Learn about Hardware Security Modules, how they protect cryptographic keys, and their role in enterprise security.
What are Hardware Security Modules (HSM)?
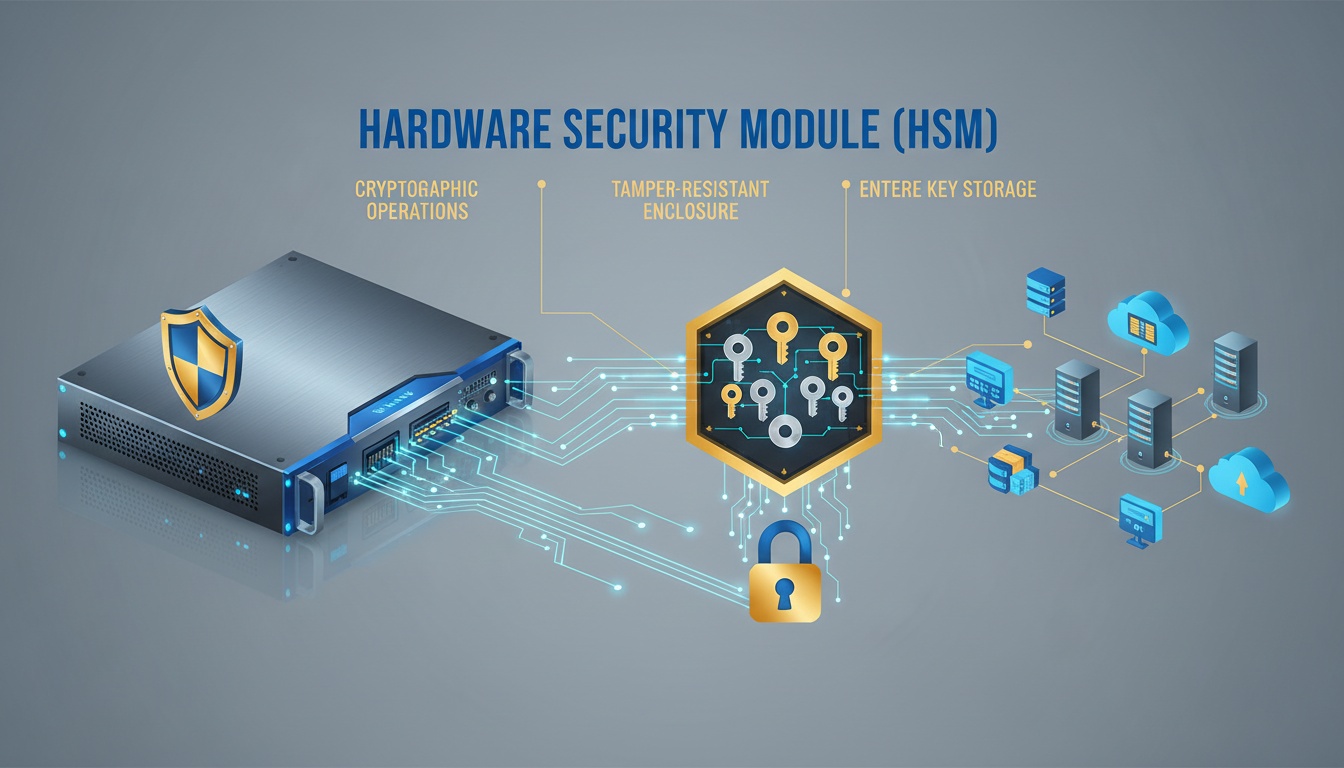
Hardware Security Modules (HSMs) are dedicated hardware devices designed to securely generate, store, and manage cryptographic keys. HSMs provide the highest level of security for sensitive cryptographic operations and are essential for protecting critical keys in enterprise environments.
