

Categories

10 Best Open Source PKI Software Solutions (And Choosing the Right One)
Public Key Infrastructure (PKI) underpins so much of digital trust: TLS, code signing, identity, IoT...

SSL vs TLS: Understanding the Difference Between Two Security Protocols
When you see a padlock icon in your browser’s address bar, it indicates a **secure, encrypted connec...
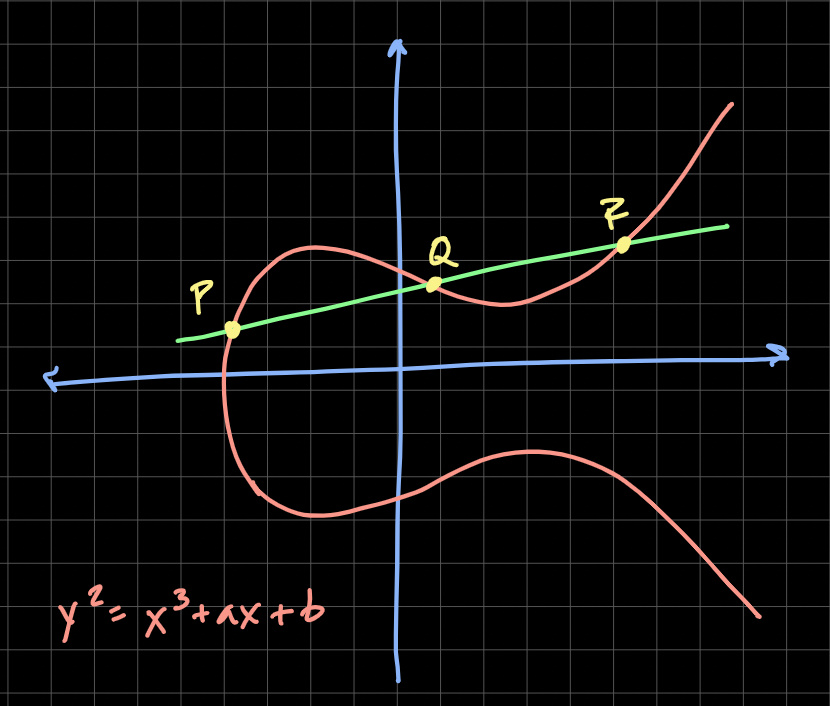
What Is Elliptic Curve Cryptography & How Does It Work
Elliptic Curve Cryptography (ECC) is a modern public-key cryptography method that has gained tractio...

The Definitive Guide to SSH Key Management [July 2022]
This is the most complete guide to SSH Key Lifecycle Management as of July 2022. We have tried to...

How DevOps Teams Can Automate PKI Deployment On Demand With QCecuring SSL CLM and AWS PrivateCA
In today’s fast-paced digital world, DevOps teams are under increasing pressure to deliver software ...

Wildcard Certificates & How Certificate Lifecycle Management Helps in Managing Them
In today's digital world, securing online communication is critical. One way to achieve this is thro...

What is a Certificate Signing Request (CSR) & How Certificate Lifecycle Management Helps
A **Certificate Signing Request (CSR)** is a message generated by an applicant for a digital certifi...