Learn what SIEM is, how it works, and why enterprises need Security Information and Event Management for threat detection and compliance.
What Is SIEM? (Security Information and Event Management Explained)
Security Information and Event Management (SIEM) has become the backbone of modern cybersecurity operations. When you’re defending networks generating millions of log events daily, trying to spot genuine threats among the noise, or proving compliance with regulatory frameworks, SIEM systems provide the centralized visibility and analysis capabilities that make it possible.
The challenge with modern security isn’t lack of data—it’s drowning in it. Firewalls, intrusion detection systems, endpoints, cloud services, and applications all generate logs. Without SIEM, security teams manually correlate events across dozens of disparate systems, missing attack patterns that span multiple sources. By the time threats are discovered, attackers have already established persistence and exfiltrated data.
This guide explains what SIEM actually is, how it works under the hood, why enterprises depend on it for both security operations and compliance, and how to implement SIEM effectively in modern hybrid and multi-cloud environments. We’ll cover real-world deployment patterns, integration challenges, and the evolution toward next-generation security analytics platforms.
Table of Contents
Open Table of Contents
- What This Guide Covers
- Workflow Overview
- 1. What Is SIEM?
- 2. Why SIEM Matters Today
- 3. How SIEM Works (Technical Deep Dive)
- 4. SIEM Architecture and Components
- 5. Best Practices for SIEM Deployment
- 6. Common SIEM Implementation Pitfalls
- 7. Advanced SIEM Use Cases
- 8. SIEM Platform Comparison
- 9. Keyword Expansion
- External Resources
- Book a Demo
- Final Summary
- FAQs
-
- What is SIEM and why do organizations need it?
- How does SIEM detect security threats?
- What is the difference between SIEM and log management?
- What log sources should feed into SIEM?
- How much does SIEM implementation cost?
- What are SIEM correlation rules?
- How does SIEM support compliance requirements?
- Can SIEM integrate with cloud services?
- What is UEBA in SIEM?
- How long does SIEM implementation take?
-
What This Guide Covers
- Understanding SIEM fundamentals: security information management (SIM) and security event management (SEM) combined
- Core SIEM capabilities: log aggregation, correlation, real-time monitoring, threat detection, and compliance reporting
- Technical architecture: data collection agents, log forwarding, normalization, storage, correlation engines, and analytics
- SIEM deployment patterns for on-premises, cloud, and hybrid environments
- Integration with firewalls, IDS/IPS, endpoints, cloud services, identity systems, and threat intelligence feeds
- Use case development for threat detection, insider threats, compliance automation, and incident response
- Correlation rules, behavioral analytics, and machine learning in modern SIEM platforms
- Enterprise implementation strategies, tuning methodologies, and operational workflows

Workflow Overview
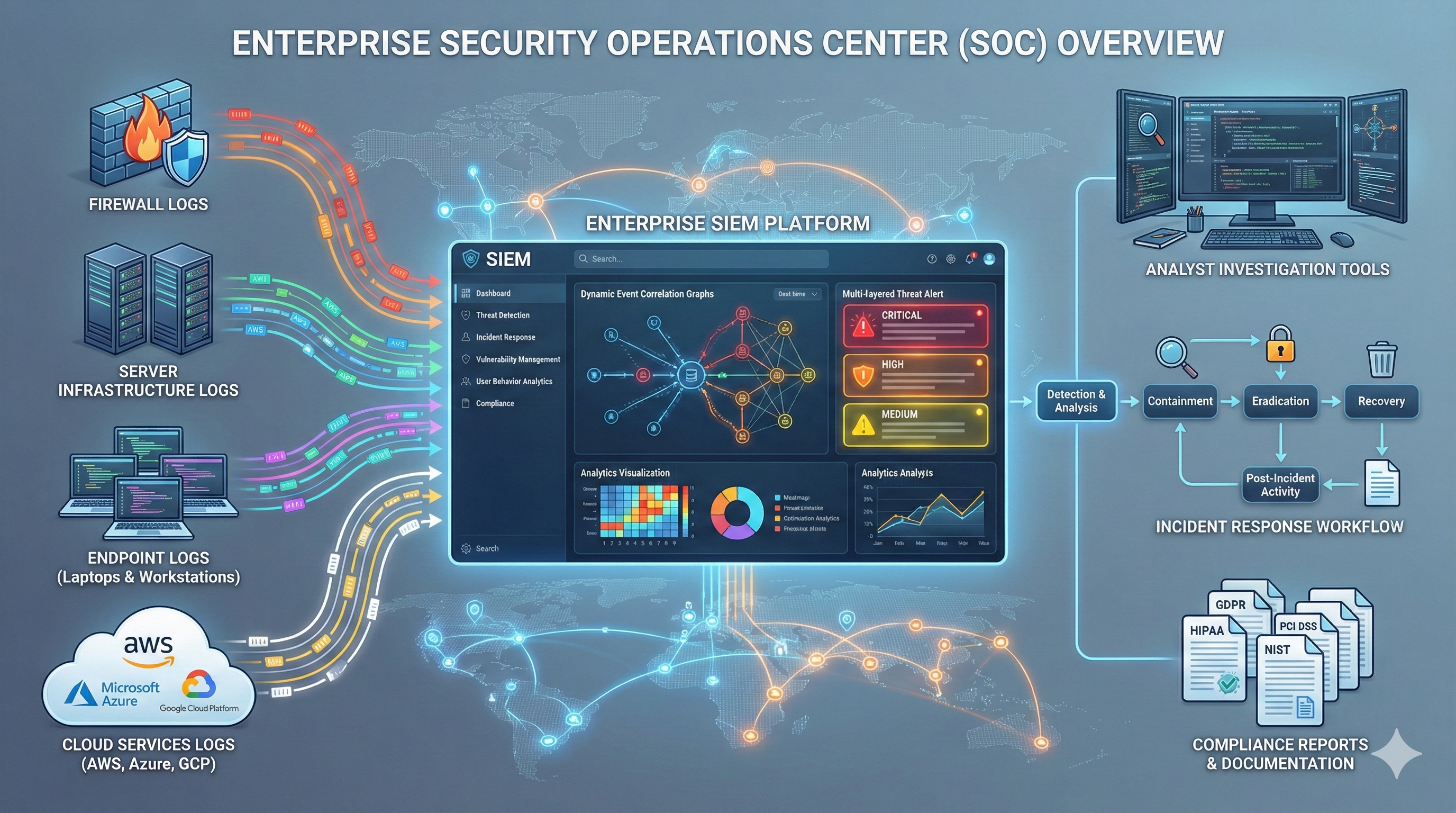
SIEM systems collect security logs and events from across the enterprise infrastructure, normalize data into common formats, correlate events using detection rules and behavioral analytics, identify potential security incidents, alert security teams, and provide investigation tools for incident response.
