Understanding the foundation of encryption, security, and key lifecycle control
Introduction
Modern cybersecurity depends on one fundamental element: cryptographic keys. These keys secure data, authenticate systems, and enable trusted communication across cloud, on-prem, and hybrid environments. Without proper key management, even the strongest encryption collapses.
As threats rise and architectures scale, organizations require a reliable, automated, and compliant way to manage keys throughout their lifecycle.
What This Guide Covers
- Definition of key management
- Why key management is critical
- Deep technical architecture
- Key lifecycle workflow
- Real commands and config examples
- Best practices & pitfalls
- Advanced use cases
- Keyword expansion
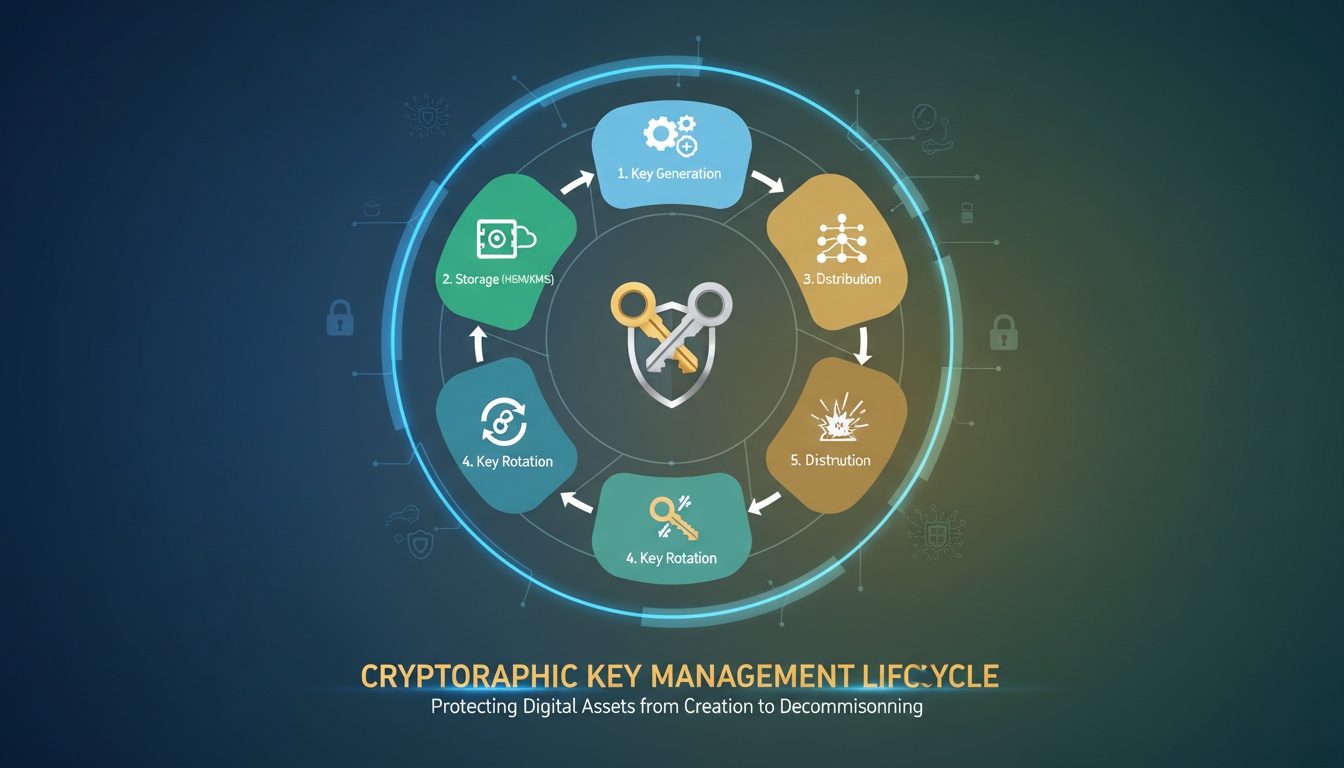
Workflow Diagram — Key Management Lifecycle
1. What Is Key Management?
Key management is the end-to-end process of creating, storing, distributing, rotating, protecting, and retiring encryption keys used in cryptographic operations.
What Problem Does It Solve?
- Prevents data exposure
- Eliminates weak manual practices
- Ensures regulatory compliance
- Enables secure machine identity
Where It Is Used?
- Cloud KMS
- Databases
- IoT
- TLS/SSL
- Code signing
Who Needs It?
