
- Qcecuring Editorial Team
- 15 Jan, 2025
- 25 Mins read
- Security Compliance Cloud
Federal systems and defense contractors rely on cryptography to protect sensitive information from adversaries. But how do you verify that encryption actually works as promised? How do agencies know that a cryptographic module won’t fail under pressure or leak secrets through side channels?
FIPS 140-2 provides the answer. This federal standard establishes rigorous security requirements for cryptographic modules—the hardware, software, and firmware components that implement encryption. Published by NIST in 2001, FIPS 140-2 has become the gold standard for cryptographic security validation.
For federal agencies, FIPS 140-2 compliance isn’t optional—it’s mandated by law. For defense contractors handling Controlled Unclassified Information, FIPS validation is required under CMMC and NIST 800-171. For technology vendors, a FIPS certificate opens doors to government contracts worth billions.
What This Guide Covers
This comprehensive guide explores FIPS 140-2 requirements, validation processes, and implementation strategies for enterprises:
- The four security levels and how to select the appropriate level for your use case
- The 11 security requirement areas that define cryptographic module validation
- Step-by-step CMVP certification process and timeline expectations
- FIPS 140-2 vs FIPS 140-3 differences and migration planning for the 2026 sunset
- CMMC 2.0 compliance requirements and NIST 800-171 control 3.13.11 implementation
- Cloud-native FIPS deployment on AWS, Azure, and GCP
- Hardware Security Module selection and configuration
- Common validation pitfalls and how to avoid costly delays
- Real-world implementation scenarios for defense contractors and federal agencies

Understanding the FIPS 140-2 Framework
Federal Information Processing Standard (FIPS) 140-2 specifies security requirements that cryptographic modules must satisfy when protecting sensitive but unclassified information. The standard emerged from a fundamental problem: cryptographic implementations often contained subtle flaws that undermined security guarantees.
Academic research demonstrates mathematically sound encryption algorithms. But implementing those algorithms in hardware and software introduces countless opportunities for error. Timing vulnerabilities leak information through execution duration. Power analysis extracts keys by measuring electrical consumption. Memory management bugs expose plaintext. Side channels bypass cryptographic strength entirely.
FIPS 140-2 addresses implementation security through rigorous third-party testing. Cryptographic modules undergo evaluation by accredited laboratories that verify the module performs as specified, protects sensitive data throughout its lifecycle, and resists known attack vectors. This validation provides assurance that encryption will function correctly in operational environments.
The standard defines a cryptographic module as any hardware, software, firmware, or combination thereof that implements cryptographic functions or processes. This includes dedicated hardware security modules, encryption software libraries, operating system cryptographic APIs, firmware in network appliances, and hybrid implementations combining multiple components.
For federal agencies, FIPS 140-2 compliance is required by the Information Technology Management Reform Act of 1996. Section 5131 mandates that cryptographic modules protecting sensitive government information must be validated to FIPS standards. The requirement extends to contractors, grantees, and other organizations processing federal data.
The Cryptographic Module Validation Program operates as a joint effort between NIST and the Canadian Centre for Cyber Security. CMVP coordinates testing, issues certificates, and maintains the authoritative list of validated modules. Organizations can verify validation status by searching the CMVP database using module name, vendor, or certificate number.
The Four Security Levels Decoded
FIPS 140-2 provides four increasing security levels designed to cover diverse applications and threat models. Selecting the appropriate level requires understanding what each level guarantees and what attacks it defends against.
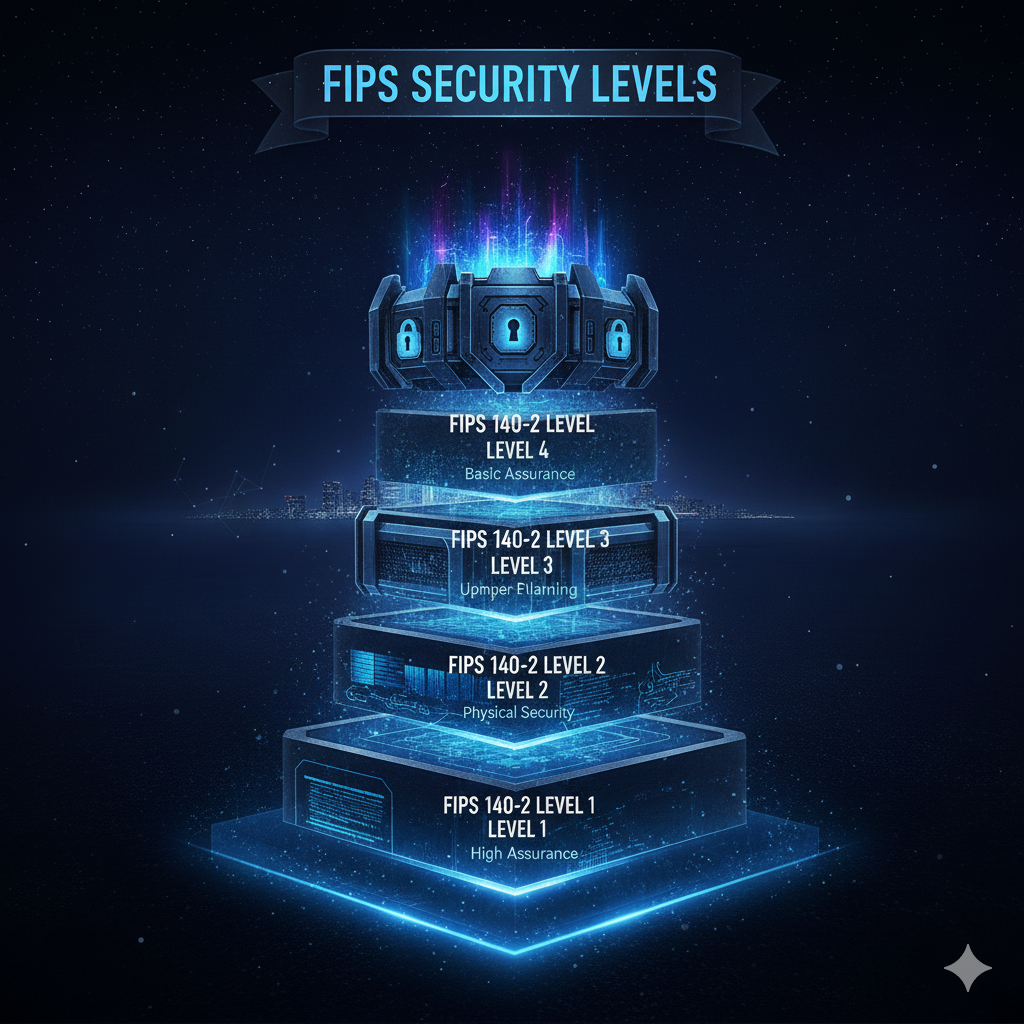
Level 1: Production-Grade Baseline
Security Level 1 provides the foundation for cryptographic module validation. The level requires that modules use FIPS-approved algorithms, implement those algorithms correctly, and document their security boundaries and operational parameters.