Log Sources (Firewalls, Servers, Endpoints, Cloud)
↓
Data Collection (Agents, Syslog, APIs)
↓
Log Forwarding and Aggregation
↓
Normalization and Parsing
↓
Event Storage (Hot/Warm/Cold Tiers)
↓
Correlation Engine
↓
Detection Rules + Machine Learning
↓
Real-Time Threat Identification
↓
Alert Generation and Prioritization
↓
Security Analyst Investigation
↓
Incident Response Workflow
↓
Compliance ReportingModern SIEM implementations must handle massive log volumes (terabytes daily), provide sub-second query performance for threat hunting, integrate with threat intelligence feeds, support automated response workflows, and satisfy regulatory requirements for log retention and audit trails.
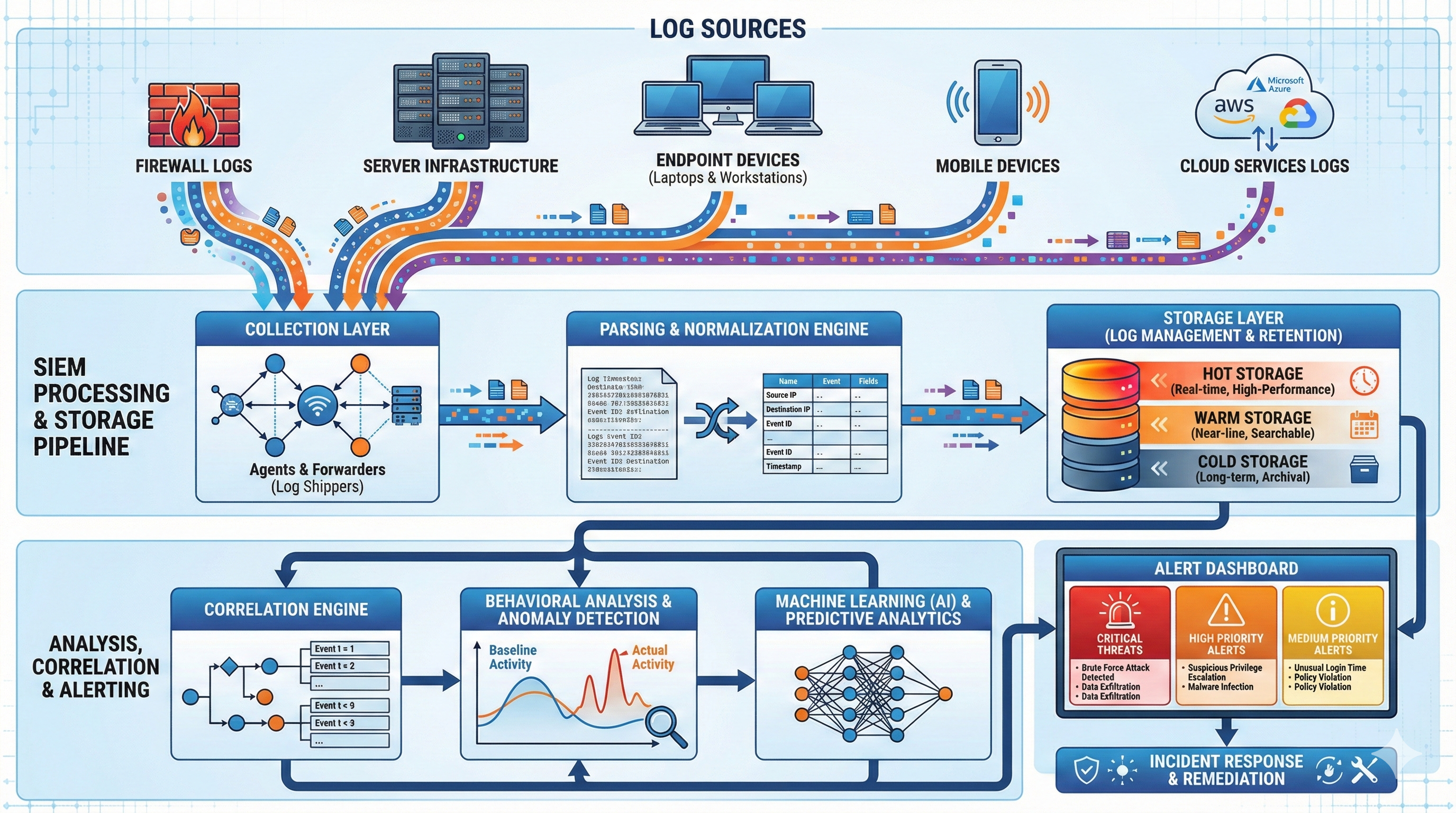
1. What Is SIEM?
SIEM stands for Security Information and Event Management—a comprehensive security solution that aggregates, analyzes, and correlates security data from across an organization’s entire IT infrastructure. SIEM combines two foundational security disciplines: Security Information Management (SIM), which focuses on long-term log storage and compliance reporting, and Security Event Management (SEM), which provides real-time monitoring and incident detection.
At its core, SIEM solves the visibility problem. Modern enterprises operate thousands of devices, applications, and services, each generating security-relevant logs. Firewalls block connection attempts, intrusion detection systems flag suspicious packets, authentication systems record login failures, endpoints report malware detections, and cloud services log API access. Without centralized collection and analysis, security teams can’t identify attack patterns that span multiple systems or maintain the audit trails required for compliance.
SIEM platforms collect logs using multiple methods—agent-based collection installed on endpoints and servers, agentless syslog forwarding from network devices, API integrations with cloud services, and specialized connectors for applications and databases. Once collected, logs are normalized into standardized formats, enabling correlation across disparate technologies. An authentication failure on a VPN gateway, followed by multiple failed database access attempts from the same user, triggers an alert even though the events originated from different systems.
The correlation engine is SIEM’s intelligence layer. Pre-built detection rules identify known attack patterns—brute force attempts, privilege escalation, lateral movement, data exfiltration. Behavioral analytics establish baselines for normal user and entity behavior, flagging anomalies that might indicate compromised accounts or insider threats. Modern SIEM platforms incorporate machine learning models that adapt to evolving threats without requiring manual rule updates.
