Learn how cloud-based PKI works, why it matters, its benefits, challenges, and best practices for secure certificate management.
Table of Contents
Open Table of Contents
- 1. Introduction
- 2. Understanding the Core Concept of Cloud-Based PKI
- 3. How Cloud-Based PKI Works
- 4. Real-World Applications of Cloud-Based PKI
- 5. Benefits of Cloud-Based PKI
- 6. Challenges and Limitations
- 7. Best Practices for Implementing Cloud-Based PKI
- 8. Future Outlook for Cloud-Based PKI
- 9. Conclusion
1. Introduction
Public Key Infrastructure has quietly become one of the most critical foundations of modern digital security. From encrypted websites and secure emails to device authentication and cloud-native applications, PKI enables trust at internet scale.
As organizations move workloads to the cloud, adopt DevOps pipelines, and manage millions of short-lived certificates, traditional on-premises PKI models increasingly struggle to keep pace. Cloud-based PKI—also known as PKI-as-a-Service—emerged to address these challenges by shifting the operational and infrastructure burden to specialized providers while preserving cryptographic trust.
Understanding cloud-based PKI is no longer optional. It is now a core building block for secure digital transformation.
2. Understanding the Core Concept of Cloud-Based PKI
2.1 What Cloud-Based PKI Is
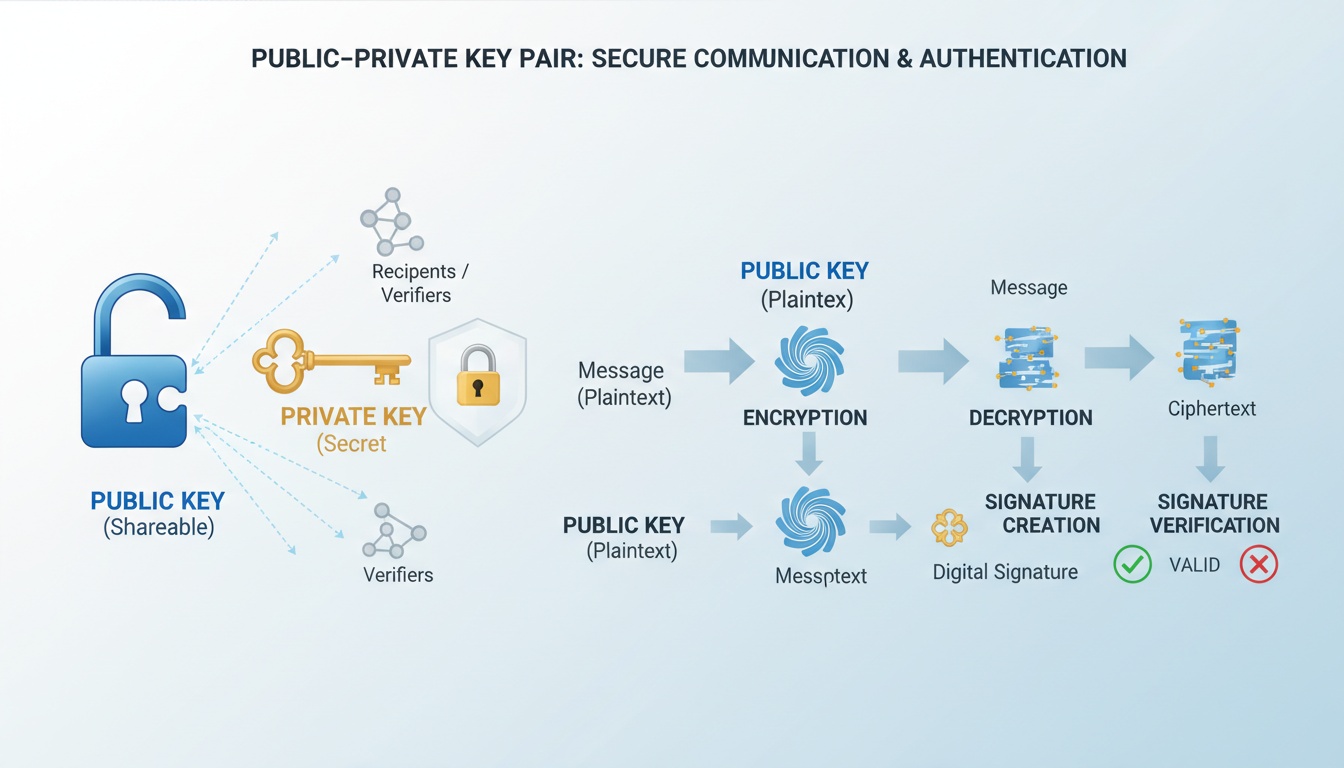
Cloud-based PKI refers to a Public Key Infrastructure that is hosted, operated, and maintained in a cloud environment by a service provider. Instead of deploying certificate authorities, hardware security modules, and management software on-premises, organizations consume PKI capabilities as an on-demand service.
At its core, the cryptographic principles remain unchanged. Certificates are issued, keys are generated and protected, and trust chains are enforced. What changes is where and how this infrastructure is delivered and managed.
