
NIST SP 1800-16 Guidelines: The Enterprise Blueprint for TLS Certificate Management
- Qcecuring Editorial Team
- 01 Jan, 2026
- 04 Mins read
- Security Pki Compliance
NIST SP 1800-16 Guidelines: The Enterprise Blueprint for TLS Certificate Management
Introduction
In the modern enterprise, the “expired certificate” is more than a help desk ticket—it is a ticking clock. When a core TLS certificate expires, the business stops. Revenue-generating web portals go dark, internal microservices lose trust, and security teams scramble to find a replacement in a sea of unmanaged spreadsheets.
The NIST SP 1800-16 guidelines, titled “Securing Web Transactions: TLS Server Certificate Management,” were developed specifically to solve this chaos. This NIST Cybersecurity Practice Guide provides a modular, standards-based blueprint for moving from manual “firefighting” to an automated, resilient Certificate Lifecycle Management (CLM) program.
What This Guide Covers
- The 4-Volume Framework: Understanding how NIST structures the SP 1800-16.
- Risk Mitigation: Identifying threats like CA compromise and server impersonation.
- Reference Architecture: Building a centralized certificate management service.
- Automation Workflows: Implementing ACME and agentless management.
- Vendor Comparison: How DigiCert, Venafi, and Keyfactor align with NIST.
- Actionable Best Practices: 15 steps to a compliant PKI posture.
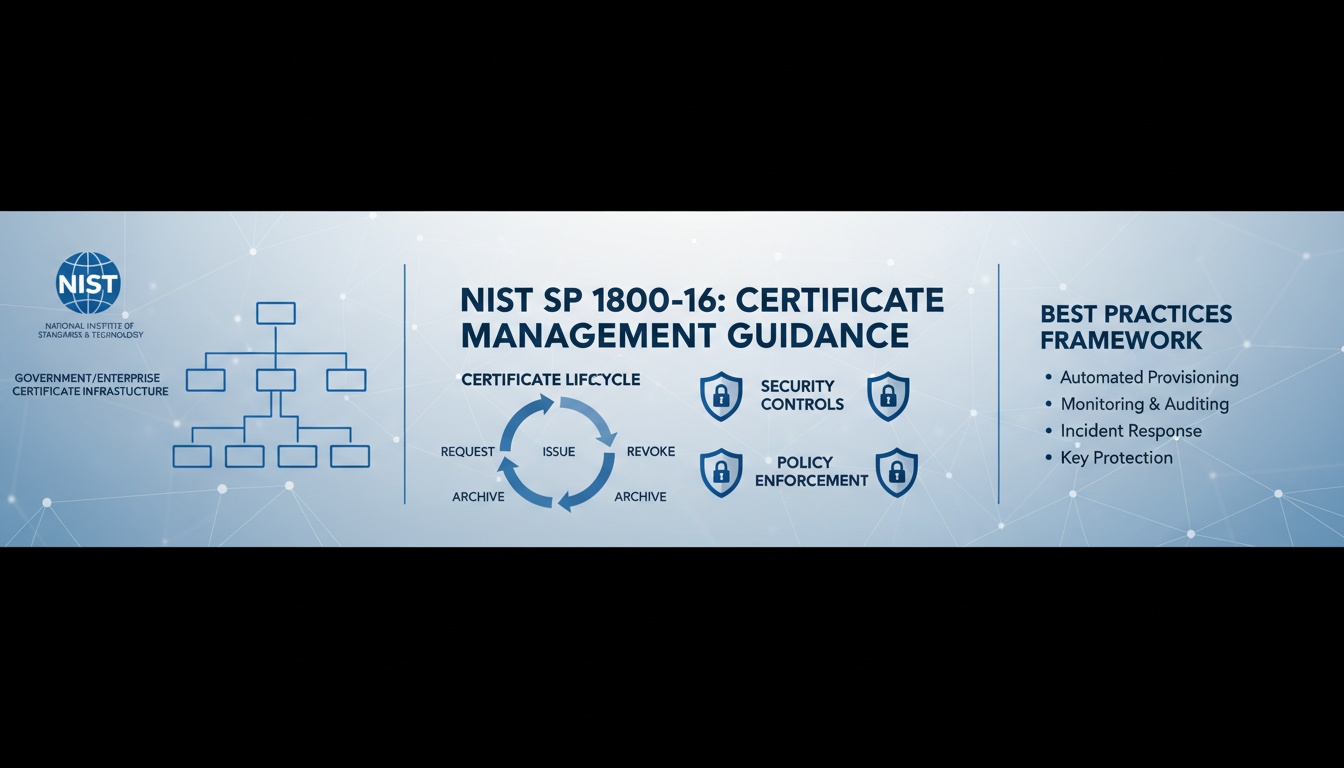
Workflow Diagram Overview of NIST SP 1800-16
The NIST SP 1800-16 framework is built on a continuous loop. Unlike traditional one-off installations, modern machine identity requires a circular workflow to handle the rapid expiration cycles of modern cloud environments.
1. What Is NIST SP 1800-16?
NIST SP 1800-16 is a specialized publication from the National Cybersecurity Center of Excellence (NCCoE). Unlike high-level frameworks, this is a Practice Guide. It doesn’t just tell you what to do; it demonstrates how to do it using commercially available technologies.