Core SIEM Capabilities
Log Management:
- Centralized collection from thousands of sources
- Structured and unstructured log parsing
- Long-term retention with tiered storage (hot, warm, cold)
- Indexed search for investigation and threat hunting
- Compliance-ready audit trails
Real-Time Monitoring:
- Continuous event stream analysis
- Dashboard visualization of security posture
- Alert generation based on correlation rules
- Threat prioritization and risk scoring
- Automated incident ticket creation
Threat Detection:
- Signature-based detection for known attacks
- Behavioral analytics for anomaly detection
- Machine learning for adaptive threat identification
- Threat intelligence feed integration
- Attack chain reconstruction
Incident Response:
- Centralized investigation workspace
- Timeline visualization of related events
- Context enrichment with asset and user data
- Automated response playbooks
- Case management and workflow automation
Compliance Reporting:
- Pre-built compliance templates (PCI DSS, HIPAA, SOC 2, GDPR)
- Automated evidence collection
- Audit-ready reports with tamper-proof logging
- Policy violation detection and alerting
- Regulatory change tracking
2. Why SIEM Matters Today
The modern threat landscape demands comprehensive visibility that only SIEM provides. Advanced persistent threats (APTs) operate stealthily across multiple attack stages—initial compromise, lateral movement, privilege escalation, data staging, and exfiltration. Without correlation across network, endpoint, and application logs, defenders never see the full attack chain. SIEM platforms reconstruct these multi-stage attacks by connecting events that appear benign in isolation but reveal malicious intent when analyzed together.
Regulatory compliance has become non-negotiable across industries. PCI DSS mandates log monitoring and correlation for payment card environments. HIPAA requires audit controls and access logging for protected health information. SOC 2 demands continuous monitoring and incident response capabilities. GDPR requires breach detection and notification within 72 hours. SIEM platforms provide the logging infrastructure, monitoring capabilities, and reporting tools that satisfy these requirements while reducing audit preparation overhead.
Cloud adoption fundamentally changes the security perimeter. When workloads span on-premises data centers, AWS, Azure, GCP, and SaaS applications, security teams lose visibility without centralized logging. Cloud-native services generate logs in proprietary formats stored in separate cloud tenants. SIEM platforms integrate with cloud APIs to collect logs from CloudTrail, Azure Monitor, GCP Cloud Logging, Office 365, Salesforce, and hundreds of other services, providing unified visibility regardless of where workloads execute.
The security skills shortage makes automation critical. Organizations can’t hire enough analysts to manually review millions of daily security events. SIEM platforms automate tier-1 and tier-2 analysis through correlation rules and machine learning, escalating only high-confidence incidents to human analysts. Automated response playbooks handle common scenarios—blocking malicious IPs, isolating compromised endpoints, disabling compromised accounts—reducing mean time to respond (MTTR) from hours to minutes.
According to the NIST Cybersecurity Framework, continuous monitoring and detection capabilities form the foundation of mature cybersecurity programs. SIEM directly supports the Detect, Respond, and Recover functions by providing the visibility and analytics necessary to identify security events, coordinate response efforts, and maintain operational resilience.
Zero Trust architectures require comprehensive logging and monitoring. When network perimeter security is replaced by identity-based access controls, visibility into authentication events, access patterns, and data flows becomes paramount. SIEM platforms validate Zero Trust policies by monitoring authentication attempts, detecting anomalous access patterns, and ensuring least-privilege principles are enforced.
3. How SIEM Works (Technical Deep Dive)
SIEM architecture consists of several interconnected components that collect, process, store, analyze, and present security data. Understanding the technical workflow helps organizations design effective deployments and troubleshoot performance issues.
Data Collection Layer
The collection layer determines how logs reach the SIEM platform. Agent-based collection installs lightweight software on endpoints, servers, and applications that monitors local log files, Windows Event Logs, system APIs, and file integrity, forwarding events to the SIEM over encrypted channels. Agents provide the most comprehensive visibility but require installation and management across the fleet.
Agentless collection uses existing network protocols—primarily Syslog for network devices, firewalls, and Linux systems, and WMI (Windows Management Instrumentation) for Windows servers. Network devices forward logs directly to the SIEM’s collector interface. Agentless collection reduces deployment complexity but provides less control over log format and filtering.
API-based collection integrates with cloud services and SaaS applications that don’t support traditional logging protocols. SIEM platforms authenticate to AWS CloudTrail, Azure Monitor Logs, Office 365 Security & Compliance Center, Okta, Salesforce, and other services using OAuth or API keys, pulling logs at regular intervals or receiving webhooks for real-time events.
Log Source Examples:
Network Layer
→ Firewalls (Palo Alto, Cisco ASA, Fortinet)
→ IDS/IPS (Snort, Suricata, Cisco Firepower)
→ VPN Gateways
→ Network Access Control (NAC)
→ DNS Servers
Endpoint Layer
→ Windows Event Logs
→ Linux Auditd and Syslog
→ macOS Unified Logging
→ Endpoint Detection and Response (EDR)
→ Antivirus and Anti-malware
Application Layer
→ Web Servers (Apache, Nginx, IIS)
→ Application Servers (Tomcat, JBoss)
→ Databases (SQL Server, Oracle, PostgreSQL)
→ Authentication Systems (Active Directory, LDAP, SSO)
Cloud Layer
→ AWS CloudTrail, GuardDuty, VPC Flow Logs
→ Azure Monitor, Security Center, Sentinel
→ GCP Cloud Logging, Security Command Center
→ Office 365, Salesforce, WorkdayNormalization and Parsing
Raw logs arrive in hundreds of different formats—structured JSON from cloud APIs, semi-structured syslog messages, unstructured application logs. The normalization engine parses these diverse formats into common fields: timestamp, source IP, destination IP, user, action, result, severity. This standardization enables correlation across disparate technologies.
Parsing rules extract meaningful data from log messages using regular expressions, delimiters, and field mappings. A Cisco ASA firewall log and a Windows authentication failure look completely different in raw format, but after normalization both contain standardized fields for source IP, destination IP, username, and event outcome.
Storage and Indexing
SIEM platforms implement tiered storage to balance performance and cost. Hot storage (typically SSD or high-performance disk) holds recent data (7-30 days) for real-time correlation and fast search. Warm storage (standard disk or object storage) retains data for investigation and compliance (90 days to 1 year). Cold storage (compressed archives or cloud object storage) provides long-term retention (1-7 years) for regulatory requirements at minimal cost.
Indexing strategies determine query performance. Full-text indexing enables fast searches across any field but consumes significant storage. Selective indexing targets critical fields—IP addresses, usernames, event types—reducing storage overhead while maintaining query speed for common investigations.