2.2 Why Cloud-Based PKI Exists
PKI was originally designed for static environments with predictable growth. Modern IT environments look very different. Certificate lifetimes are shrinking, automation is mandatory, and systems scale dynamically across regions and providers.
Cloud-based PKI exists to solve several persistent problems:
- Operational complexity of managing certificate authorities at scale
- High upfront costs of secure hardware and skilled personnel
- Difficulty adapting on-prem PKI to cloud-native and API-driven workflows
- Increased risk of outages caused by expired or mismanaged certificates
By abstracting infrastructure and maintenance, cloud-based PKI allows organizations to focus on using trust—not running it.
3. How Cloud-Based PKI Works
Cloud-based PKI operates as a layered service rather than a single system. The provider maintains the underlying cryptographic infrastructure, while customers interact through secure management interfaces and APIs.
The process typically begins with establishing a certificate authority hierarchy in the cloud. Root and intermediate CAs are created and protected, often using FIPS-compliant hardware security modules. These keys never leave secure boundaries, even though they are remotely managed.
Once the trust hierarchy is in place, certificates are issued dynamically to users, machines, applications, or services. Integration protocols such as ACME, SCEP, and EST allow certificates to be requested and renewed automatically, aligning PKI with modern DevOps and cloud-native practices.
Lifecycle management is continuous rather than episodic. Certificates are monitored, rotated, revoked, and replaced automatically based on policy, reducing human error and service disruption.
4. Real-World Applications of Cloud-Based PKI
Cloud-based PKI is used wherever large-scale, automated trust is required.
In cloud and hybrid environments, it secures communication between microservices, APIs, and containers. In DevOps pipelines, it enables automated certificate issuance for short-lived workloads. Enterprises rely on it to authenticate users, devices, and workloads without manual provisioning.
Industries such as finance, healthcare, manufacturing, and government use cloud PKI to protect sensitive data, comply with regulations, and support secure remote access. It also plays a growing role in IoT ecosystems, where managing device identities at scale is otherwise impractical.
5. Benefits of Cloud-Based PKI
From a security perspective, cloud-based PKI improves consistency and reduces risk. Policies are enforced centrally, cryptographic standards are kept current, and certificate expirations are less likely to cause outages.
Operationally, it removes the burden of maintaining complex infrastructure. Updates, backups, and high availability are handled by the provider, freeing internal teams to focus on higher-value work.
From a business standpoint, cloud-based PKI reduces total cost of ownership. Organizations avoid large capital investments and instead consume PKI as a scalable service that grows with demand.
Perhaps most importantly, cloud-based PKI aligns trust with automation. It enables security to move at the same speed as modern applications.
6. Challenges and Limitations
Despite its advantages, cloud-based PKI is not without trade-offs. Organizations relinquish some control over infrastructure and must rely on the provider’s security practices and operational transparency.
Customization may be limited, particularly when proprietary APIs or standardized workflows do not fully align with existing systems. Integration with legacy environments can also present challenges.
Regulatory and jurisdictional concerns must be carefully evaluated. Data residency, compliance obligations, and audit requirements vary across regions, making provider selection a critical decision.
Cloud-based PKI follows a shared responsibility model. While the provider secures the platform, customers remain responsible for access control, policy configuration, and governance.
7. Best Practices for Implementing Cloud-Based PKI
Successful cloud PKI deployments begin with clear requirements. Organizations should define their trust models, compliance needs, and integration points before selecting a provider.
Strong access controls are essential. Role-based access control, multi-factor authentication, and comprehensive auditing help protect sensitive certificate operations.
Automation should be embraced deliberately. Integrating certificate lifecycle management into CI/CD pipelines and cloud platforms reduces risk but requires disciplined policy design.
Finally, organizations should treat PKI as a living system. Regular reviews, monitoring, and testing ensure that trust infrastructure evolves alongside business and threat landscapes.
8. Future Outlook for Cloud-Based PKI
Cloud-based PKI is poised to become even more central as certificate volumes grow and environments become more distributed. Shorter certificate lifetimes, zero trust architectures, and machine identities will continue to drive adoption.
Emerging technologies such as post-quantum cryptography are likely to be introduced first in cloud-based PKI platforms, where algorithms and policies can be updated centrally.
As organizations prioritize agility and resilience, PKI delivered as a cloud-native service will increasingly define how digital trust is established and maintained.
9. Conclusion
Cloud-based PKI represents a fundamental shift in how organizations build and operate trust infrastructure. By moving PKI into the cloud, enterprises gain scalability, automation, and resilience that traditional models struggle to provide.
While it introduces new considerations around control and governance, cloud-based PKI has become a practical and often necessary evolution for modern security architectures. Understanding its design, benefits, and limitations is essential for anyone responsible for securing digital systems today.
Ready to modernize your PKI? Contact our experts to learn how cloud-based PKI can transform your certificate management operations.
Ready to Secure Your Enterprise?
Discover how QCecuring can help you automate certificate lifecycle management, secure SSH keys, and protect your cryptographic infrastructure.