- Enterprises
- SaaS
- DevOps
- Governments
2. Why Key Management Matters Today
- Protects encrypted data
- Enables Zero Trust
- Supports cloud-native architectures
- Reduces key theft risk
- Prevents outages due to expired keys
References:
- NIST SP 800-57
- CISA
- OWASP
3. How Key Management Works
Key Generation
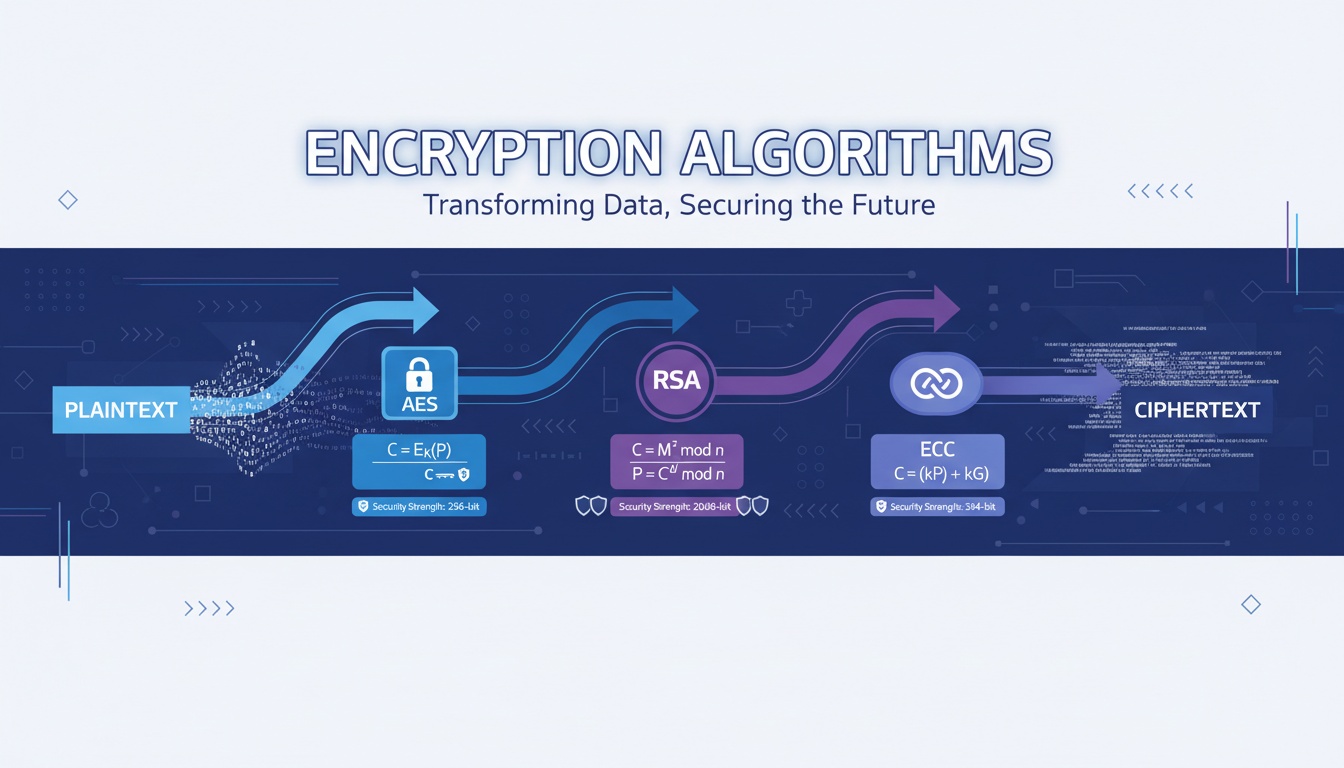
Secure random generation using RSA, ECC, AES, Ed25519.
Key Storage
HSMs, KMS, TPMs, vaults.
Key Distribution
mTLS, envelope encryption.
Key Rotation
Cryptoperiod-based renewal.
Key Revocation
Disable and destroy compromised keys.
4. Architecture Workflow
- App requests key
- KMS authenticates
- HSM generates key
- Key is wrapped with KEK
- App receives wrapped key
- Logs updated
- Rotation occurs
- Key retired
5. Code Examples
openssl rand -base64 32 > data-key.binopenssl genrsa -out kek-private.pem 4096from cryptography.hazmat.primitives import serialization
with open("kek-private.pem", "rb") as f:
key = serialization.load_pem_private_key(f.read(), password=None)
print(key.key_size)6. Best Practices
- Use HSMs
- Enforce least privilege
- Rotate keys
- Separate KEKs and DEKs
- Audit all access
- Avoid static keys
7. Common Pitfalls
- Hardcoded keys
- Weak RNG
- Missing rotation
- No alerts
- Expired certificates
8. Advanced Use Cases
- Cloud KMS
- IoT provisioning
- CI/CD automation
- Container signing
9. Keyword Expansion Zone
- Private key management
- Cryptographic key management
- Key encryption key management
- Secure key management
- Cloud key management service
Comparison Table
| Feature | Manual | Modern KMS |
|---|---|---|
| Rotation | Rare | Automated |
| Storage | File | HSM |
| Auditing | None | Full |
External Resources
https://www.nist.gov
https://www.cisa.gov
https://www.cloudflare.com/learning
https://learn.microsoft.com/security
https://www.rfc-editor.org
Looking to implement secure, scalable certificate lifecycle automation across your enterprise? Qcecuring helps you modernize PKI, SSH, SSL, and code signing workflows with cloud-native automation.
https://qcecuring.com/request-demo
Final Summary
- Key management is essential for encryption.
- Controls full lifecycle of keys.
- Modern systems require automation.
- Prevents breaches & outages.
- Cloud requires scalable KMS.
Ready to Secure Your Enterprise?
Discover how QCecuring can help you automate certificate lifecycle management, secure SSH keys, and protect your cryptographic infrastructure.