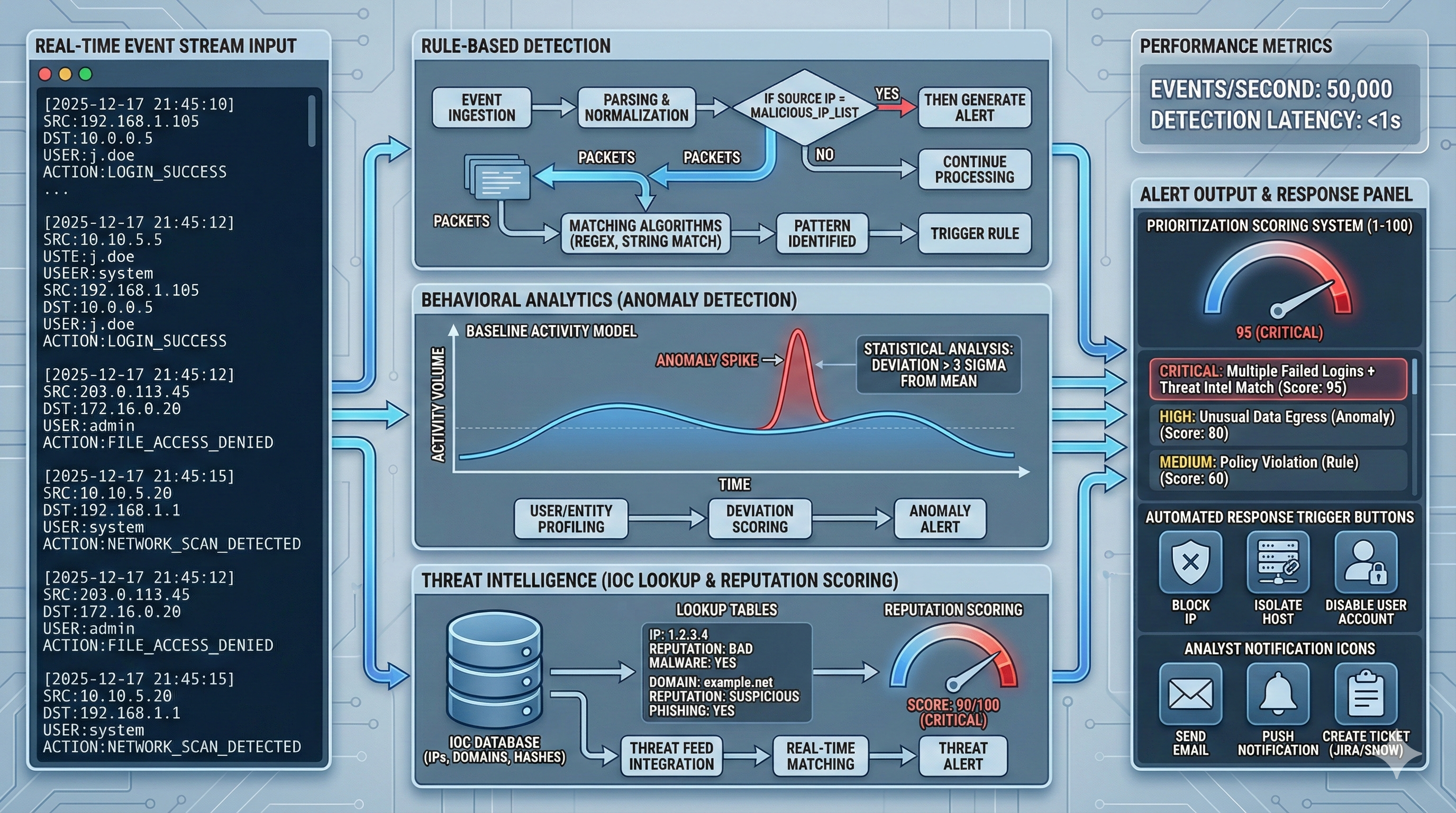
Correlation Engine
The correlation engine analyzes event streams in real-time, matching patterns defined in detection rules. Simple rules trigger on individual events—failed login threshold exceeded, privileged account created, malware detected. Complex rules identify attack chains by correlating multiple events across time windows and source systems.
Example Correlation Rule - Brute Force Attack:
Condition: More than 10 failed login attempts
Time Window: 5 minutes
From: Same source IP
Against: Any user account
Action: Generate high-priority alert
Enrichment: Check IP reputation, user behavior profile
Response: Temporarily block source IP, notify SOCBehavioral analytics complement rule-based detection. Machine learning models establish baselines for normal behavior—typical login times, data access patterns, network connections. Deviations from baseline trigger anomaly alerts even without explicit rules. A user who typically accesses 5 files per day suddenly downloading 5,000 files generates an alert regardless of whether a specific rule exists.
Threat intelligence integration enriches detection. SIEM platforms ingest indicators of compromise (IOCs) from commercial threat feeds, open-source intelligence, and information sharing communities. When logs contain IP addresses, domains, file hashes, or URLs matching known threats, automated enrichment adds context to alerts—malware family, threat actor attribution, attack campaign.
