Learn about public-key cryptography, how it differs from symmetric encryption, and its role in modern security systems.
What is Public-key Cryptography?
Public-key cryptography, also known as asymmetric cryptography, is a cryptographic system that uses pairs of keys: a public key that can be shared openly and a private key that must be kept secret. This fundamental technology enables secure communication without requiring parties to share a secret key in advance.
Understanding Public-key Cryptography
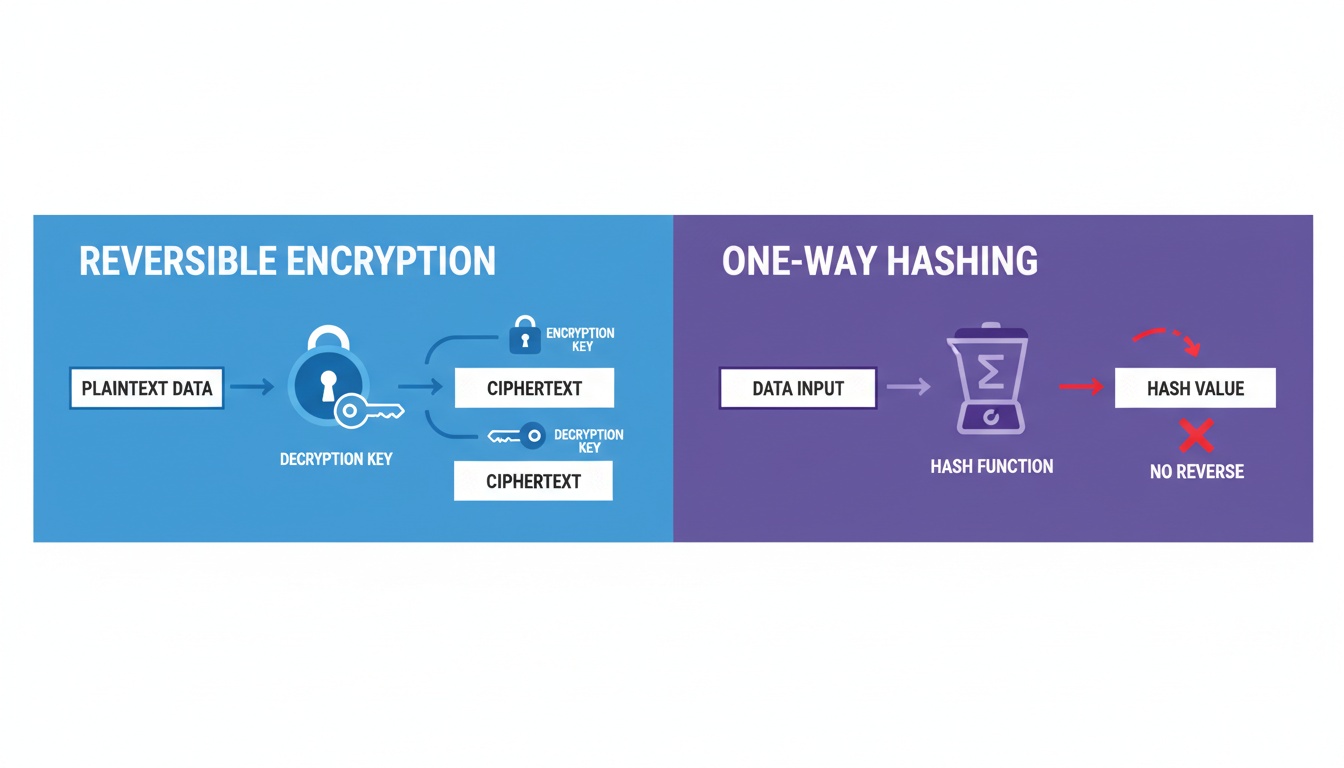
Unlike symmetric cryptography where the same key is used for both encryption and decryption, public-key cryptography uses two mathematically related keys:
- Public Key: Can be freely distributed and is used to encrypt data or verify signatures
- Private Key: Must be kept secret and is used to decrypt data or create signatures
How It Works
Encryption Process
- Key Generation: A user generates a public-private key pair
- Public Key Distribution: The public key is shared with anyone who needs to send encrypted messages
- Encryption: The sender uses the recipient’s public key to encrypt the message
- Decryption: Only the recipient, with their private key, can decrypt the message
Digital Signatures
- Signing: The sender uses their private key to create a digital signature
- Verification: Anyone with the sender’s public key can verify the signature’s authenticity
- Integrity: The signature proves the message hasn’t been tampered with
Key Properties
Confidentiality
Data encrypted with a public key can only be decrypted with the corresponding private key, ensuring only the intended recipient can read it.
Authentication
Digital signatures created with a private key can be verified with the corresponding public key, proving the sender’s identity.
Non-Repudiation
Once a message is signed with a private key, the sender cannot deny having sent it, as only they possess that key.
Integrity
Digital signatures detect any modification to the signed data, ensuring the message hasn’t been altered.
Common Algorithms
RSA (Rivest-Shamir-Adleman)
One of the first and most widely used public-key algorithms, based on the difficulty of factoring large prime numbers.
Elliptic Curve Cryptography (ECC)
Uses the mathematics of elliptic curves to provide equivalent security with smaller key sizes, making it more efficient.
Diffie-Hellman
Enables secure key exchange over insecure channels, allowing parties to establish a shared secret.
Advantages and Disadvantages
Advantages
- No Pre-shared Secret: Parties don’t need to exchange keys beforehand
- Digital Signatures: Enables authentication and non-repudiation
- Scalability: Public keys can be freely distributed
- Key Management: Easier to manage than symmetric key systems
Disadvantages
- Performance: Slower than symmetric encryption
- Key Size: Requires larger keys for equivalent security
- Computational Cost: More resource-intensive operations
Real-World Applications
- TLS/SSL: Securing web communications
- Email Encryption: PGP and S/MIME
- Digital Certificates: PKI and certificate-based authentication
- Blockchain: Cryptocurrency transactions and smart contracts
- SSH: Secure remote access and authentication
Public-key vs. Symmetric Cryptography
In practice, most systems use a hybrid approach:
- Public-key cryptography for key exchange and digital signatures
- Symmetric cryptography for bulk data encryption (faster and more efficient)
This combination provides both security and performance benefits.
Conclusion
Public-key cryptography is a foundational technology that enables secure communication, digital signatures, and trust in digital systems. Understanding its principles is essential for anyone working with modern cybersecurity and encryption technologies.
Want to learn more? Explore our guides on PKI and symmetric vs asymmetric encryption.
Ready to Secure Your Enterprise?
Discover how QCecuring can help you automate certificate lifecycle management, secure SSH keys, and protect your cryptographic infrastructure.