Level 1 modules must specify which cryptographic algorithms they implement, define their logical and physical boundaries clearly, and document all interfaces through which data enters or exits. The module must include approved algorithms for encryption, digital signatures, hashing, and key establishment.
Physical security requirements are minimal at Level 1. Software implementations running on general-purpose operating systems qualify without special hardware protections. The level assumes that the operational environment provides adequate physical security.
Level 1 suits applications where cost and ease of deployment outweigh physical threat concerns. Commercial software products, cloud service cryptographic libraries, and general-purpose encryption tools typically target Level 1 validation.
Level 2: Tamper Evidence and Role-Based Authentication
Level 2 adds requirements that make unauthorized access detectable. Modules must provide physical tamper-evidence features like seals, coatings, or enclosures that show visible signs if someone attempts to access internal components.
Role-based authentication becomes mandatory. The module must support at least two distinct roles—typically a Crypto Officer who manages cryptographic keys and configuration, and a User who performs cryptographic operations. The module must verify identity before granting role access.
For software implementations, Level 2 requires that the operating system meet Common Criteria EAL2 certification. This ensures the OS provides adequate separation between processes and enforces access controls that protect the cryptographic module from other software.
Level 2 applies when physical access to cryptographic equipment might occur but strong deterrents and detection mechanisms suffice. Network encryption devices, certificate authorities, and enterprise key management systems commonly implement Level 2.
Level 3: Tamper Resistance and Identity Authentication
Level 3 significantly strengthens physical security. Tamper-evidence gives way to tamper-resistance—the module must actively prevent unauthorized physical access. Attempts to penetrate the module’s enclosure should be detected and trigger protective responses like key erasure.
Identity-based authentication replaces role-based authentication. Rather than authenticating that someone holds a particular role, Level 3 requires authenticating specific individuals. Multi-factor authentication becomes common, combining something you know (password), something you have (token), or something you are (biometric).
Physical or logical separation between interfaces carrying Critical Security Parameters is required. Keys must enter and exit the module only in encrypted form. Clear-text keys cannot cross the module boundary in ways that would expose them to interception.
Environmental failure protection appears at Level 3. Modules must detect operation outside normal temperature and voltage ranges and either implement protections to maintain security or undergo environmental failure testing demonstrating that excursions won’t compromise cryptographic material.
Level 3 targets scenarios where physical attacks are realistic threat vectors. High-value payment processing, classified data encryption, and critical infrastructure protection often require Level 3 validation.
Level 4: Complete Physical Protection
Level 4 represents the highest commercially available cryptographic security. Physical security becomes proactive—the module must detect and respond to environmental manipulation attempts in real time.
Tamper detection must be active rather than passive. Penetration attempts, voltage manipulation, temperature excursions, or electromagnetic interference should trigger immediate protective responses. These responses typically involve erasing all cryptographic keys and sensitive parameters, rendering the module inoperable but preventing key extraction.
Multi-factor identity-based authentication is required for all critical operations. The module must verify identity through multiple independent mechanisms before permitting access to cryptographic services.
Environmental protection requirements become stringent. The module must continue operating securely across extended environmental ranges or implement mechanisms that guarantee security even during environmental attack attempts.
Level 4 suits applications where cryptographic compromise would have catastrophic consequences. Nuclear facility security, military communications encryption, and classified information processing systems operate at Level 4.
Here’s how the levels compare across key dimensions:
Security Physical Authentication Software Typical
Level Protection Requirements Environment Use Cases
Level 1 None required None required Any OS Commercial apps,
cloud services
Level 2 Tamper Role-based CC EAL2 OS Network devices,
evidence enterprise PKI
Level 3 Tamper Identity-based CC EAL3 OS Payment systems,
resistance (multi-factor) HSM clusters
Level 4 Active tamper Multi-factor CC EAL4+ OS Classified systems,
response identity critical infraThe 11 Security Requirement Areas
FIPS 140-2 evaluates cryptographic modules across 11 distinct security areas. Each area addresses specific aspects of secure design and implementation. Understanding these areas helps organizations prepare for validation and implement compliant modules.
1. Cryptographic Module Specification
The module must be precisely defined and documented. Specifications must identify the module’s physical and logical boundaries, describe all hardware and software components, list cryptographic algorithms implemented, and define operational modes.
Documentation requirements are extensive. The security policy document describes how the module implements security features, what roles exist, which services each role can access, and how the module maintains security. This document becomes the contract between vendor and validator.
2. Cryptographic Module Ports and Interfaces
All data entering and leaving the module must flow through defined interfaces. FIPS 140-2 recognizes four interface types: data input, data output, control input, and status output.
The module must segregate different data types across these interfaces. Plaintext data, ciphertext, cryptographic keys, and control parameters must be clearly separated. Interfaces carrying Critical Security Parameters require particular attention—these interfaces must be protected to prevent key leakage.
3. Roles, Services, and Authentication
Every cryptographic module must define roles that users or processes assume when accessing module services. Each role has associated services—cryptographic operations or administrative functions—that the role can perform.
Authentication mechanisms verify that operators possess the credentials required for their role. The strength of authentication increases with security levels. Level 1 requires no authentication. Level 2 requires role-based authentication. Levels 3 and 4 require identity-based authentication with increasing strength.
4. Finite State Model
The module must implement a finite state machine that defines valid operational states and transitions between states. Typical states include initialization, operation, error, and shutdown.
The finite state model documents what services are available in each state, what events trigger state transitions, and how the module behaves during transitions. This model helps validators understand module behavior and verify that security is maintained across all states.