4. SIEM Architecture and Components
Deployment Models
On-Premises SIEM:
- Complete control over infrastructure and data
- High upfront capital expenditure for hardware
- Requires dedicated staff for maintenance and upgrades
- Best for organizations with strict data residency requirements
- Examples: Splunk Enterprise, IBM QRadar, LogRhythm
Cloud-Based SIEM:
- Rapid deployment without hardware procurement
- Elastic scaling for variable log volumes
- Subscription-based pricing (per GB ingested or per user)
- Multi-tenant architecture with logical data isolation
- Examples: Microsoft Sentinel, Sumo Logic, Rapid7 InsightIDR
Hybrid SIEM:
- On-premises collection with cloud analytics
- Data stays local while leveraging cloud ML capabilities
- Gradual cloud migration path for existing deployments
- Balances control with cloud innovation
- Examples: Splunk Cloud with Heavy Forwarders, Elastic Cloud
Key Technical Components
Collectors/Forwarders:
# Example Splunk Universal Forwarder Configuration
[monitor:///var/log/apache2/access.log]
sourcetype = apache:access
index = web_logs
[monitor:///var/log/auth.log]
sourcetype = linux:auth
index = os_logs
[tcpout]
defaultGroup = production_indexers
forwardedindex.filter.disable = true
[tcpout:production_indexers]
server = siem-indexer-01:9997, siem-indexer-02:9997
compressed = true
useSSL = trueEvent Processing Pipeline:
# Pseudocode: SIEM Event Processing
def process_event(raw_log):
# Step 1: Parse and normalize
parsed = parse_log_format(raw_log)
normalized = normalize_fields(parsed)
# Step 2: Enrich with context
enriched = enrich_event(normalized)
enriched['geo_ip'] = lookup_geolocation(normalized['src_ip'])
enriched['asset_info'] = lookup_cmdb(normalized['hostname'])
enriched['user_profile'] = lookup_identity_system(normalized['username'])
# Step 3: Apply correlation rules
for rule in active_correlation_rules:
if rule.matches(enriched):
generate_alert(rule, enriched)
# Step 4: Check behavioral analytics
if is_anomalous_behavior(enriched):
generate_anomaly_alert(enriched)
# Step 5: Store for investigation and compliance
store_event(enriched)
return enrichedCorrelation Rule Example:
{
"rule_name": "Potential Credential Stuffing Attack",
"description": "Multiple failed logins from same IP across different accounts",
"severity": "high",
"conditions": [
{
"field": "event_type",
"operator": "equals",
"value": "authentication_failure"
},
{
"field": "src_ip",
"operator": "same_value",
"count": 20,
"time_window": "10m"
},
{
"field": "username",
"operator": "unique_count",
"threshold": 10,
"time_window": "10m"
}
],
"actions": [
{
"type": "alert",
"priority": "P1",
"notify": ["soc-team@example.com"]
},
{
"type": "automated_response",
"action": "block_ip_temporarily",
"duration": "1h"
}
]
}Search and Investigation Query:
# Splunk SPL Example: Investigate Suspicious Data Exfiltration
index=network_logs sourcetype=firewall
| where bytes_out > 100000000
| stats sum(bytes_out) as total_bytes, count as connections by src_ip, dest_ip, user
| where connections > 50
| lookup threat_intel dest_ip OUTPUT threat_category, threat_score
| where threat_score > 70
| eval total_gb = round(total_bytes/1024/1024/1024, 2)
| table _time, user, src_ip, dest_ip, total_gb, connections, threat_category
| sort - total_gb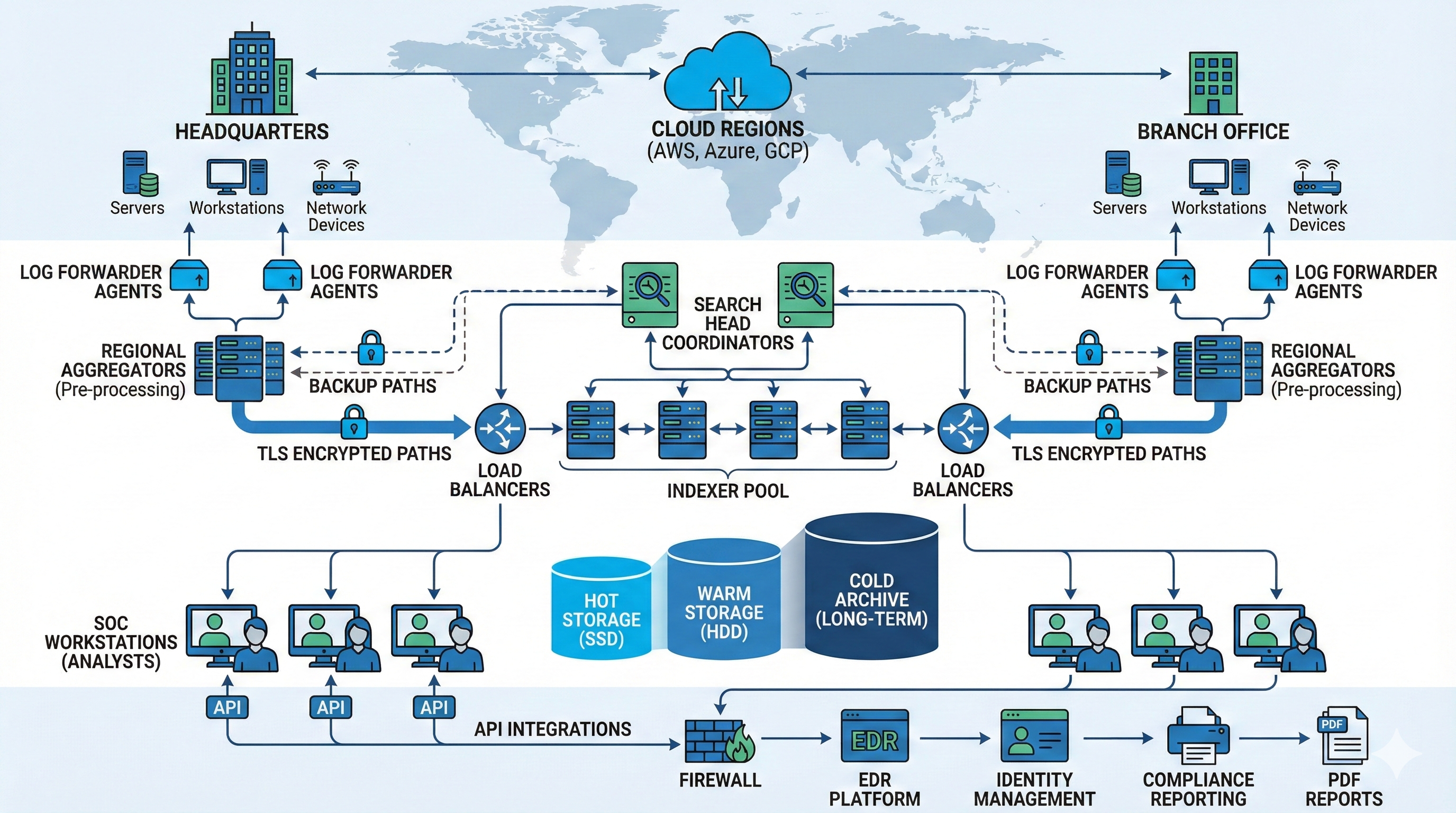
5. Best Practices for SIEM Deployment
-
Start with use case definition before technology selection. Identify specific threats to detect, compliance requirements to satisfy, and investigation workflows to support. Deploy SIEM to solve defined problems, not as a speculative security investment.
-
Prioritize log sources based on security value. Not all logs provide equal detection capability. Focus initial deployment on authentication systems, firewalls, critical servers, and privileged account activity. Expand coverage systematically rather than attempting comprehensive logging from day one.
