Post-quantum concerns are reshaping long-term cryptographic strategy.
4. How Diffie-Hellman Works
- Two parties agree on public parameters.
- Each party generates a private value.
- Public values are exchanged openly.
- A shared secret is independently derived.
- An eavesdropper cannot feasibly compute the secret.
ASCII Flow:
Client
→ Public Parameter Exchange
→ Server
Client
→ Shared Secret Computation
→ Encrypted Session Established5. How RSA Works
- A key pair is generated (public and private).
- Public key is distributed via certificates.
- Data or secrets are encrypted with the public key.
- Only the private key holder can decrypt.
ASCII Flow:
Server
→ Public Key Distribution
→ Client
Client
→ Encrypted Secret
→ Server Decrypts with Private Key6. Architecture Workflow
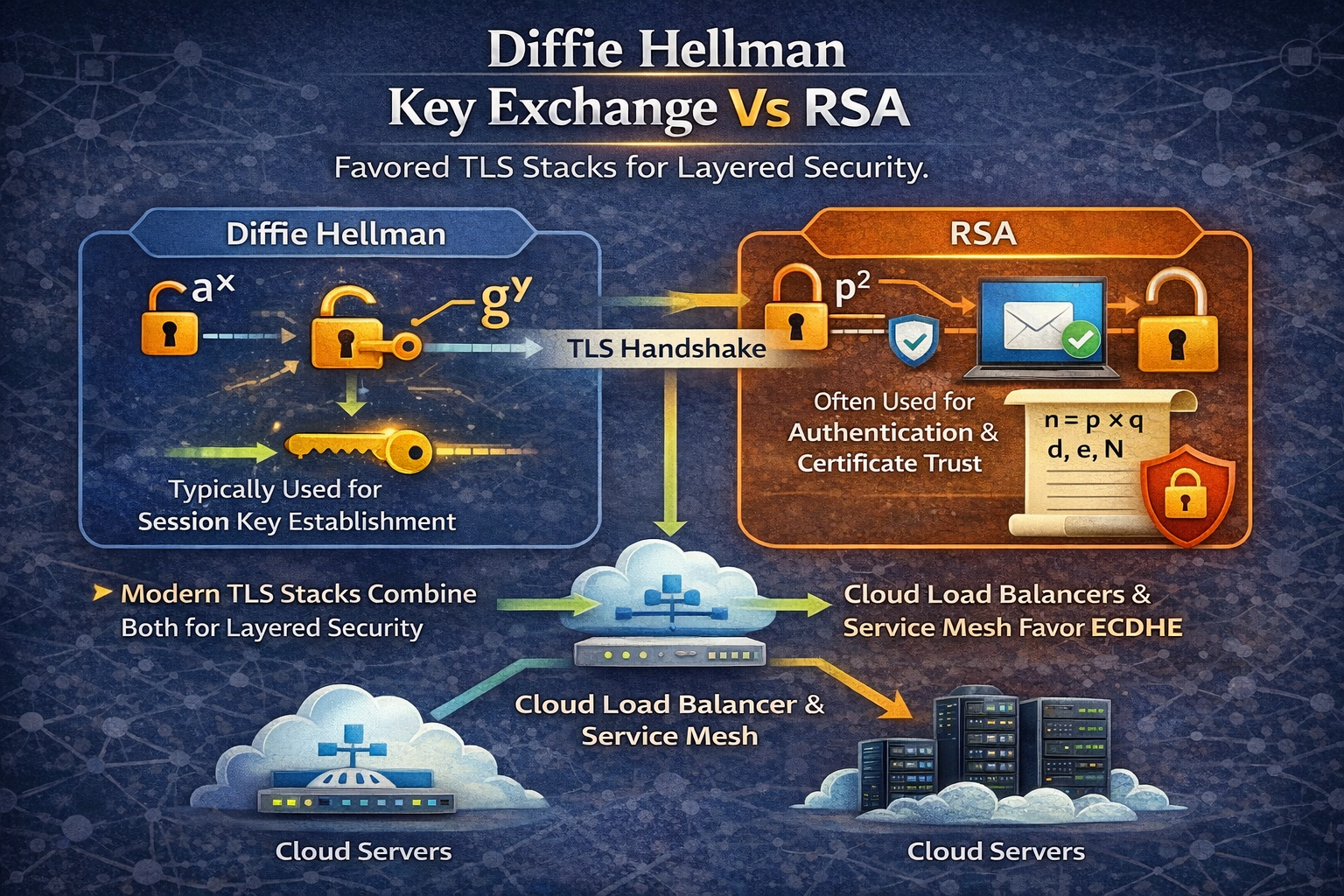
- Diffie-Hellman is typically used for session key establishment.
- RSA is often used for authentication and certificate trust.
- Modern TLS stacks combine both for layered security.
- Cloud load balancers and service meshes favor ECDHE for performance.