5. Physical Security
Physical security requirements vary dramatically by security level. Level 1 requires no physical security. Level 2 requires tamper-evidence. Level 3 requires tamper-resistance. Level 4 requires active tamper response.
The specific mechanisms depend on module form factor. Hardware modules use physical enclosures, seals, coatings, or sensors. Software modules rely on the underlying platform’s physical security combined with logical protections.
6. Operational Environment
This area applies primarily to software and firmware modules. The operational environment encompasses the underlying hardware, operating system, and other software that hosts the cryptographic module.
For Levels 1 and 2, the environment must provide appropriate separation between processes. For Levels 3 and 4, the environment must meet Common Criteria certification requirements that demonstrate security properties like access control, audit, and protection against tampering.
7. Cryptographic Key Management
Key management represents one of the most critical security areas. The module must generate keys using approved random number generators, store keys securely throughout their lifecycle, establish keys through approved protocols, and destroy keys securely when no longer needed.
FIPS 140-2 specifies approved algorithms for key generation, key establishment, and key derivation. Keys must be protected according to their sensitivity—more valuable keys require stronger protection mechanisms. The module must ensure that keys cannot be extracted or modified except through authorized procedures.
8. Electromagnetic Interference and Compatibility
Cryptographic modules must operate correctly in electromagnetic environments without leaking sensitive information through electromagnetic radiation. EMI/EMC requirements ensure that modules function reliably and don’t emit signals that could enable side-channel attacks.
Testing verifies compliance with Federal Communications Commission regulations for electromagnetic emissions. For higher security levels, additional testing may evaluate whether electromagnetic emanations could leak cryptographic material.
9. Self-Tests
Modules must perform automated self-tests to verify correct operation. Power-on self-tests run when the module initializes, verifying that cryptographic algorithms function correctly and that the module hasn’t been tampered with.
Conditional tests trigger before using specific algorithms or functions. If a module implements RSA encryption, conditional tests verify RSA correctness before performing RSA operations. This ensures that transient faults or attacks haven’t corrupted cryptographic functions.
10. Design Assurance
Design assurance requirements ensure that modules are built with security in mind. Configuration management tracks all module components. Secure distribution mechanisms protect modules during delivery. Development environment controls prevent malicious code injection.
The module must include version identification so users can verify they’re using the validated version. Documentation must be sufficient for validators and users to understand security features and limitations.
11. Mitigation of Other Attacks
This area addresses attacks beyond the scope of earlier sections. Side-channel attacks like timing analysis, power analysis, and fault injection can extract cryptographic keys without breaking the underlying algorithms.
Higher security levels require resistance to specific attack classes. The module must document which attacks it mitigates and how. For Level 3 and above, physical probing attacks and fault induction become significant concerns requiring explicit countermeasures.

Here’s how validation flows through these areas:
Module Development
↓
Documentation Preparation
↓
Lab Selection & Contract
↓
Algorithm Testing (CAVP)
↓
Module Testing (11 Areas)
↓
Test Report Submission
↓
NIST/CSE Review
↓
Certificate Issuance
↓
Ongoing MaintenanceFIPS 140-2 vs FIPS 140-3: Navigating the Transition
FIPS 140-3 was approved in March 2019 as the successor to FIPS 140-2. The new standard aligns with international standards ISO/IEC 19790 and ISO/IEC 24759, allowing a single validation to meet both US and international requirements.
Key Architectural Differences
FIPS 140-3 modernizes several aspects of cryptographic module validation. The standard explicitly recognizes hybrid modules combining hardware, software, and firmware. FIPS 140-2 restricted hybrid modules to Level 1; FIPS 140-3 removes this restriction.
Module types expand to include software modules, firmware modules, hardware modules, hybrid-software modules, and hybrid-firmware modules. This taxonomy better reflects modern cryptographic implementations.
Authentication requirements evolve. FIPS 140-2 required crypto officer and user roles with an optional maintenance role. FIPS 140-3 requires only the crypto officer role, with user and maintenance roles optional. Level 4 now mandates multi-factor identity-based authentication for trusted channel operations.
The interface model adds a fifth interface type: control output interface. This interface allows the module to output commands and signals indicating operational state, improving troubleshooting and monitoring capabilities.
Self-test requirements change significantly. The power-on self-test focuses on memory integrity rather than algorithm correctness. Conditional Algorithm Self-Tests run before using each algorithm rather than at startup. This approach detects runtime corruption without imposing startup delays for unused algorithms.
FIPS 140-3 replaces the trusted path concept with trusted channels. A trusted channel is a secure communication link between the cryptographic module and endpoint device, protecting Critical Security Parameters during transmission. This change better addresses modern distributed architectures.
