Understand why SSH key protection is critical for enterprise security and learn best practices for securing SSH keys.
What is the Need for SSH Keys Protection?
SSH (Secure Shell) keys are fundamental to secure server access and automation, but they represent a significant security risk if not properly protected. Understanding why SSH key protection is essential helps organizations implement effective security measures.
The Critical Importance of SSH Key Protection
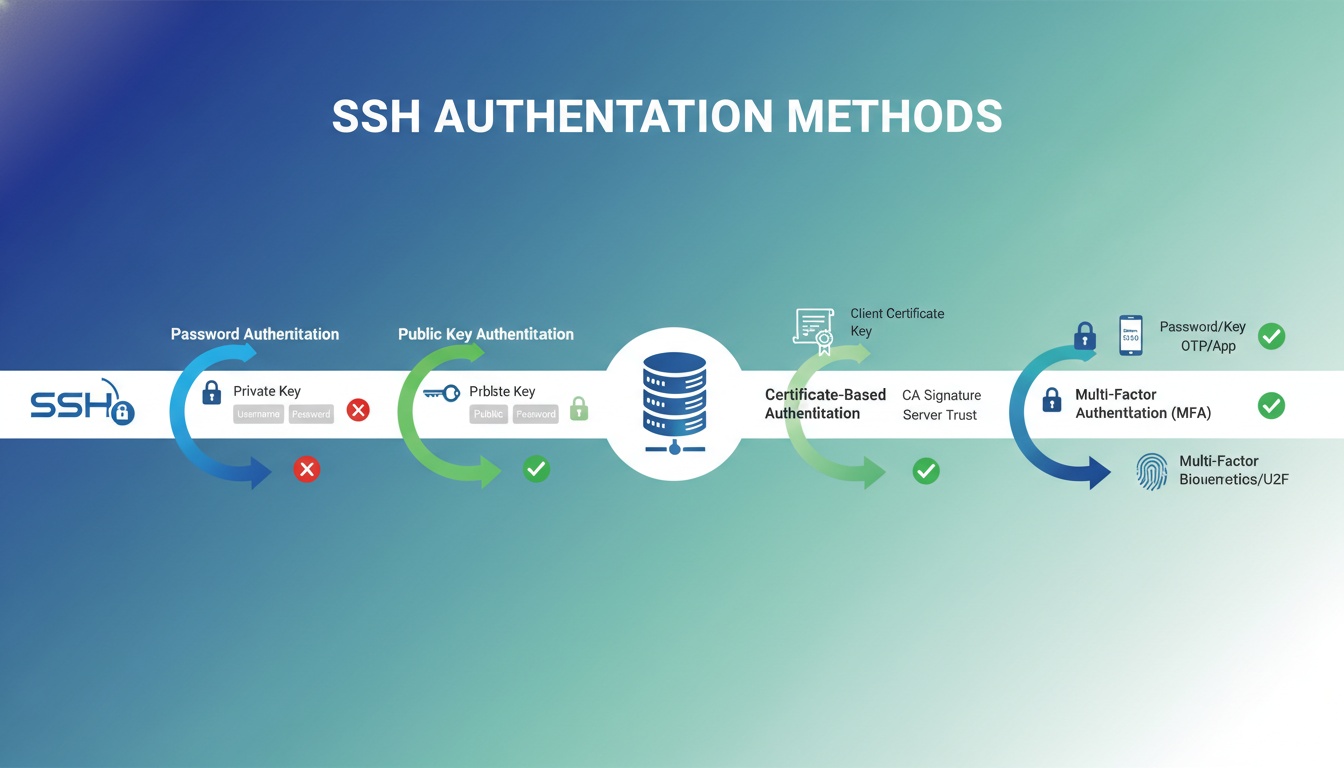
SSH keys provide passwordless authentication to servers, systems, and services. If compromised, they grant attackers immediate access to critical infrastructure without needing passwords or additional authentication.
Why SSH Keys Need Protection
1. Privileged Access
SSH keys often provide root or administrative access to systems, making them high-value targets for attackers. A single compromised key can lead to:
- Complete System Compromise: Full control over servers and infrastructure
- Data Breaches: Access to sensitive data and databases
- Lateral Movement: Ability to move between systems and networks
- Persistent Access: Long-term unauthorized access even after passwords change
2. Widespread Use
SSH keys are used extensively across modern IT environments:
- Server Access: System administrators use SSH keys for server management
- Automation: CI/CD pipelines and scripts rely on SSH keys
- Cloud Services: Cloud instances and containers use SSH keys
- Git Operations: Version control systems authenticate via SSH keys
3. Long-Lived Credentials
Unlike passwords that can be changed regularly, SSH keys often remain valid for months or years, making them attractive targets for persistent attacks.