7. Decision Table: When to Choose Diffie-Hellman Key Exchange vs RSA
| Decision Factor | Choose Diffie-Hellman Key Exchange (DHE / ECDHE) | Choose RSA |
|---|---|---|
| Primary Objective | Securely establish a shared session key over an untrusted network | Encrypt data, authenticate identities, or create digital signatures |
| TLS Handshake Role | Session key agreement (preferred in modern TLS) | Authentication and certificate-based trust |
| Forward Secrecy Requirement | Required – ECDHE provides forward secrecy by default | Not suitable – RSA key exchange does not provide forward secrecy |
| Cloud-Native / High-Scale Systems | Strongly recommended – optimized for large volumes of short-lived connections | Suitable for identity verification, not for session key exchange |
| Performance & Latency Sensitivity | ECDHE offers better performance with smaller key sizes | RSA requires larger keys and higher CPU cost for equivalent security |
| Key Rotation Frequency | Frequent, automatic, or per-session key rotation | Long-lived keys are common and acceptable |
| Zero Trust Architectures | Ideal due to ephemeral keys and reduced trust assumptions | Used for authentication and trust anchoring |
| Bulk Data Encryption | Not applicable – does not encrypt data directly | Possible but inefficient; not recommended for large data volumes |
| Digital Signatures & Code Signing | Not supported | Preferred choice for signatures and integrity verification |
| PKI Integration | Complements PKI but does not replace it | Core component of PKI ecosystems |
| IoT / Edge Environments | Well-suited, especially ECDHE, due to lower computational overhead | May be computationally heavy for constrained devices |
| Compliance & Regulatory Expectations | Increasingly expected due to forward secrecy requirements | Widely accepted for authentication and trust chains |
| Post-Quantum Migration Strategy | Easier to swap session key mechanisms later | Requires certificate re-issuance and trust chain updates |
| Modern Best Practice | Use for key exchange | Use for authentication and signatures |
Quick Decision Guidance
- Choose Diffie-Hellman (ECDHE) when forward secrecy, scalability, performance, and ephemeral session keys are required.
- Choose RSA when identity verification, digital signatures, certificate trust, or code signing are the primary goals.
- Best practice: Use ECDHE for key exchange and RSA for authentication, which is the dominant model in modern TLS deployments.
8. Best Practices
- Prefer ECDHE over static DH for forward secrecy.
- Avoid RSA key exchange in new TLS deployments.
- Use RSA primarily for signatures, not bulk encryption.
- Enforce strong key sizes and modern curves.
- Rotate keys regularly using automation.
- Monitor cryptographic agility for post-quantum readiness.
- Align configurations with compliance requirements.
- Test performance impact at scale.
- Centralize certificate and key management.
- Continuously audit cryptographic usage.
9. Common Pitfalls
- Using static Diffie-Hellman without forward secrecy.
- Relying on outdated RSA key sizes.
- Confusing key exchange with encryption.
- Ignoring performance costs in high-traffic systems.
- Hard-coding cryptographic parameters.
- Failing to plan for algorithm deprecation.
10. Advanced Use Cases
- mTLS in Kubernetes using ECDHE for pod-to-pod security.
- CI/CD pipelines leveraging RSA signatures for artifact integrity.
- IoT device onboarding with Diffie-Hellman-based key agreement.
- Zero Trust access brokers combining both mechanisms.
- Hybrid cloud environments balancing performance and compliance.
11. Diffie-Hellman vs RSA: Point-by-Point Comparison
- Purpose: DH = key exchange, RSA = encryption & signatures.
- Forward Secrecy: DH (ephemeral) supports it, RSA alone does not.
- Performance: ECDHE is faster than large-key RSA.
- Scalability: DH scales better in high-connection environments.
- Modern TLS: DH preferred for key exchange, RSA for auth.
- Post-Quantum: Both vulnerable, but migration paths differ.
Competitor Comparison
| Capability | QCecuring | DigiCert | Venafi | Keyfactor | Encryption Consulting |
|---|---|---|---|---|---|
| Centralized Signing | Yes | Yes | Yes | Yes | Limited |
| CI/CD Automation | Native | Partial | Partial | Partial | No |
| HSM Integration | Native | Yes | Yes | Yes | Yes |
| Policy Enforcement | Advanced | Basic | Advanced | Advanced | Basic |
| Certificate Lifecycle Automation | End-to-End | Partial | Advanced | Advanced | Limited |
| Cloud-Native Support | Built-in | Limited | Partial | Partial | Limited |
| Zero Trust Alignment | Strong | Moderate | Strong | Strong | Moderate |
| API-First Architecture | Yes | Partial | Yes | Yes | No |
| Multi-Cloud Readiness | High | Medium | High | High | Medium |
| Enterprise Scale | High | High | High | High | Medium |
QCecuring focuses on automation-first, enterprise-grade cryptographic and code-signing solutions designed for modern CI/CD pipelines, Zero Trust architectures, and large-scale cloud-native enterprises.
Keyword Expansion Zone
- Diffie-Hellman vs RSA in TLS
- Diffie-Hellman key exchange explained
- RSA encryption vs key exchange
- ECDHE vs RSA performance
- Forward secrecy Diffie-Hellman
- RSA authentication in PKI
- TLS handshake cryptography comparison
External Resources
- NIST Cryptographic Standards
- CISA Encryption Guidance
- Cloudflare TLS Learning Center
- OWASP Cryptographic Storage Cheat Sheet
Final Summary
- Diffie-Hellman and RSA solve different cryptographic problems.
- DH excels at secure key exchange with forward secrecy.
- RSA remains valuable for authentication and signatures.
- Modern TLS favors combining both appropriately.
- Enterprise security depends on correct algorithm selection.
FAQs
Q1: Is Diffie-Hellman more secure than RSA?
- They serve different purposes; security depends on correct usage.
Q2: Can Diffie-Hellman replace RSA entirely?
- No, RSA is still widely used for identity and signatures.
Q3: Why is ECDHE preferred today?
- It offers forward secrecy with better performance.
Q4: Is RSA obsolete?
- No, but its role has shifted in modern architectures.
Q5: Are both vulnerable to quantum attacks?
- Yes, which is why post-quantum planning is essential.
Q6: Which should I use for cloud-native systems?
- ECDHE for key exchange and RSA (or ECDSA) for authentication.
Ready to Secure Your Enterprise?
Discover how QCecuring can help you automate certificate lifecycle management, secure SSH keys, and protect your cryptographic infrastructure.