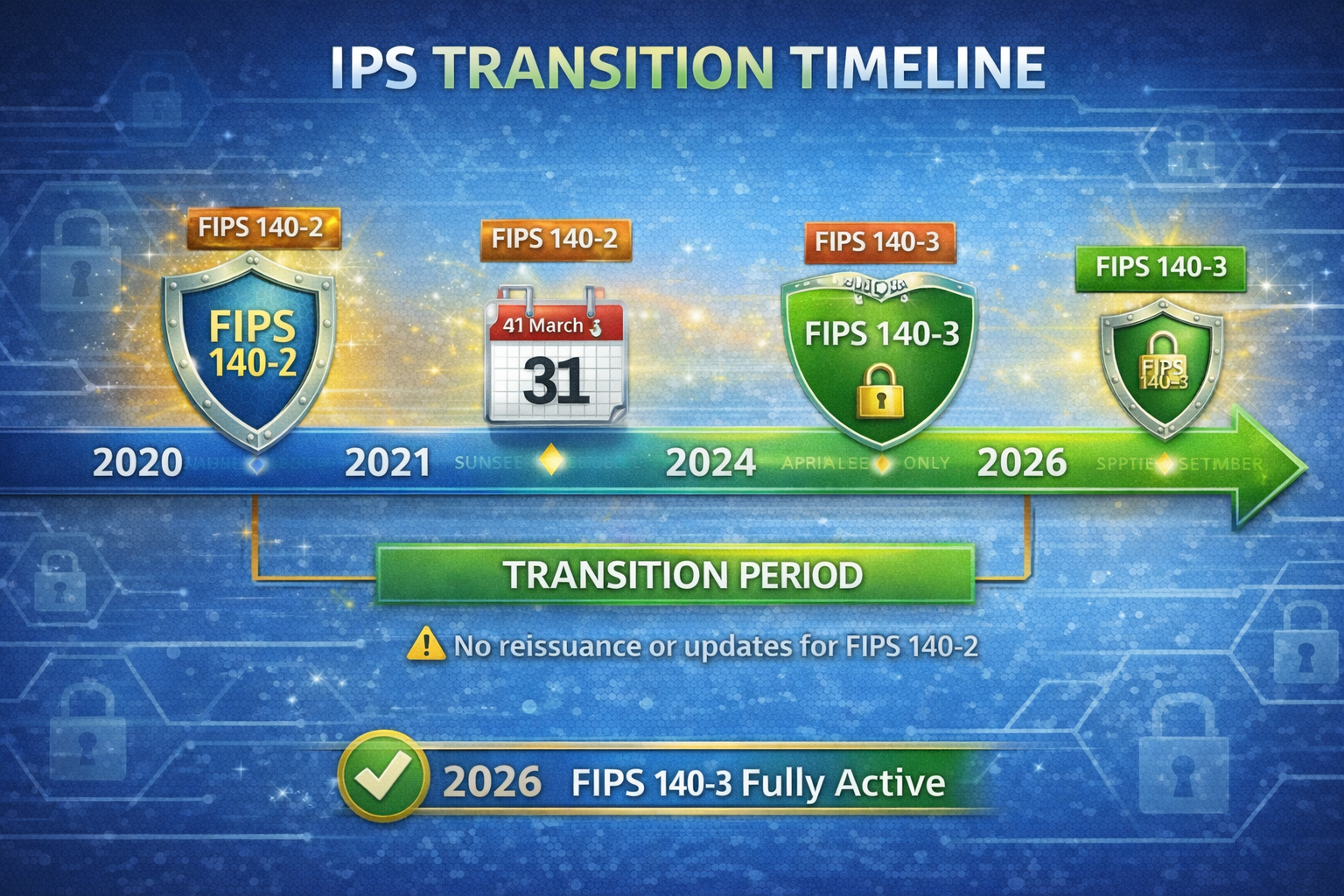
Transition Timeline and Implications
The transition timeline spans seven years to allow industry adjustment:
March 2019: FIPS 140-3 approved and published September 2019: FIPS 140-3 becomes effective September 2020: CMVP begins accepting FIPS 140-3 submissions April 2022: CMVP stops accepting new FIPS 140-2 submissions September 2026: All FIPS 140-2 certificates move to historical list
Organizations face a critical decision point. FIPS 140-2 validations issued before September 2026 remain on the active list for five years from validation date. A certificate issued in January 2025 stays active until January 2030, even though FIPS 140-2 itself sunsets in September 2026.
However, relying on FIPS 140-2 certificates creates long-term risk. After September 2026, new contracts may require FIPS 140-3 validation. Federal procurement policies could mandate the newer standard. Defense contractors pursuing CMMC compliance should plan for FIPS 140-3 migration.
Migration Strategy Considerations
Vendors with existing FIPS 140-2 certificates must decide whether to revalidate under FIPS 140-3. The validation process starts fresh—there’s no “upgrade path” that reuses FIPS 140-2 test results. The entire module undergoes new testing against FIPS 140-3 requirements.
This creates a validation queue challenge. Many organizations postponed FIPS 140-3 validation, waiting to see how requirements would mature. Now, validation laboratories face increasing demand with limited capacity. Current wait times for validation range from 12 to 24 months from lab engagement to certificate issuance.
Organizations should begin FIPS 140-3 planning immediately if they:
Rely on FIPS validation for government contracts Provide cryptographic products to federal agencies or defense contractors Currently hold FIPS 140-2 certificates approaching expiration Face competitive pressure from vendors with FIPS 140-3 certificates Operate in regulated industries expecting FIPS 140-3 compliance
The validation investment is substantial. Costs typically range from $50,000 to $250,000 depending on module complexity, security level, and number of platforms. Timeline expectations should account for 12-24 months from initial lab engagement to certificate receipt.
CMMC Compliance and FIPS 140-2 Integration
The Cybersecurity Maturity Model Certification program dramatically expands FIPS validation requirements beyond federal agencies to the entire Defense Industrial Base. Approximately 220,000 contractors must demonstrate cybersecurity compliance to continue DoD business.
NIST 800-171 Control 3.13.11 Explained
CMMC Level 2 incorporates all 110 security controls from NIST Special Publication 800-171. Control 3.13.11 states: “Employ FIPS-validated cryptography when used to protect the confidentiality of CUI.”
This control appears straightforward but creates significant implementation challenges. The requirement applies whenever cryptography protects Controlled Unclassified Information—whether encrypting data at rest on storage devices, encrypting data in transit across networks, or encrypting data in backup systems.
NIST considers non-validated cryptography equivalent to plaintext. Using strong algorithms like AES-256 provides no credit toward control satisfaction unless the implementation holds FIPS validation. This position reflects hard-learned lessons: even mathematically sound algorithms fail when incorrectly implemented.
The control requires FIPS validation at the module level, not just algorithm level. Many organizations initially assume that using AES or RSA satisfies the requirement. It doesn’t. The entire cryptographic module—the software library, hardware device, or firmware implementation—must hold a CMVP certificate.
Mapping CUI Workflows to FIPS Modules
Compliance requires identifying every location where CUI exists and every cryptographic mechanism protecting it. Defense contractors must document:
- All systems storing CUI and the encryption protecting storage devices
- All network paths transmitting CUI and the encryption protecting transmission
- All backup systems containing CUI and the encryption protecting backups
- All endpoints accessing CUI and the encryption protecting local storage
- All cloud services holding CUI and the validation status of cloud cryptography
For each cryptographic mechanism, contractors must provide evidence of FIPS validation. This evidence typically includes the CMVP certificate number, the validated module name and version, confirmation that the deployed version matches the validated version, and documentation showing the module operates in FIPS-approved mode.
Operating systems complicate compliance. Windows, Linux, and macOS contain cryptographic modules with FIPS 140-2 certificates. However, FIPS mode must be explicitly enabled. Simply running a FIPS-capable OS doesn’t satisfy the requirement—the system must be configured to use only FIPS-approved algorithms through validated modules.
Windows systems enable FIPS mode through Group Policy or registry settings. Linux systems configure FIPS mode during installation or through package management. Cloud platforms provide FIPS-compliant regions or services with validated cryptography.