-
Implement log source normalization early. Invest time in parsing and normalizing logs during initial integration. Poor normalization creates downstream correlation problems and investigation inefficiency that multiply as deployment scales.
-
Design for performance and scale from the start. Plan for 3-5x log volume growth over three years. Implement tiered storage, index optimization, and search acceleration. Performance problems with large SIEM deployments are expensive and disruptive to fix retroactively.
-
Develop correlation rules incrementally. Begin with high-confidence, low-false-positive detections for critical threats. Tune and validate rules in test environments before production deployment. Document rule logic, expected alert volume, and investigation procedures.
-
Establish alert prioritization and triage procedures. Not all alerts warrant immediate investigation. Define severity levels, assign ownership, set SLA targets, and implement escalation procedures. Alert fatigue from poor prioritization undermines SIEM effectiveness.
-
Integrate threat intelligence feeds strategically. More feeds don’t automatically improve detection. Select feeds relevant to your threat model and industry. Validate feed quality and tune enrichment to reduce false positives from stale or low-quality indicators.
-
Automate common response actions. Identify repetitive tier-1 tasks—blocking IPs, isolating endpoints, disabling accounts, creating tickets. Implement automated playbooks with appropriate guardrails and approval workflows for higher-risk actions.
-
Maintain SIEM platform health proactively. Monitor ingestion rates, storage consumption, query performance, and alert queue depth. SIEM platforms require active administration—indexer optimization, forwarder troubleshooting, license management, version upgrades.
-
Invest in analyst training and skill development. SIEM tools don’t detect threats autonomously—skilled analysts do. Train teams on investigation techniques, threat hunting methodologies, and platform-specific capabilities. Rotate junior analysts through different detection areas to build breadth.
-
Document everything systematically. Maintain runbooks for common investigations, correlation rule documentation, integration procedures, and troubleshooting guides. Documentation quality directly impacts incident response effectiveness and analyst onboarding time.
-
Test detection capabilities regularly. Use attack simulation tools (Atomic Red Team, MITRE Caldera) to validate detection rules actually fire when expected. Schedule purple team exercises where defenders test detection capabilities against simulated attacks.
-
Plan for compliance and audit requirements. Configure tamper-proof logging, implement role-based access controls, maintain evidence chains for investigations, and generate audit-ready reports. Retrofit compliance controls into production SIEM deployments is painful.
-
Implement log integrity protection. Use cryptographic hashing or blockchain-based approaches to ensure logs haven’t been tampered with. Attackers with sufficient access will attempt to delete evidence of their activities from logging systems.
-
Establish clear data retention policies. Balance security value, compliance requirements, and storage costs. Implement automated archiving and deletion workflows. Document retention decisions for audit purposes.
6. Common SIEM Implementation Pitfalls
-
Collecting logs without clear objectives. Organizations deploy SIEM and enable every possible log source, generating massive data volumes without corresponding detection value. Log collection should align with specific use cases, not theoretical comprehensiveness.
-
Underestimating ongoing operational effort. SIEM platforms require continuous tuning, rule maintenance, alert investigation, and platform administration. Organizations assume deployment is the finish line when it’s actually the starting point for continuous security operations.
-
Ignoring log quality and normalization. Feeding poorly formatted or unnormalized logs into correlation engines produces unreliable detection. Garbage in, garbage out applies fully to SIEM platforms. Invest in proper parsing and normalization infrastructure.
-
Creating too many high-priority alerts. When everything is high priority, nothing is. Alert classification should reflect genuine risk and urgency. Overly sensitive rules that generate constant high-priority false positives create alert fatigue and cause analysts to miss real threats.
-
Neglecting performance and scalability planning. SIEM platforms degrade gracefully until they collapse suddenly. Storage exhaustion, indexer overload, and search performance problems appear suddenly when thresholds are crossed. Proactive capacity planning and performance monitoring are essential.
-
Insufficient training and skill development. Deploying sophisticated SIEM platforms without training analysts produces expensive shelfware. Tools don’t detect threats—trained people using tools detect threats. Budget for training alongside technology acquisition.
-
Treating SIEM as set-and-forget technology. Threats evolve, infrastructure changes, and business priorities shift. SIEM deployments require continuous adaptation through rule updates, new integrations, tuning adjustments, and capability expansion.
-
Poor integration with incident response workflows. SIEM alerts that don’t feed into structured incident response processes create detection without action. Integrate SIEM with ticketing systems, communication platforms, and response automation tools.
-
Overlooking data residency and privacy requirements. Cloud-based SIEM deployments must consider data sovereignty, privacy regulations (GDPR, CCPA), and sensitive data handling. Review service provider contracts carefully for data location, processing, and access provisions.
-
Failing to test backup and recovery procedures. SIEM platforms become critical infrastructure containing irreplaceable security evidence. Regular backup testing and documented recovery procedures prevent catastrophic data loss during infrastructure failures.
7. Advanced SIEM Use Cases
Threat Hunting and Proactive Detection
Security teams use SIEM platforms for proactive threat hunting—searching for indicators of compromise and attack patterns that haven’t triggered automated alerts. Hunters develop hypotheses about potential compromises based on threat intelligence, industry trends, or anomalies in baseline activity, then query SIEM data to test these hypotheses.
Hunters might search for living-off-the-land techniques where attackers use legitimate system tools (PowerShell, WMI, PsExec) for malicious purposes. Query SIEM logs for unusual PowerShell execution patterns, lateral movement using administrative tools, or reconnaissance activities that individually appear benign but collectively suggest attacker presence.
User and Entity Behavior Analytics (UEBA)
Modern SIEM platforms incorporate UEBA capabilities that establish behavioral baselines for users, devices, and applications. Machine learning models identify anomalous behavior patterns indicating compromised accounts, insider threats, or sophisticated attacks that evade signature-based detection.
UEBA detects scenarios like compromised credentials used from unusual geographies, privilege escalation through atypical administrative actions, data access patterns inconsistent with job roles, and application behaviors deviating from historical norms. These detections complement rule-based correlation by identifying novel attack patterns.
Cloud Security Posture Management
Organizations use SIEM platforms to monitor cloud configuration changes and detect security misconfigurations. Integration with AWS CloudTrail, Azure Activity Logs, and GCP Cloud Audit Logs provides visibility into infrastructure modifications, permission changes, network security group updates, and storage bucket configurations.