4. Lack of Visibility
Many organizations don’t know:
- How many SSH keys exist in their environment
- Where SSH keys are stored
- Who has access to which keys
- Which keys are still in use
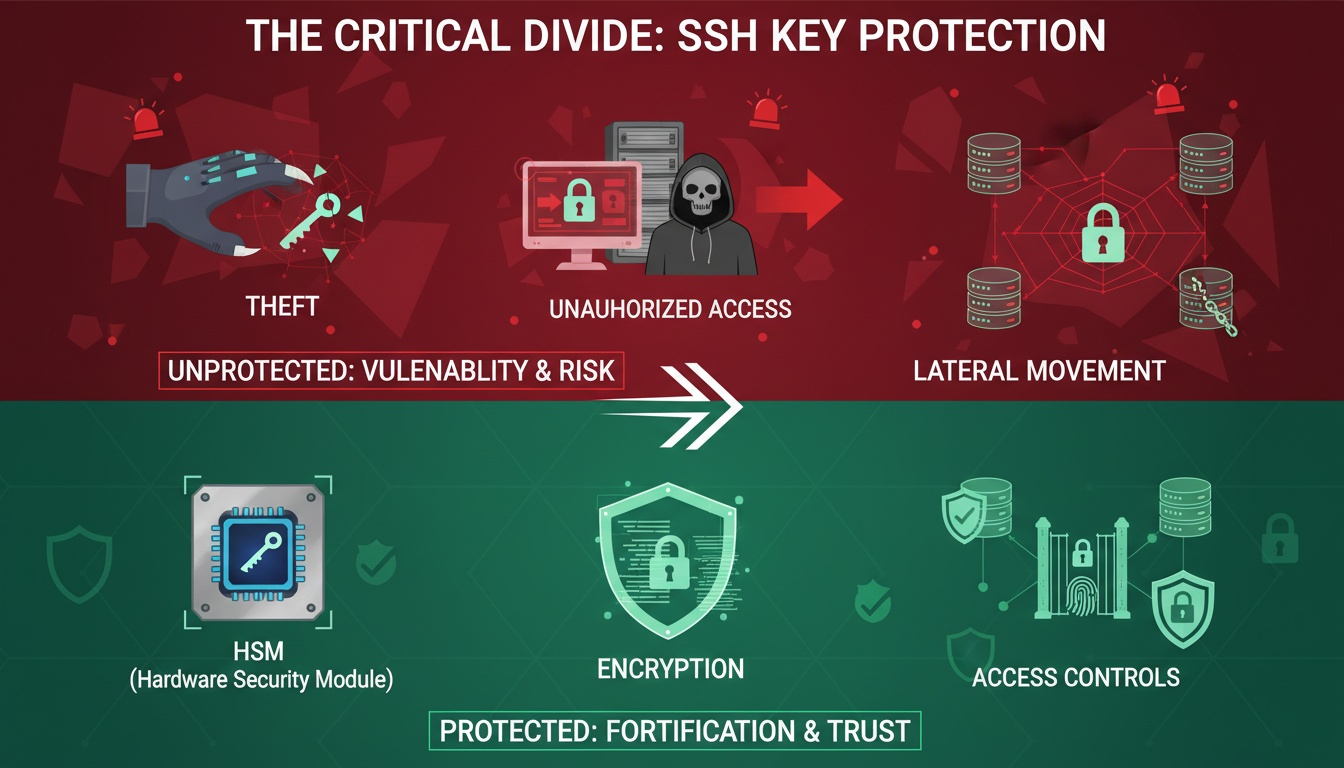
Common SSH Key Security Risks
Unprotected Private Keys
- Unencrypted Storage: Private keys stored without passphrase protection
- Insecure Locations: Keys stored in plain text files or shared storage
- Weak Permissions: Keys with overly permissive file permissions
- Version Control: Keys accidentally committed to Git repositories
Key Proliferation
- Orphaned Keys: Keys from former employees still active
- Duplicate Keys: Same key used across multiple systems
- Unmanaged Keys: Keys created without proper tracking or rotation
Insufficient Access Controls
- Overly Permissive Keys: Keys with more access than necessary
- Shared Keys: Multiple users sharing the same key
- No Audit Trail: No logging of key usage or access
Consequences of SSH Key Compromise
Immediate Impact
- Unauthorized Access: Attackers gain immediate system access
- Data Theft: Sensitive information can be exfiltrated
- Service Disruption: Systems can be modified or destroyed
Long-Term Impact
- Persistent Backdoors: Attackers maintain access even after detection
- Compliance Violations: Regulatory penalties and audit failures
- Reputation Damage: Loss of customer trust and business impact
- Financial Loss: Costs of incident response and remediation
Best Practices for SSH Key Protection
1. Encrypt Private Keys
Always use passphrase-protected private keys:
ssh-keygen -t ed25519 -C "your_email@example.com" -f ~/.ssh/id_ed255192. Implement Key Rotation
- Rotate SSH keys regularly (every 90-180 days)
- Immediately rotate keys after employee departure
- Rotate keys after suspected compromise
3. Centralized Key Management
- Use SSH key management platforms
- Maintain inventory of all SSH keys
- Track key ownership and usage