Assessment Documentation Requirements
C3PAO assessors evaluating CMMC Level 2 compliance expect detailed FIPS documentation. Organizations should prepare:
A comprehensive inventory of all CUI storage and transmission paths For each path, documentation of the cryptographic mechanism employed CMVP certificate numbers for every cryptographic module in use Configuration evidence showing FIPS mode enabled where applicable Validation that deployed versions match certificate specifications Testing results confirming cryptography functions correctly in FIPS mode
Assessors may request demonstrations that FIPS mode is actually active. Windows systems can verify FIPS mode through security policy settings. Linux systems can check kernel parameters and package configurations. Network devices should show FIPS mode in administrative interfaces.
Cloud service usage requires special documentation. Many contractors use AWS, Azure, or GCC cloud platforms. These platforms provide FIPS 140-2 validated services, but contractors must verify and document:
Which cloud services process or store CUI Whether those services use FIPS-validated cryptographic modules CMVP certificate numbers for cloud platform modules Configuration settings ensuring FIPS-compliant encryption Evidence that data doesn’t flow through non-FIPS services
FedRAMP Moderate and High authorizations implicitly require FIPS validation, as FedRAMP incorporates NIST 800-53 controls that reference FIPS standards. Contractors can reference cloud providers’ FedRAMP authorizations as partial evidence of FIPS compliance.
Common CMMC FIPS Pitfalls
Many contractors struggle with FIPS validation requirements during CMMC assessments. Common failures include:
Assuming encryption is sufficient without validating FIPS certification status Deploying cryptographic modules that aren’t the validated version Failing to enable FIPS mode on capable operating systems and devices Using encryption products that are “FIPS-compliant” but not FIPS-validated Inadequate documentation of validation certificates and configurations Applying FIPS modules to some CUI workflows but not others Using cloud services without verifying cryptographic module validation
The distinction between FIPS-compliant and FIPS-validated causes particular confusion. FIPS-compliant products use FIPS-approved algorithms but haven’t undergone CMVP validation. FIPS-validated products hold actual CMVP certificates. Only validated products satisfy control 3.13.11.
The Cryptographic Module Validation Process
Achieving FIPS validation requires navigating a complex process involving vendors, testing laboratories, and NIST. Understanding the process helps organizations set realistic expectations for timelines and costs.
Selecting an Accredited Testing Laboratory
The National Voluntary Laboratory Accreditation Program accredits Cryptographic and Security Testing laboratories authorized to perform FIPS validation testing. Approximately 20 NVLAP-accredited labs currently operate globally.
Vendors select a lab based on technical expertise, capacity, geographic location, and cost. Labs differ in their specializations—some focus on hardware modules, others on software implementations, some on high-security-level validations.
The initial engagement involves scoping the validation. The lab reviews module documentation, identifies platforms for testing, determines which security level to target, and estimates timeline and costs. This scoping phase typically requires 2-4 weeks.
Lab costs vary significantly based on module complexity. Simple software libraries might cost $50,000 to $75,000 for Level 1 validation. Complex hardware modules targeting Level 3 or 4 could require $150,000 to $250,000. Multi-platform validations where the same module runs on different operating systems or hardware configurations multiply costs.
Algorithm Testing Through CAVP
Before module validation begins, individual cryptographic algorithms must be validated through the Cryptographic Algorithm Validation Program. CAVP verifies that implementations of AES, RSA, SHA, ECDSA, and other approved algorithms produce correct results.
CAVP testing precedes CMVP validation because FIPS 140-2 requires that modules use only FIPS-approved algorithms with validated implementations. The lab submits algorithm implementations to CAVP, receives test vectors, executes tests, and submits results to NIST.
Algorithm validation typically requires 1-3 months per algorithm family. Modules implementing multiple algorithms may need several months of CAVP testing before module validation begins. However, CAVP and CMVP testing can overlap—early algorithm certificates allow module testing to proceed while remaining algorithms complete validation.
Module Testing and Documentation Review
The testing laboratory performs comprehensive evaluation across all 11 FIPS 140-2 security areas. Testing includes documentation review, physical examination, algorithm verification, side-channel analysis, and operational testing.
The lab produces a detailed test report documenting findings for each security requirement. The report describes the module, explains how it satisfies FIPS requirements, documents test procedures and results, and identifies any non-compliant areas requiring correction.
If the lab identifies deficiencies, the vendor must remediate them and resubmit the module for retesting. Minor issues might be addressed quickly. Fundamental design flaws could require months of rework. This iteration between testing and remediation often consumes more time than initial testing.
NIST Review and Certificate Issuance
Once the lab completes testing and issues a test report, the package moves to NIST for validation review. A NIST validator examines the test report, verifies completeness, checks that testing followed proper procedures, and ensures the module meets all FIPS requirements.
The NIST review phase historically consumed 3-6 months but has improved with CMVP process optimizations. The validator may request clarifications or additional information from the lab. Once satisfied, NIST issues a validation certificate and adds the module to the active validated modules list.
The certificate specifies the module name and version, vendor information, security level achieved, hardware and software platforms covered, operational environment requirements, and approved algorithms implemented. This certificate becomes the official evidence of validation.
Ongoing Maintenance and Revalidation
FIPS validation doesn’t end with certificate issuance. Vendors must maintain validation through the certificate’s lifetime. Any changes to the module—even minor updates—may require revalidation.
CMVP classifies changes as minor or major. Minor changes might allow maintaining the existing certificate with amendment. Major changes require new validation. The challenge is that what seems minor to engineers might constitute major changes in CMVP terms.
Algorithm updates almost always trigger revalidation. Changing platforms requires revalidation. Modifying key management procedures typically requires revalidation. Even security patches that fix vulnerabilities might require revalidation if they change cryptographic behavior.
Vendors must balance security updates against validation maintenance. A security patch fixing a critical vulnerability should be deployed immediately, even if it invalidates the FIPS certificate. However, frequent changes that constantly invalidate certificates create operational problems for customers who require continuous FIPS compliance.
Annual surveillance assessments verify that validated modules remain in compliance. Vendors submit documentation confirming no unauthorized changes occurred, configuration management remains in effect, and the deployed module matches the validated version.