Understanding HSMs
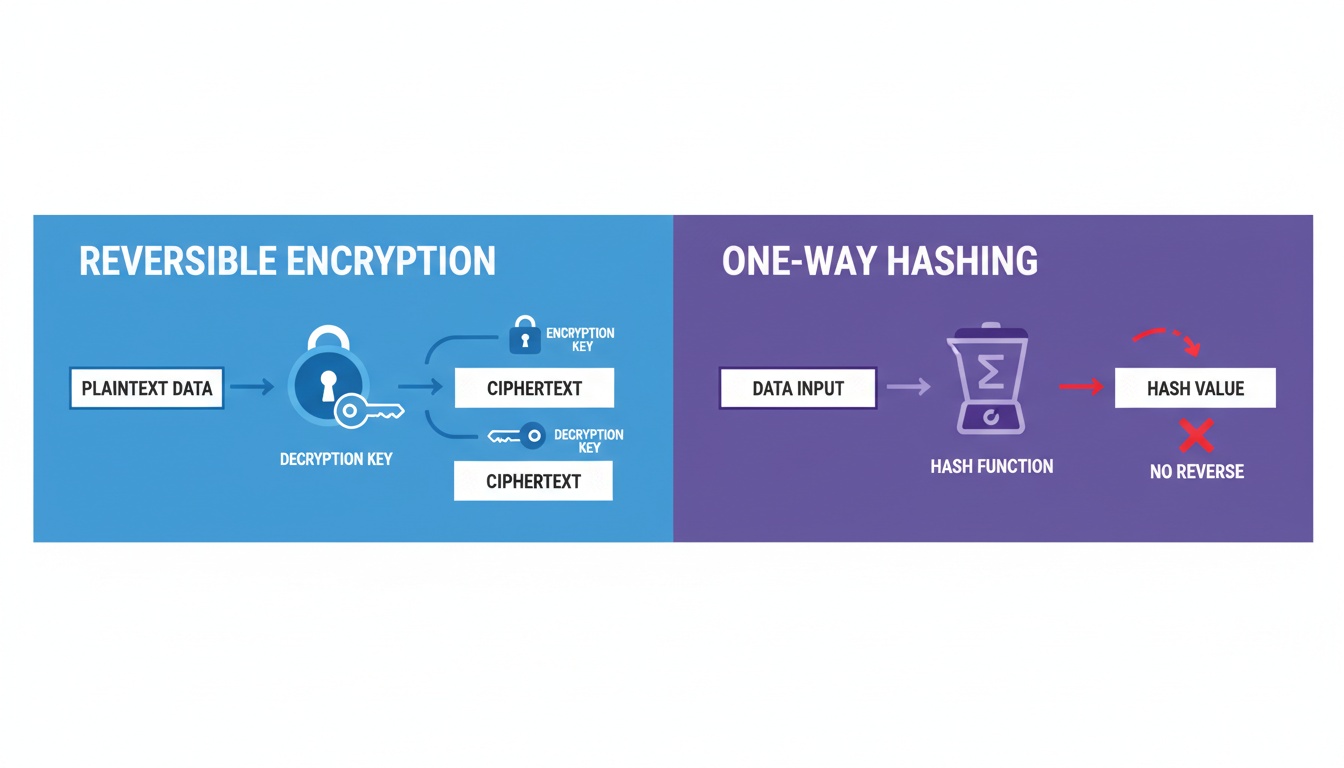
An HSM is a tamper-resistant hardware device that performs cryptographic operations in a secure, isolated environment. Unlike software-based key storage, HSMs protect keys from both logical and physical attacks.
Key Functions of HSMs
Key Generation
HSMs generate cryptographically strong random keys using hardware-based random number generators, ensuring keys are truly random and unpredictable.
Key Storage
Private keys are stored within the HSM’s secure boundary and never leave the device in plaintext form, protecting them from software attacks and memory dumps.
Cryptographic Operations
HSMs perform encryption, decryption, digital signing, and key derivation operations without exposing private keys to the host system.
Key Lifecycle Management
HSMs support key creation, rotation, backup, recovery, and destruction operations while maintaining security throughout the lifecycle.