- Automate key rotation and revocation
4. Enforce Access Controls
- Implement least privilege principles
- Use separate keys for different purposes
- Restrict key usage to specific hosts or commands
- Monitor and audit key usage
5. Secure Key Storage
- Store private keys in secure locations
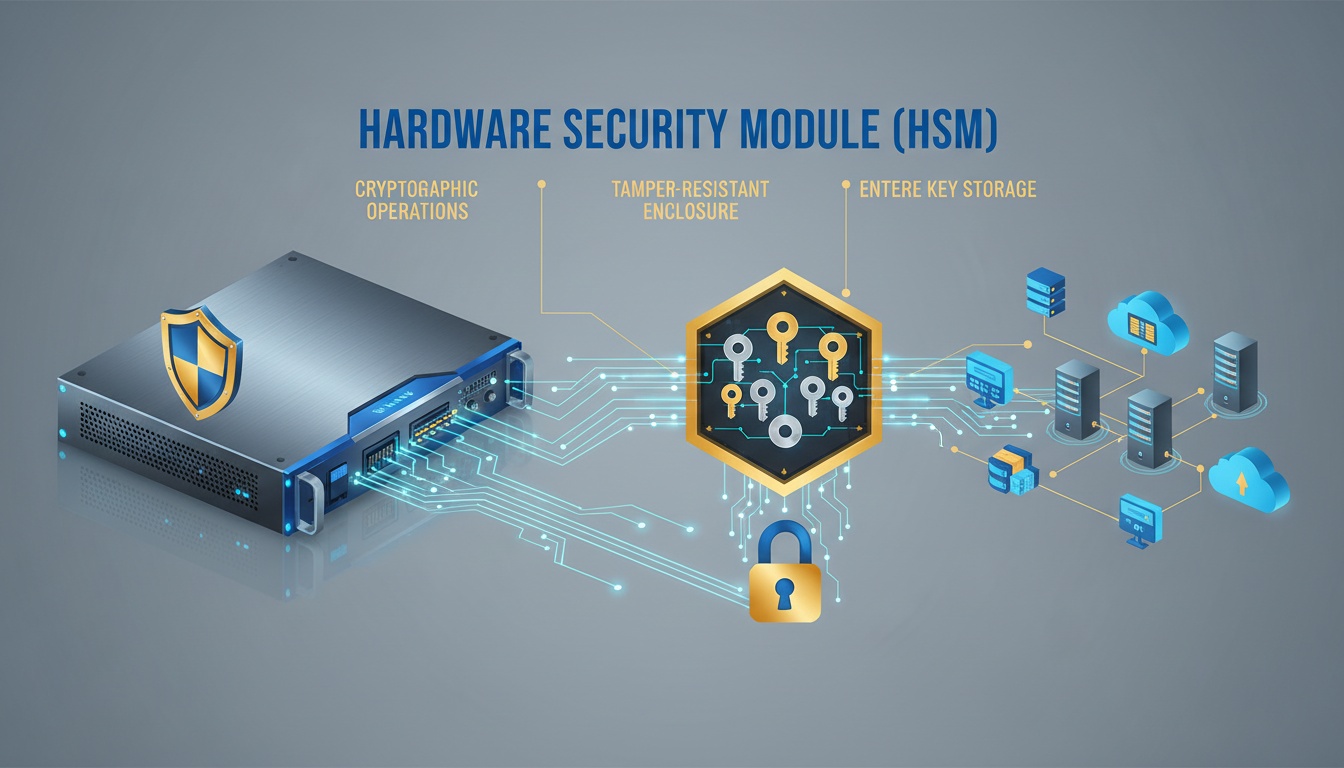
- Use Hardware Security Modules (HSMs) for critical keys
- Implement proper file permissions (600 for private keys)
- Never store keys in version control
6. Monitor and Audit
- Log all SSH key usage
- Monitor for suspicious access patterns
- Regular audits of SSH key inventory
- Alert on unauthorized key usage
SSH Key Management Solutions
Manual Management
- Basic key generation and distribution
- Manual rotation and revocation
- Limited visibility and control
Centralized Management Platforms
- Automated key lifecycle management
- Comprehensive visibility and auditing
- Integration with identity systems
- Policy enforcement and compliance
Compliance and Regulatory Requirements
Many regulations require SSH key protection:
- PCI DSS: Requires strong access controls and key management
- HIPAA: Mandates protection of access credentials
- SOC 2: Requires secure key management practices
- ISO 27001: Specifies cryptographic key management controls
Conclusion
SSH key protection is not optional—it’s a critical security requirement. Organizations must implement comprehensive SSH key management practices to protect against unauthorized access, data breaches, and compliance violations. By understanding the risks and implementing best practices, organizations can significantly improve their security posture.
Need help securing your SSH keys? Contact our security experts to learn about enterprise SSH key management solutions.
Ready to Secure Your Enterprise?
Discover how QCecuring can help you automate certificate lifecycle management, secure SSH keys, and protect your cryptographic infrastructure.