Cloud and Enterprise Implementation Strategies
Modern infrastructure relies on cloud services, virtualized environments, and distributed architectures. Implementing FIPS-validated cryptography in these contexts requires understanding cloud provider capabilities and configuration options.
AWS FIPS 140-2 Services and Configuration
Amazon Web Services provides multiple FIPS 140-2 validated cryptographic modules across its service portfolio. AWS CloudHSM uses Thales Luna HSMs holding FIPS 140-2 Level 3 certificates. AWS Key Management Service operates FIPS 140-2 validated modules for key generation and cryptographic operations.
Organizations using AWS must configure services appropriately to ensure FIPS mode operation. KMS automatically uses validated cryptography for all operations—no special configuration required. S3 bucket encryption using SSE-KMS leverages KMS’s validated modules.
EC2 instances require explicit FIPS mode configuration. Amazon Linux provides FIPS modules through the dracut-fips package. Installing and enabling this package configures the system to use only FIPS-approved algorithms. Windows Server AMIs support FIPS mode through Group Policy configuration.
VPN connections to AWS can use FIPS-validated cryptography by selecting appropriate tunnel parameters. Site-to-site VPN configurations should specify FIPS-approved encryption algorithms like AES-256 and integrity algorithms like SHA-256.
AWS Certificate Manager Private CA uses FIPS 140-2 Level 3 HSMs for private CA key storage and operations. Organizations requiring FIPS-validated private CAs can use ACM PCA without deploying dedicated HSM infrastructure.
Azure FIPS Deployment Patterns
Microsoft Azure provides FIPS 140-2 validated cryptographic modules for Windows Server, Azure Key Vault, and Azure Dedicated HSM service. The Azure cryptography team maintains detailed documentation of validated modules and certificates.
Azure Key Vault protects keys and secrets using FIPS 140-2 Level 2 validated HSMs. The Premium tier provides HSM-backed key storage with FIPS validation. Standard tier uses software protection without HSM backing.
Virtual machines in Azure require FIPS mode configuration similar to on-premises systems. Windows VMs enable FIPS mode through Group Policy or registry settings. Linux VMs configure FIPS mode based on distribution—Red Hat, Ubuntu, and SUSE each have specific procedures.
Azure Storage service encryption uses Microsoft-managed keys stored in Key Vault HSMs. This configuration provides FIPS-validated encryption for data at rest without requiring customer-managed encryption key infrastructure.
Azure SQL Database Transparent Data Encryption integrates with Azure Key Vault for key management. Configuring TDE to use customer-managed keys in Premium Key Vault provides FIPS 140-2 validated encryption for database workloads.
GCP Cloud HSM and Cryptographic Services
Google Cloud Platform offers Cloud HSM for FIPS 140-2 Level 3 validated cryptographic operations. Cloud HSM integrates with Cloud Key Management Service for centralized key management with HSM-level protection.
Cloud KMS provides software-based key management with FIPS 140-2 Level 1 validation. For higher security levels, Cloud HSM backed keys offer Level 3 protection. The choice depends on compliance requirements and threat model.
Compute Engine instances can enable FIPS mode through OS configuration. Google provides documentation for configuring FIPS compliance on CentOS, RHEL, and Ubuntu instances running in GCP.
Cloud SQL for PostgreSQL and MySQL supports customer-managed encryption keys stored in Cloud KMS with HSM protection. This configuration provides FIPS-validated encryption for managed database services.
Google Kubernetes Engine nodes can be configured for FIPS mode operation. The Container-Optimized OS with FIPS enabled ensures that Kubernetes clusters operate with validated cryptography for both control plane and data plane operations.
Hardware Security Module Deployment
Organizations requiring highest assurance cryptographic operations deploy dedicated Hardware Security Modules. HSMs provide tamper-resistant hardware that generates, stores, and uses cryptographic keys without ever exposing them in software.
Selecting an HSM requires evaluating security level requirements, performance needs, form factor preferences, and integration capabilities. Network-attached HSMs serve multiple applications across the data center. PCIe HSMs install directly in servers for low-latency operations. USB HSMs provide portable cryptographic capabilities.
Leading HSM vendors like Thales, Entrust, and Utimaco offer products with FIPS 140-2 Level 3 validation. Some specialized HSMs achieve Level 4 for applications requiring maximum physical security.
HSM deployment architecture typically involves clusters for high availability. Three or more HSMs configured in an N+1 redundancy pattern ensure continued operation if individual devices fail. Key materials replicate across cluster members using secure protocols.
Integration with applications occurs through PKCS11 interfaces, JCE providers, Microsoft CNG, or proprietary APIs. Certificate authorities, code signing systems, SSL/TLS acceleration, and database encryption commonly leverage HSMs for key protection.
Operating System FIPS Mode Configuration
Both Windows and Linux operating systems include FIPS 140-2 validated cryptographic modules that must be explicitly enabled. Default configurations typically don’t enforce FIPS mode, allowing applications to use non-validated algorithms.
Windows systems enable FIPS mode through Security Policy. The system cryptography policy “Use FIPS compliant algorithms for encryption, hashing, and signing” forces all Windows cryptographic APIs to use only FIPS-approved algorithms from validated modules.
Enabling Windows FIPS mode affects .NET Framework, TLS implementations, BitLocker, EFS, and all applications using Windows CryptoAPI or CNG. Some legacy applications that rely on non-FIPS algorithms like MD5 may fail after enabling FIPS mode.
Red Hat Enterprise Linux provides FIPS mode through the fips-mode-setup utility. Installing the dracut-fips package and running fips-mode-setup —enable configures the system to operate in FIPS mode. The system requires reboot to activate FIPS configuration.
Ubuntu implements FIPS mode through the Ubuntu Advantage subscription. Installing ubuntu-advantage-tools and enabling fips or fips-updates configures validated cryptographic modules. The implementation uses OpenSSL FIPS module along with kernel-level cryptographic API changes.
FIPS mode validation extends beyond installation—organizations must verify that systems actually operate in FIPS mode. Windows systems show FIPS policy status in Security Policy editor. Linux systems display FIPS mode status through sysctl crypto.fips_enabled variable.
Best Practices for FIPS Implementation
Successfully deploying FIPS-validated cryptography requires attention to configuration details, operational procedures, and ongoing maintenance practices that preserve validation integrity.
