Unprotected SSH keys can expose critical systems. Learn why SSH key security and proper authentication are essential.
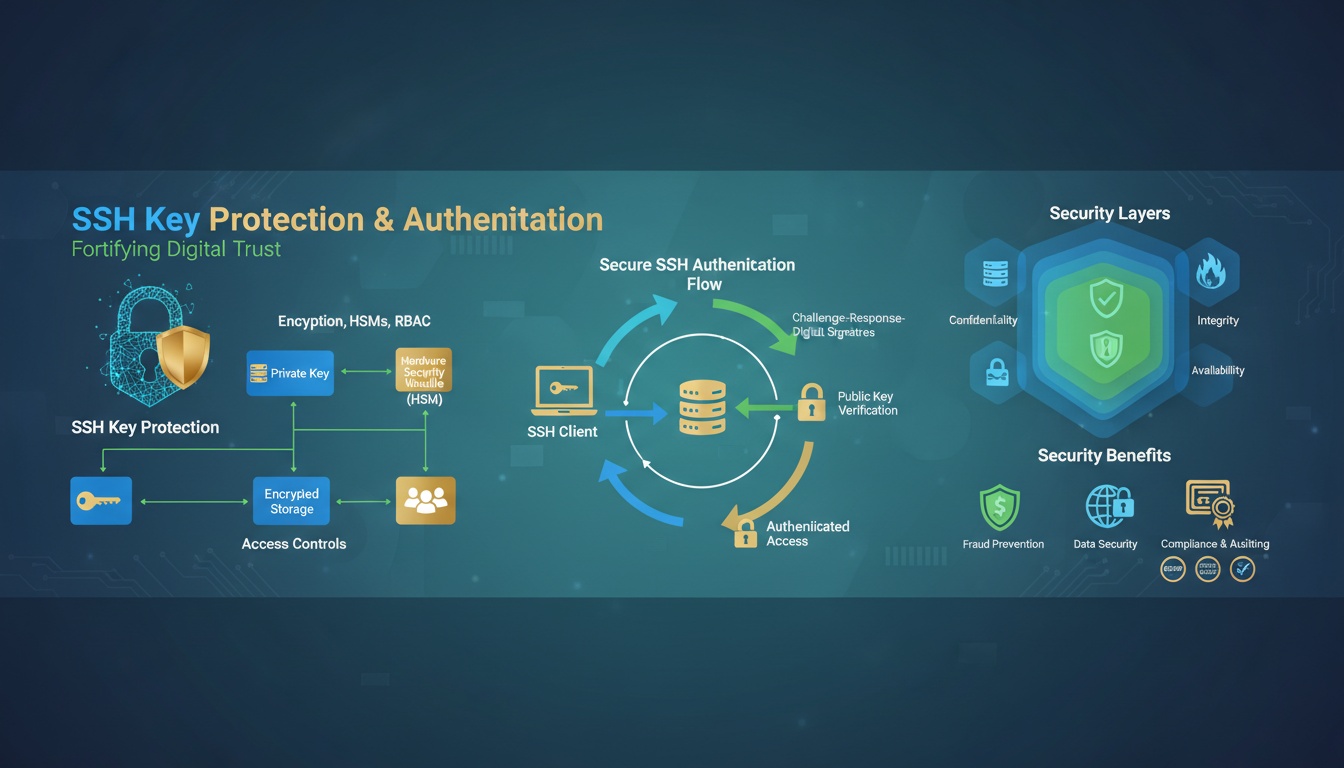
SSH keys often provide privileged access to critical systems such as servers, databases, and network devices. In large organizations, millions of SSH keys may exist, many of which are unmanaged or undocumented.
Unused or forgotten SSH keys can act as hidden access paths into an environment. Keys that are never rotated may rely on outdated cryptographic algorithms, increasing the risk of compromise.
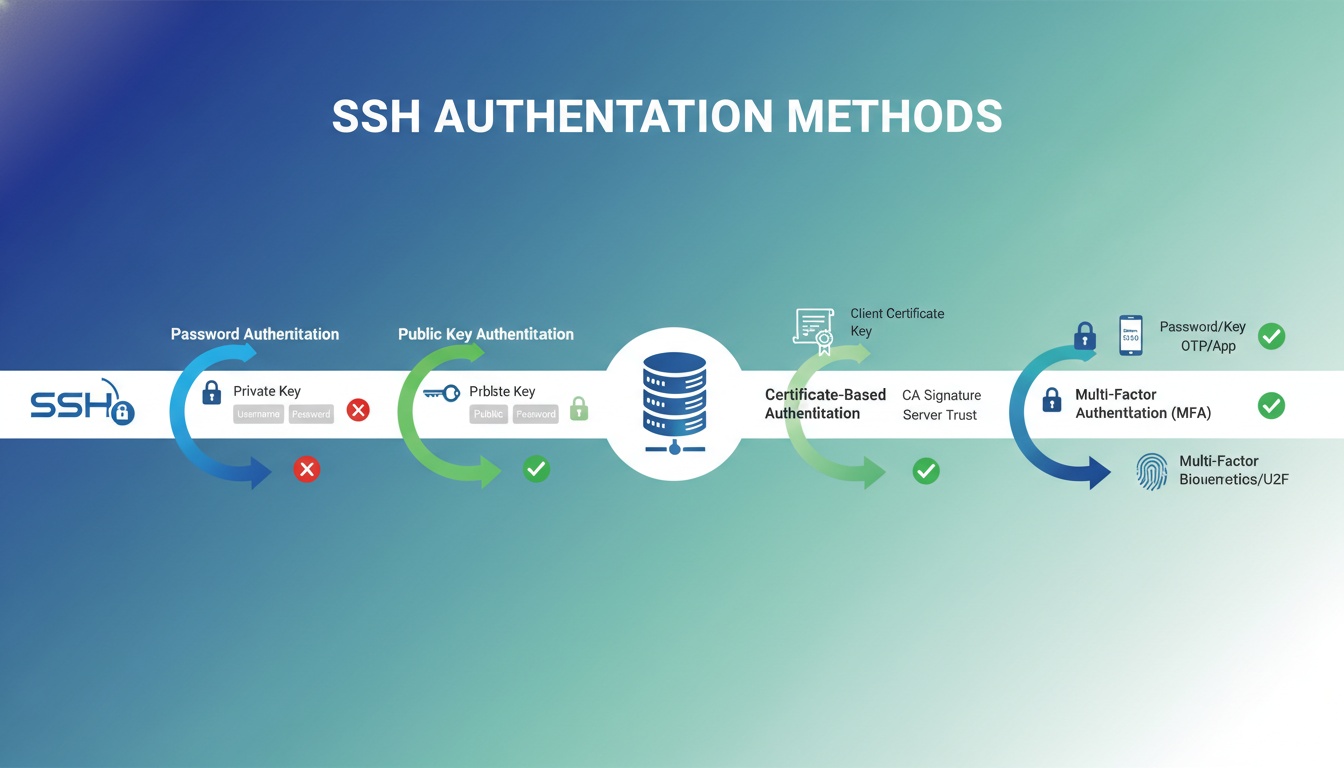
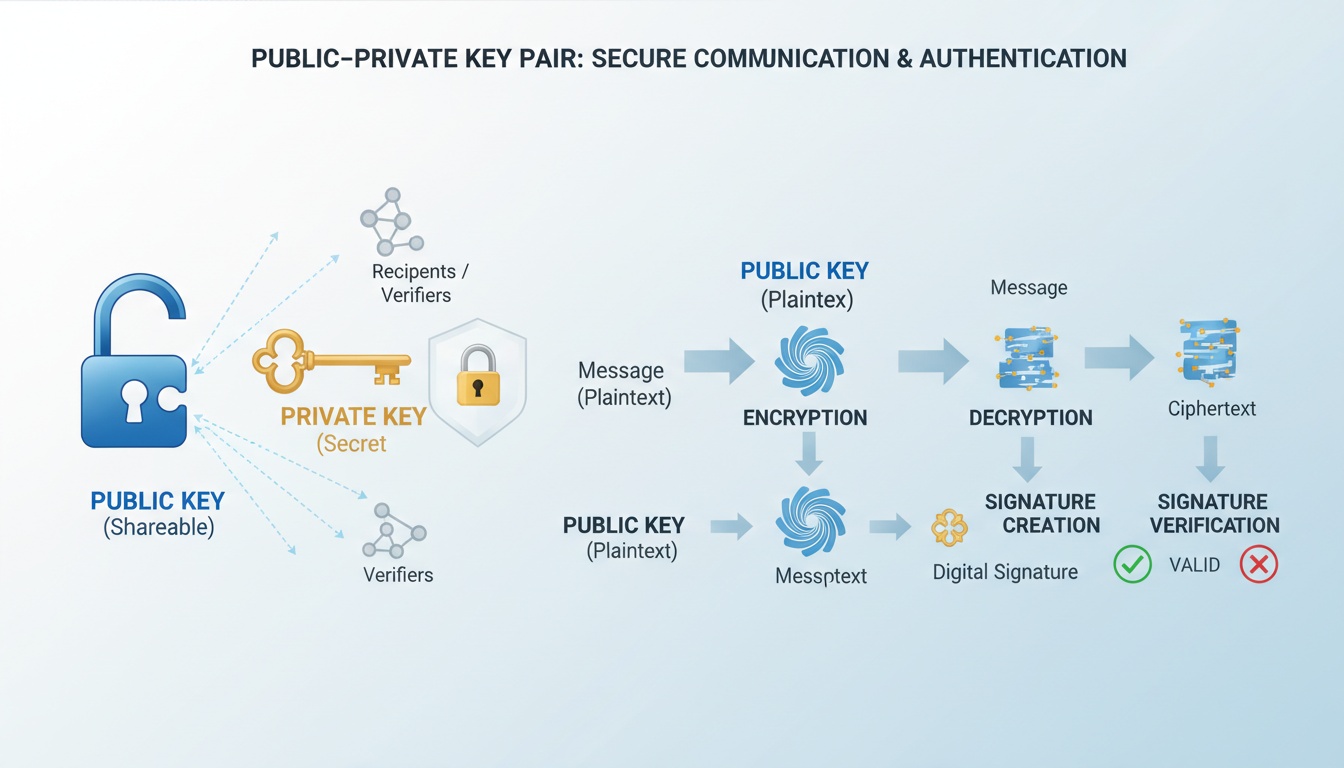
SSH supports both password-based and public key-based authentication. Password-based authentication relies on shared secrets and is vulnerable to brute-force attacks and credential reuse. Public key-based authentication is more secure because the private key never leaves the client system.
By protecting SSH keys through discovery, rotation, access controls, and auditing—and by favoring key-based authentication—organizations can significantly reduce the risk of unauthorized access and lateral movement within their infrastructure.
Ready to Secure Your Enterprise?
Discover how QCecuring can help you automate certificate lifecycle management, secure SSH keys, and protect your cryptographic infrastructure.