The Four Volume Structure
| Volume | Title | Purpose |
|---|---|---|
| Volume A | Executive Summary | High-level business risks and the need for leadership in PKI. |
| Volume B | Security Risks | Deep dive into threats, vulnerabilities, and best practices. |
| Volume C | Approach & Architecture | The logical and physical design of an automated CLM solution. |
| Volume D | How-To Guides | Step-by-step instructions for re-creating the NIST reference implementation. |
2. Why NIST SP 1800-16 Matters Today
We are living in the era of Short-Lived Certificates. With industry trends pushing toward 90-day lifespans, manual management is no longer an option.
Cloud-Native Relevance & Zero Trust
In a Zero Trust Architecture, identity is the new perimeter. Every container, load balancer, and API gateway needs a unique, verifiable identity. NIST SP 1800-16 provides the framework to manage these identities at scale without slowing down DevOps pipelines.
Compliance and Real Enterprise Impact
Failing to follow these guidelines often leads to:
- Application Outages: The #1 cause of preventable downtime.
- Hidden Intrusions: Attackers using their own certificates to masquerade as your servers.
- Data Exfiltration: Malicious actors leveraging encrypted channels to bypass legacy firewalls.
3. How NIST SP 1800-16 Works (Technical Deep Dive)
The core philosophy of NIST SP 1800-16 is Centralization. You cannot manage what you cannot see. The guide proposes a centralized “Certificate Manager” that acts as the brain of your PKI.
The NIST Reference Architecture
The NIST SP 1800-16 reference architecture establishes a centralized, automated framework designed to manage the entire certificate lifecycle and mitigate high-stakes risks. This modular approach relies on five critical pillars:
- Centralized Governance: Eliminate fragmented management across IT silos.
- Automated Discovery: Inventory engines to find “shadow” certificates and maintain a single source of truth.
- Automated Enrollment: Utilizing protocols like ACME or agentless pushes to ensure renewals before expiration.
- Continuous Monitoring: Detecting non-compliant keys or unauthorized changes in real-time.
- Crypto-Agility: The ability to rapidly replace thousands of certificates in response to a CA compromise.
4. Best Practices for Implementation
- Establish a Formal Policy: Define approved CAs and minimum key lengths (RSA 2048+).
- Automate Discovery: Use network-based discovery tools to find “shadow” certificates.
- Enable ACME Protocol: Use the Automated Certificate Management Environment for web server renewals.
- Implement Agentless Management: Use SSH or APIs to push certificates to appliances.
- Rotate Private Keys: Always generate a new key pair during renewal.
- Monitor Certificate Transparency (CT): Watch CT logs for unauthorized issuances.
- Enforce RBAC: Ensure only authorized users can request high-value certificates.
- Prepare for Crypto-Agility: Document your plan to replace all certificates within 24 hours.
- Use HSMs for Root Keys: Store sensitive private keys in Hardware Security Modules.
- Continuous Monitoring: Set up early warning systems (30/60/90 day alerts).
5. Common Pitfalls
- Ignoring Shadow IT: Teams buying certificates outside of central procurement.
- No Ownership Tracking: Certificates expiring because the original requester left the company.
- Manual Installation Errors: Typos in configuration files causing chain-of-trust breaks.
- Over-reliance on Wildcards: Increasing the blast radius of a single key compromise.
- Using Self-Signed Certificates: Breaking the NIST chain of trust in production environments.
6. Advanced Use Cases: DevOps & mTLS
In a Zero Trust environment, NIST SP 1800-16 principles extend to mTLS (mutual TLS). Modern DevOps teams use tools like cert-manager to automate the NIST workflow within Kubernetes environments.
7. External Resources
Primary NIST SP 1800-16 Links
- Official NIST SP 1800-16 Publication (All Volumes)
- NCCoE Project Page
- NIST SP 1800-16 Volume B (Security Risks)
Protocols & Technical Standards
Book a NIST Compliance Demo
Is your organization still managing certificates with spreadsheets and calendar alerts? Qcecuring helps enterprises implement the full NIST SP 1800-16 framework.
Final Summary
- NIST SP 1800-16 is the industry standard for TLS automation.
- Discovery must be continuous to avoid shadow certificates.
- Automation is the only way to handle 90-day certificate lifespans.
- Agility is your best defense against CA compromise.
- Ownership prevents outages caused by employee turnover.
FAQs
1. Is NIST SP 1800-16 mandatory? No, but it is considered the “gold standard” for enterprise PKI audits and federal compliance.
2. How does this relate to NIST SP 800-53? SP 1800-16 provides the specific “how-to” for the technical encryption controls listed in SP 800-53.
3. What is crypto-agility? The ability to switch encryption algorithms or Certificate Authorities across an entire organization instantly.
4. Why is automation required? Manual management fails at scale and cannot support the short lifespans (90 days) becoming the industry norm.
5. Does it cover SSH keys? While focused on TLS, the lifecycle principles (Discovery -> Inventory -> Rotation) apply directly to SSH and machine identities.
Ready to Secure Your Enterprise?
Discover how QCecuring can help you automate certificate lifecycle management, secure SSH keys, and protect your cryptographic infrastructure.