- Verify that cryptographic modules are actually validated, not just compliant or based on validated algorithms
- Search the CMVP validated modules database to confirm current certificate status
- Document CMVP certificate numbers for all cryptographic modules protecting sensitive data
- Enable FIPS mode on all operating systems and devices that support it
- Test applications thoroughly in FIPS mode before production deployment
- Establish change management procedures that preserve FIPS validation during updates
- Monitor cryptographic module versions to ensure deployed systems match validated versions
- Plan for certificate expiration and initiate revalidation before certificates expire
- Document operational environment requirements specified in validation certificates
- Train operations teams on FIPS mode configuration and validation verification
- Implement centralized key management using validated HSMs or cloud KMS services
- Use automated configuration management to enforce FIPS settings across infrastructure
- Conduct regular audits verifying FIPS mode remains enabled and properly configured
- Maintain vendor relationships to receive notification of validation changes or updates
- Budget for ongoing validation maintenance costs, not just initial certification
Common Implementation Pitfalls
FIPS validation challenges frequently arise from misunderstandings about requirements or operational complexity. These pitfalls appear repeatedly across organizations implementing FIPS compliance.
- Assuming strong algorithms satisfy FIPS requirements without verifying module validation
- Deploying FIPS-capable systems without enabling FIPS mode configuration
- Using modules that are validated but deployed in non-FIPS operational modes
- Failing to test application compatibility in FIPS mode before production deployment
- Applying security patches that change cryptographic behavior and invalidate certificates
- Mixing FIPS-validated and non-validated cryptographic modules in the same workflow
- Using cloud services without verifying FIPS validation status and configuration
- Relying on vendor claims of FIPS compliance without independent certificate verification
- Implementing encryption for CUI using non-validated commercial products
- Deploying OpenSSL in standard mode when FIPS mode configuration is available
- Assuming hardware security modules are validated without checking CMVP database
- Using hash algorithms like MD5 or SHA-1 that aren’t FIPS-approved
- Failing to document validation evidence for compliance assessments
- Not planning for validation timeline delays when launching new cryptographic products
Advanced Implementation Scenarios
FIPS validation integrates into diverse architectural patterns across modern enterprises. Understanding these advanced scenarios helps organizations maximize security while maintaining operational efficiency.
Service Mesh mTLS with FIPS Cryptography
Service mesh architectures like Istio, Linkerd, and Consul Connect provide mutual TLS for service-to-service authentication. Configuring these meshes to use FIPS-validated cryptography strengthens zero-trust implementations.
Istio’s Envoy proxy can be configured to use FIPS-compliant BoringSSL builds. The envoy.reloadable_features.fips_compliant_ciphers feature flag restricts cipher suites to FIPS-approved algorithms. Control plane components like istiod must also operate in FIPS mode for end-to-end compliance.
Certificate management in service meshes requires particular attention. Certificate authorities issuing workload certificates should use FIPS-validated cryptographic modules for key generation and signing operations. Short-lived certificates combined with automated rotation minimize exposure if individual workload credentials are compromised.
Container Security and FIPS Base Images
Containerized applications present unique FIPS challenges. Base container images must include FIPS-validated cryptographic modules, but standard images typically don’t enable FIPS mode by default.
Red Hat provides Universal Base Images with FIPS mode support. The ubi8-minimal and ubi9-minimal images include necessary packages for FIPS operation. Applications built on these images inherit FIPS-capable cryptography.
Container runtime configuration must also enforce FIPS mode. Docker and containerd can be configured to only run containers with FIPS-enabled base images. Kubernetes admission controllers verify that pod specifications meet FIPS requirements before scheduling.
Multi-stage Docker builds should preserve FIPS configuration across stages. Copying binaries from FIPS-enabled build stages into minimal runtime images can accidentally lose FIPS mode configuration if not carefully managed.
IoT Device Fleet Cryptographic Validation
Internet of Things deployments span thousands or millions of devices that must protect sensitive data using validated cryptography. The resource constraints of IoT devices create challenges for FIPS implementation.
Lightweight FIPS modules specifically designed for embedded systems provide validated cryptography with minimal memory and CPU footprint. wolfSSL and OpenSSL both offer FIPS modules suitable for resource-constrained devices.
Device provisioning workflows must install the validated cryptographic module version during manufacturing or initial deployment. Over-the-air updates that modify cryptographic libraries risk invalidating FIPS status unless updates maintain module version consistency.
Fleet management systems should track which cryptographic module versions each device operates. This inventory enables rapid response if a vulnerability is discovered in a particular module version or if validation certificates expire.
Database Encryption with FIPS Validation
Enterprise databases store vast quantities of sensitive information requiring encryption at rest and in transit. Achieving FIPS validation for database encryption involves multiple layers.
Transparent Data Encryption in SQL Server uses Windows cryptographic modules operating in FIPS mode. Enabling system FIPS policy ensures that TDE relies only on validated cryptography. SQL Server itself holds FIPS 140-2 certificates for its cryptographic implementations.
Oracle Database Advanced Security TDE integrates with hardware security modules through PKCS11 interfaces. Configuring Oracle TDE to use HSM-backed master keys provides FIPS-validated key protection while maintaining encryption key hierarchy within the database.
PostgreSQL encryption using pgcrypto extension must explicitly configure OpenSSL in FIPS mode. The database server requires OS-level FIPS configuration, and applications must verify that encryption operations actually use validated modules.
Cloud-managed databases like Amazon RDS, Azure SQL, and Cloud SQL provide FIPS-validated encryption options. Organizations must review each service’s documentation to confirm validation status and configure appropriate encryption settings.
Keyword Expansion: Related Topics and Questions
Organizations researching FIPS 140-2 frequently explore these related compliance and technical topics:
- NIST Special Publication 800-171 control implementation guidance for defense contractors.
- CMMC Level 2 assessment preparation and evidence collection strategies.
- Hardware security module selection criteria for payment processing and PKI operations.
- Cloud service provider FIPS validation documentation for Azure, AWS, and GCP.
- FedRAMP security control inheritance for cloud-based cryptographic operations.
- OpenSSL FIPS mode configuration and troubleshooting on Linux systems.
- Windows Server FIPS Group Policy settings and application compatibility testing.
- Container orchestration FIPS base images and Kubernetes security policies.
- Code signing certificate storage in FIPS-validated HSMs for software publishers.
- Database transparent data encryption using FIPS modules for compliance.
- Certificate authority operations using validated cryptographic modules.