Types of HSMs
Network-Attached HSMs
- Connected to networks via Ethernet
- Shared by multiple applications and servers
- Suitable for enterprise-wide key management
- Examples: Thales Luna, Utimaco CryptoServer
PCIe/Internal HSMs
- Installed directly in servers
- Lower latency for high-performance applications
- Dedicated to specific servers or applications
- Examples: Thales nShield, Utimaco CryptoServer PCIe
USB/Portable HSMs
- Portable devices connected via USB
- Suitable for development and testing
- Lower cost for smaller deployments
- Examples: YubiHSM, Nitrokey HSM
Cloud HSMs
- HSM services provided by cloud providers
- Managed HSM services (HSM-as-a-Service)
- No hardware to purchase or maintain
- Examples: AWS CloudHSM, Azure Dedicated HSM, Google Cloud HSM
HSM Security Features
Physical Security
- Tamper Detection: Sensors detect physical tampering attempts
- Tamper Response: Automatic key destruction upon tampering detection
- Hardware Security: Keys stored in secure memory that cannot be extracted
- FIPS Certification: Compliance with FIPS 140-2 security standards
Logical Security
- Access Controls: Role-based access control and authentication
- Audit Logging: Comprehensive logging of all operations
- Key Isolation: Keys are isolated and cannot be exported
- Secure APIs: Cryptographically secure interfaces
Operational Security
- High Availability: Clustering and redundancy options
- Backup and Recovery: Secure key backup mechanisms
- Performance: Hardware-accelerated cryptographic operations
- Compliance: Support for regulatory requirements
FIPS 140-2 Security Levels
HSMs are certified under FIPS 140-2 with different security levels:
- Level 1: Basic security requirements
- Level 2: Role-based authentication, tamper-evident
- Level 3: Identity-based authentication, tamper-resistant
- Level 4: Highest security, tamper-responsive, formal security models
Common Use Cases
Certificate Authority (CA) Operations
- Protecting CA private keys
- Signing digital certificates
- Maintaining certificate trust chains
Code Signing
- Securing code signing keys
- Protecting software integrity
- Preventing unauthorized code modification
Database Encryption
- Protecting database encryption keys
- Secure key management for encrypted databases
- Compliance with data protection regulations
Payment Processing
- Protecting payment card data
- PCI DSS compliance
- Secure transaction processing
Blockchain and Cryptocurrency
- Securing cryptocurrency wallets
- Protecting blockchain private keys
- Secure transaction signing
Benefits of Using HSMs
Enhanced Security
- Physical Protection: Keys protected from physical attacks
- Logical Protection: Keys protected from software attacks
- Tamper Resistance: Automatic key destruction on tampering
- Compliance: Meets regulatory and industry standards
Performance
- Hardware Acceleration: Faster cryptographic operations
- Dedicated Processing: Offloads cryptographic work from main systems
- Scalability: Can handle high-volume operations
Compliance
- FIPS 140-2: Certified security standards
- Common Criteria: International security certification
- PCI DSS: Payment card industry compliance
- eIDAS: European digital identity standards
HSM vs. Software Key Storage
| Aspect | HSM | Software Storage |
|---|---|---|
| Security | Hardware-protected | Software-protected |
| Tamper Resistance | Physical and logical | Logical only |
| Performance | Hardware-accelerated | CPU-dependent |
| Cost | Higher initial cost | Lower cost |
| Compliance | FIPS certified | May not meet requirements |
| Key Extraction | Extremely difficult | Possible with access |
Best Practices
1. Choose the Right HSM
- Evaluate security requirements (FIPS level)
- Consider performance needs
- Assess integration requirements
- Review compliance certifications
2. Implement Proper Access Controls
- Use role-based access control
- Implement multi-factor authentication
- Separate administrative and operational roles
- Regular access reviews
3. Secure HSM Deployment
- Physically secure HSM devices
- Use secure network connections
- Implement proper backup procedures
- Regular security updates
4. Monitor and Audit
- Enable comprehensive audit logging
- Monitor HSM operations
- Regular security assessments
- Incident response procedures
5. Plan for Disaster Recovery
- Secure key backup procedures
- Test recovery processes
- Maintain HSM redundancy
- Document procedures
Cloud HSM Services
Cloud providers offer managed HSM services:
- AWS CloudHSM: Dedicated HSM instances in AWS
- Azure Dedicated HSM: FIPS 140-2 Level 3 HSMs in Azure
- Google Cloud HSM: Managed HSM service
- HSM-as-a-Service: Fully managed HSM solutions
Conclusion
Hardware Security Modules are essential for protecting critical cryptographic keys in enterprise environments. By providing physical and logical security, HSMs enable organizations to meet compliance requirements, protect sensitive data, and maintain the highest levels of security for cryptographic operations.
Need HSM solutions? Contact our experts to learn about HSM deployment and management services.
Ready to Secure Your Enterprise?
Discover how QCecuring can help you automate certificate lifecycle management, secure SSH keys, and protect your cryptographic infrastructure.