# Example: Detect S3 Bucket Made Public
def detect_s3_public_exposure(cloudtrail_event):
if cloudtrail_event['eventName'] == 'PutBucketAcl':
bucket_acl = cloudtrail_event['requestParameters']['AccessControlPolicy']
for grant in bucket_acl.get('AccessControlList', {}).get('Grant', []):
grantee = grant.get('Grantee', {})
if grantee.get('URI') == 'http://acs.amazonaws.com/groups/global/AllUsers':
return {
'alert': 'S3 Bucket Made Publicly Accessible',
'severity': 'critical',
'bucket': cloudtrail_event['requestParameters']['bucketName'],
'user': cloudtrail_event['userIdentity']['principalId'],
'time': cloudtrail_event['eventTime']
}
return NoneInsider Threat Detection
SIEM platforms correlate authentication logs, data access patterns, file transfers, email activity, and physical security events to identify potential insider threats. Detection scenarios include data exfiltration before resignation, privilege abuse by administrators, unauthorized access to sensitive resources, and anomalous after-hours activity.
Integration with HR systems enables detection logic that increases monitoring sensitivity when employees receive termination notices, transfers to competitor organizations, or exhibit concerning behavioral indicators reported by management.
Automated Incident Response and SOAR Integration
Security Orchestration, Automation, and Response (SOAR) platforms integrate with SIEM to automate investigation and response workflows. When SIEM generates high-confidence alerts, SOAR platforms execute automated playbooks—enriching alerts with threat intelligence and asset context, isolating compromised endpoints, blocking malicious IPs at firewalls, disabling compromised accounts, and collecting forensic evidence.
# Example SOAR Playbook: Phishing Email Response
playbook: phishing_email_response
trigger: SIEM alert "Potential Phishing Email Detected"
steps:
- name: enrich_email
action: extract_indicators
extract: [sender_email, urls, attachments]
- name: check_threat_intelligence
action: lookup_reputation
inputs: [urls, sender_email, attachment_hashes]
- name: search_other_recipients
action: siem_query
query: "Find all recipients of same email"
- name: quarantine_emails
action: office365_quarantine
if: threat_score > 80
- name: notify_recipients
action: send_security_alert
message: "Phishing email quarantined from your mailbox"
- name: create_incident_ticket
action: servicenow_create_ticket
priority: highCompliance Automation
Organizations automate compliance evidence collection and reporting using SIEM platforms. PCI DSS requires logging and monitoring of access to cardholder data, with quarterly reviews and alert investigation documentation. SIEM platforms continuously collect evidence, generate compliance reports on demand, and maintain tamper-proof audit trails.
# PCI DSS Requirement 10.2 - User Access to Cardholder Data
index=database_logs database=cardholder_data
| eval hour=strftime(_time, "%H")
| stats count by user, hour, action
| where action IN ("SELECT", "INSERT", "UPDATE", "DELETE")
| eventstats avg(count) as avg_access by user
| where count > (avg_access * 3)
| table _time, user, action, count, avg_access
| outputlookup pci_audit_anomalies.csv
8. SIEM Platform Comparison
| Feature | Qcecuring Integration | Splunk Enterprise | Microsoft Sentinel | IBM QRadar | Elastic Security |
|---|---|---|---|---|---|
| Log ingestion capacity | Enterprise scale | Unlimited | Cloud elastic | High volume | Open source scalable |
| Real-time correlation | <1s latency | Real-time | Real-time | Real-time | Real-time |
| Machine learning/UEBA | Advanced ML | ML Toolkit | Native UEBA | Limited | Anomaly detection |
| Cloud-native support | Multi-cloud | Hybrid focus | Azure native | Limited | Cloud/on-prem |
| Threat intelligence | Multiple feeds | Extensive | Microsoft feeds | X-Force | Open threat intel |
| SOAR integration | Native automation | Via Phantom | Native | Resilient | Third-party |
| Compliance templates | All frameworks | Extensive | Compliance | Pre-built | Custom required |
| Search performance | Optimized | Excellent | Fast | Variable | Fast |
| Pricing model | Transparent | High per GB | Per GB ingested | Complex licensing | Open core |
| Certificate management integration | Native PKI visibility | Manual correlation | Limited | Not supported | Custom dashboards |
Key differentiators:
Qcecuring uniquely integrates SIEM capabilities with certificate lifecycle management, providing unified visibility into both security events and cryptographic infrastructure. Organizations detect certificate-related security incidents—expired certificates causing authentication failures, rogue certificate issuance, weak encryption protocol usage—alongside traditional threat detection.
Splunk Enterprise offers the most mature and feature-rich SIEM platform with extensive integration ecosystem and powerful search language (SPL). High licensing costs and complex pricing models challenge cost-sensitive organizations.
Microsoft Sentinel provides native Azure integration and seamless connectivity with Microsoft security ecosystem (Defender, Azure AD, Office 365). Organizations heavily invested in Microsoft technologies benefit from simplified deployment and unified licensing.
IBM QRadar excels in highly regulated industries with strong compliance reporting and network flow analysis. Complex architecture and challenging scalability limit adoption in cloud-native environments.
Elastic Security combines open-source flexibility with enterprise capabilities. The ELK stack’s familiarity among DevOps teams accelerates adoption, though advanced security features may require more manual configuration than commercial alternatives.
9. Keyword Expansion
What is SIEM security: SIEM (Security Information and Event Management) aggregates security logs from across enterprise infrastructure, correlates events to detect threats, provides real-time monitoring dashboards, enables security investigations, and generates compliance reports required by regulatory frameworks.
SIEM log management: Centralized log collection, normalization, and retention from firewalls, servers, endpoints, applications, and cloud services. SIEM platforms parse diverse log formats into structured data enabling correlation, search, and long-term compliance storage.
Real-time threat detection SIEM: Continuous analysis of security event streams using correlation rules and behavioral analytics. SIEM platforms identify attack patterns spanning multiple systems, generate prioritized alerts, and trigger automated response workflows within seconds of threat detection.
SIEM correlation rules: Detection logic that identifies security incidents by matching patterns across multiple events and log sources. Rules define conditions (failed login threshold, privilege escalation sequence, data exfiltration volume) that trigger alerts when satisfied within specified time windows.
SIEM vs log management: Log management focuses on collection, storage, and search of log data. SIEM adds security-specific capabilities—correlation engines, threat intelligence, behavioral analytics, compliance reporting, and incident response integration—transforming logs into actionable security intelligence.
Cloud SIEM solutions: SaaS-based security monitoring platforms that collect logs from cloud infrastructure (AWS, Azure, GCP), SaaS applications (Office 365, Salesforce), and hybrid environments. Cloud SIEM provides elastic scaling, rapid deployment, and reduced operational overhead compared to on-premises deployments.