- VPN and network encryption device FIPS validation for secure communications.
- Mobile device encryption using FIPS-validated cryptographic APIs.
- Cryptographic key management lifecycle aligned with FIPS requirements.
- NIST 800-53 cryptographic protection controls and validation mapping.
- Side-channel attack resistance in higher FIPS security levels.
External Resources
These authoritative resources provide detailed technical specifications and implementation guidance:
- NIST FIPS 140-2 Standard Publication - Official standard specification
- CMVP Validated Modules Search - Database of all validated modules
- NIST SP 800-171 Revision 2 - Protecting CUI requirements
- CMMC Model Overview - Cybersecurity Maturity Model Certification program
- ISO/IEC 19790:2012 - International cryptographic module security standard
Secure Your Cryptographic Infrastructure
Federal contracts require FIPS validation. Defense contractors need CMMC compliance. Technology vendors pursue government market opportunities. But achieving and maintaining cryptographic validation is complex, expensive, and time-consuming.
Qcecuring provides end-to-end cryptographic compliance solutions that accelerate your FIPS validation journey, integrate validated cryptography into cloud infrastructure, automate certificate lifecycle management across your enterprise, and maintain ongoing compliance as standards evolve.
Our team has guided hundreds of organizations through FIPS validation, CMMC assessments, and federal security certifications. We understand the technical requirements, documentation expectations, and operational challenges.
Schedule Your Compliance Assessment →
Final Summary
FIPS 140-2 validation provides the foundation for federal cryptographic security and defense contractor compliance:
- Four security levels address diverse threat models from basic software protection to advanced physical attack resistance
- 11 security requirement areas comprehensively evaluate cryptographic module design, implementation, and operational security
- CMMC Level 2 requires FIPS validation for all cryptography protecting Controlled Unclassified Information under NIST 800-171 control 3.13.11
- FIPS 140-3 transition requires planning for September 2026 sunset with validation timelines of 12-24 months
- Cloud providers offer validated services across AWS, Azure, and GCP with proper configuration required to ensure FIPS mode operation
Organizations should begin FIPS implementation immediately, starting with cryptographic module inventory and progressing through validation planning that addresses timelines, costs, and operational impacts.
Frequently Asked Questions
What’s the difference between FIPS-compliant and FIPS-validated?
FIPS-compliant products use algorithms specified in FIPS standards but haven’t undergone third-party validation testing. FIPS-validated products have completed CMVP testing and hold actual validation certificates. Only FIPS-validated products satisfy federal compliance requirements. Many vendors market products as “FIPS-compliant” because they use approved algorithms, but this doesn’t meet regulatory requirements that explicitly require validation.
How long does FIPS 140-2 validation take?
The complete process typically requires 12-24 months from initial lab engagement to certificate issuance. Algorithm testing through CAVP consumes 1-3 months per algorithm family. Module testing by the accredited laboratory takes 3-9 months depending on complexity and security level. NIST review currently averages 3-6 months. Organizations should plan for 18 months minimum and budget contingency time for any issues discovered during testing.
How much does FIPS validation cost?
Costs vary significantly based on module complexity and security level. Software modules targeting Level 1 typically cost $50,000 to $75,000 for testing lab fees. Hardware modules pursuing Level 3 can require $150,000 to $250,000. Multi-platform validations multiply these costs. Additional expenses include internal engineering time, documentation preparation, potential redesign if issues are found, and ongoing maintenance costs for certificate lifespan.
Do I need FIPS 140-2 or FIPS 140-3?
New validations should target FIPS 140-3. CMVP stopped accepting new FIPS 140-2 submissions in April 2022. Existing FIPS 140-2 certificates remain valid for five years from issuance date, but the standard sunsets in September 2026. Organizations starting validation today should pursue FIPS 140-3 to ensure long-term compliance and avoid needing immediate revalidation after certificate issuance.
Which FIPS security level do I need?
The required level depends on your threat model and regulatory requirements. Level 1 suffices for commercial applications with software-based cryptography. Level 2 applies when tamper-evidence and role-based authentication are needed. Level 3 targets scenarios with physical attack concerns requiring tamper-resistant hardware. Level 4 provides maximum protection for classified systems. Most defense contractors meet CMMC requirements with Level 1 or Level 2 validated modules.
Can I use AWS/Azure/GCP and meet FIPS requirements?
Yes, all major cloud providers offer FIPS 140-2 validated cryptographic services. AWS CloudHSM and KMS use validated modules. Azure Key Vault Premium tier provides HSM-backed validated cryptography. GCP Cloud HSM offers Level 3 validation. However, you must configure services appropriately and document the specific modules and certificates in use. Not all cloud services automatically use FIPS modules—verification and proper configuration are essential.
Does enabling FIPS mode break applications?
Enabling FIPS mode restricts cryptographic operations to approved algorithms, which can break applications relying on non-approved algorithms like MD5, RC4, or SHA-1. Common issues include legacy authentication protocols, certificate validation using SHA-1 signatures, and applications hardcoded to use specific cipher suites. Organizations must test all applications in FIPS mode before production deployment and remediate compatibility issues.
How do I verify a module is actually FIPS-validated?
Search the CMVP validated modules database at csrc.nist.gov using the vendor name, module name, or certificate number. The database shows certificate status, security level, validated platforms, and approved algorithms. Verify that the deployed module version exactly matches the validated version. Some modules have multiple certificates for different versions or platforms—ensure you’re referencing the correct certificate.
What happens when a FIPS certificate expires?
Certificates remain valid for five years from validation date. After expiration, the module moves to the historical list and no longer satisfies federal compliance requirements. Organizations must initiate revalidation before expiration to maintain continuous compliance. Revalidation is a complete new validation—there’s no expedited renewal process. Planning should begin 18-24 months before expiration to ensure certificate continuity.
Does FIPS 140-2 validation cover cloud-based cryptographic operations?
It depends on the deployment model. If you’re using a cloud provider’s cryptographic service like AWS KMS, the provider’s validation covers the service. If you’re running your own cryptographic modules in cloud VMs, you need separate validation for your implementation. Software modules validated for specific operating systems can be deployed in cloud instances of those operating systems, but you must verify the operational environment matches validation certificate requirements.
Ready to Secure Your Enterprise?
Discover how QCecuring can help you automate certificate lifecycle management, secure SSH keys, and protect your cryptographic infrastructure.