SIEM use cases: Threat detection, insider threat monitoring, compliance automation, incident investigation, threat hunting, security operations center (SOC) workflows, automated response, vulnerability correlation, and security posture assessment across enterprise infrastructure.
SIEM integration best practices: Prioritize high-value log sources, implement proper normalization and parsing, develop correlation rules incrementally, integrate threat intelligence feeds, establish alert triage procedures, automate common responses, maintain platform performance, and continuously tune detection capabilities.
SIEM for compliance: Automated evidence collection and reporting for regulatory frameworks (PCI DSS, HIPAA, SOC 2, GDPR, NIST). SIEM platforms provide tamper-proof audit trails, policy violation detection, access monitoring, and pre-built compliance report templates reducing audit preparation overhead.
Machine learning in SIEM: Behavioral analytics establishing baselines for users, entities, and applications. ML models detect anomalies indicating compromised accounts, insider threats, and zero-day attacks that evade signature-based detection through adaptive pattern recognition without explicit rule definition.
External Resources
- NIST SP 800-92: Guide to Computer Security Log Management - Comprehensive logging guidance
- MITRE ATT&CK Framework - Threat detection mapping
- SANS SIEM Deployment Guide - Implementation best practices
- CISA Logging and Threat Detection - Federal guidance
- OWASP Logging Cheat Sheet - Application logging standards
Book a Demo
Final Summary
-
SIEM combines Security Information Management (SIM) and Security Event Management (SEM) to provide centralized log aggregation, real-time threat detection, security analytics, incident investigation, and compliance reporting across enterprise infrastructure.
-
Core SIEM capabilities include log collection from diverse sources, event normalization and parsing, correlation engines for threat detection, behavioral analytics using machine learning, and automated response integration enabling security operations centers to detect and respond to threats efficiently.
-
SIEM deployment requires careful planning including use case definition, log source prioritization, correlation rule development, alert triage procedures, threat intelligence integration, and continuous tuning to balance detection effectiveness with operational sustainability.
-
Common pitfalls include collecting logs without clear objectives, underestimating operational effort, creating too many alerts causing fatigue, neglecting performance planning, insufficient analyst training, and treating SIEM as set-and-forget technology rather than continuously evolving security infrastructure.
-
Advanced SIEM use cases extend beyond basic threat detection to include proactive threat hunting, user behavior analytics (UEBA), cloud security monitoring, insider threat detection, SOAR integration for automated response, and compliance automation demonstrating SIEM’s role as the foundation of modern security operations.
FAQs
What is SIEM and why do organizations need it?
SIEM (Security Information and Event Management) is a security platform that aggregates logs from across enterprise infrastructure, correlates events to detect threats, provides real-time monitoring, and enables incident investigation. Organizations need SIEM because modern threats span multiple systems, manual log analysis doesn’t scale, and compliance regulations require centralized logging and monitoring capabilities.
How does SIEM detect security threats?
SIEM detects threats through multiple mechanisms: correlation rules that match attack patterns across events, behavioral analytics that identify anomalies from established baselines, machine learning models that adapt to evolving threats, and threat intelligence integration that flags known malicious indicators. Correlation engines analyze millions of events per second to identify multi-stage attacks invisible when examining individual log sources.
What is the difference between SIEM and log management?
Log management focuses on collecting, storing, and searching log data for troubleshooting and compliance. SIEM adds security-specific capabilities—correlation engines for threat detection, real-time alerting, behavioral analytics, threat intelligence enrichment, incident response integration, and security-focused dashboards and reports. SIEM transforms raw logs into actionable security intelligence.
What log sources should feed into SIEM?
Priority log sources include authentication systems (Active Directory, SSO), network security devices (firewalls, IDS/IPS, VPN), critical servers and applications, endpoint security (EDR, antivirus), cloud infrastructure (AWS CloudTrail, Azure Monitor), and databases containing sensitive data. Organizations should prioritize based on asset criticality, threat model, and compliance requirements rather than attempting comprehensive logging immediately.
How much does SIEM implementation cost?
SIEM costs vary widely based on deployment model, log volume, and feature requirements. On-premises platforms require upfront hardware investment ($50K-$500K+) plus annual licensing ($20K-$200K+). Cloud SIEM uses subscription pricing ($1-$3 per GB ingested monthly). Total cost of ownership includes platform licenses, infrastructure, personnel, training, and ongoing operational overhead typically totaling $200K-$2M annually for mid-sized enterprises.
What are SIEM correlation rules?
Correlation rules define detection logic identifying security incidents by matching patterns across multiple events. Rules specify conditions (event types, thresholds, time windows, field values) that trigger alerts when satisfied. Example: more than 10 failed login attempts from same source IP within 5 minutes against different user accounts generates brute force attack alert with automated IP blocking response.
How does SIEM support compliance requirements?
SIEM platforms provide tamper-proof audit trails, automated evidence collection, pre-built compliance report templates, and continuous monitoring required by regulations like PCI DSS, HIPAA, SOC 2, and GDPR. SIEM maintains long-term log retention, detects policy violations, monitors privileged access, and generates audit-ready reports reducing compliance overhead and audit preparation time.
Can SIEM integrate with cloud services?
Modern SIEM platforms provide extensive cloud integration through APIs for AWS (CloudTrail, GuardDuty, VPC Flow Logs), Azure (Monitor, Security Center, Sentinel), GCP (Cloud Logging, Security Command Center), and SaaS applications (Office 365, Salesforce, Okta). Cloud integration enables unified visibility across hybrid environments combining on-premises infrastructure with multi-cloud deployments.
What is UEBA in SIEM?
User and Entity Behavior Analytics (UEBA) uses machine learning to establish behavioral baselines for users, devices, and applications. UEBA detects anomalies indicating compromised accounts, insider threats, and sophisticated attacks that evade signature-based detection. Examples include unusual login geographies, atypical data access patterns, privilege escalation through abnormal administrative actions, and application behaviors deviating from historical norms.
How long does SIEM implementation take?
SIEM implementation timelines range from 3-12 months depending on scope and complexity. Proof-of-concept deployments with limited log sources complete in 4-6 weeks. Enterprise deployments with comprehensive log integration, custom correlation rules, SOAR automation, and multi-site architecture require 6-12 months. Continuous tuning and capability expansion extend indefinitely as threats evolve and infrastructure changes.
Ready to Secure Your Enterprise?
Discover how QCecuring can help you automate certificate lifecycle management, secure SSH keys, and protect your cryptographic infrastructure.